Personal identification information identification system and method in high-performance ip network
A technology for identifying information and identification methods, which is applied in the fields of network information and security and network personal privacy protection, can solve the problems of large computing costs, and achieve the effects of large coverage area, strong operability, and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
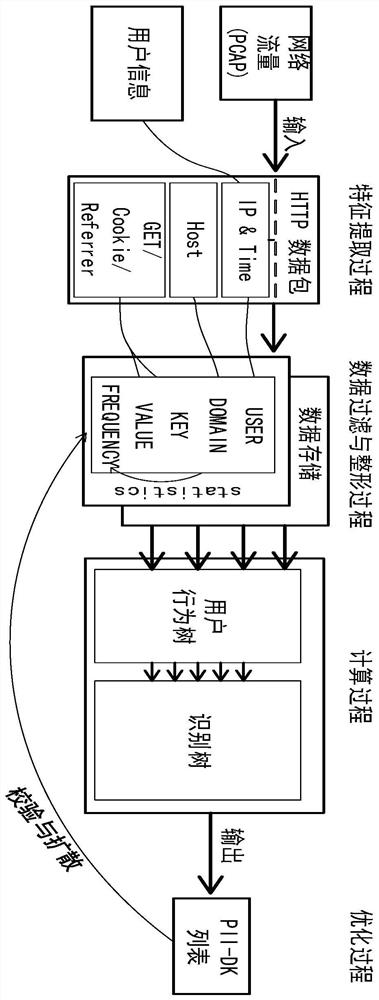
[0068]This embodiment describes in detail the overall system structure diagram of a personal identification information identification system in an operator network of the present invention. Fromfigure 1 It can be seen that the network traffic is first input to the system in the PCAP format; secondly, the data packet is associated with the user (object) in the authentication system using the timestamp and IP address; again, the system uses regular expressions to extract the network traffic in the feature extraction process The HOST field and GET field of the HTTP data packet are extracted, and the characteristics are extracted according to the method in step 2 and then stored as a record (see Example 2 for details); then, the system statistics (statistics) the same records and aggregates, the same records The frequency of occurrence is FREQUENCY; finally a five-dimensional field data set {USER,DOMAIN,KEY,VALUE, FREQUENCY} is obtained. The system here uses the MAC address to represen...
Embodiment 2
[0074]This embodiment describes in detail the feature extraction process of a personal identification information recognition system in an operator network of the present invention. The feature extraction location map represents an HTTP data packet header field in actual network traffic. According to the prompt in step 2, the method extracts the string "mcgi.v.qq.com" in the HOST field and writes it into the DOMAIN field of the data set, and extracts 13 strings such as "app_id", "imsi" and "imei" to write data KEY field, and write 13 strings such as "248", "460023918121329" and "868129022933673" into the VALUE field corresponding to the data set, and finally write 13 records in the data set. See the feature extraction result table below for details.
[0075]Feature extraction location chart
[0076]
[0077]Feature extraction result table
[0078] DOMAIN KEY VALUE mcgi.v.qq.com cmd 51 mcgi.v.qq.com app_version_name 6.5.3 mcgi.v.qq.com app_version_build 0 mcgi.v.qq.com so_name p2p mcgi.v.qq...
Embodiment 3
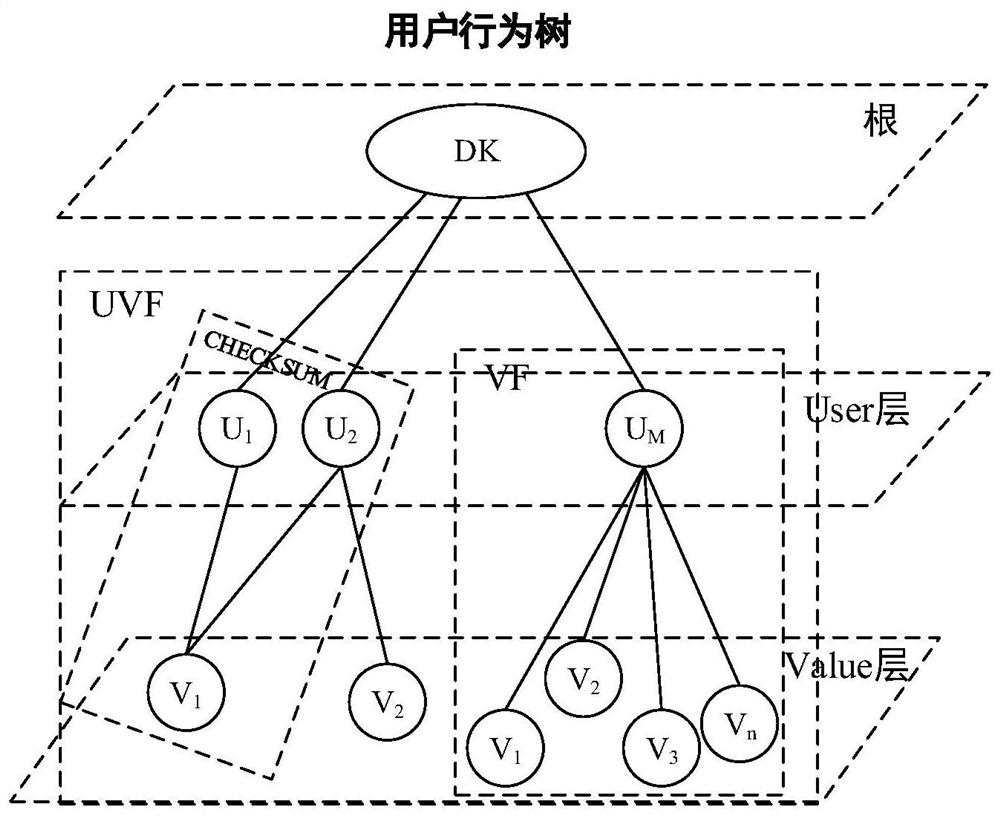
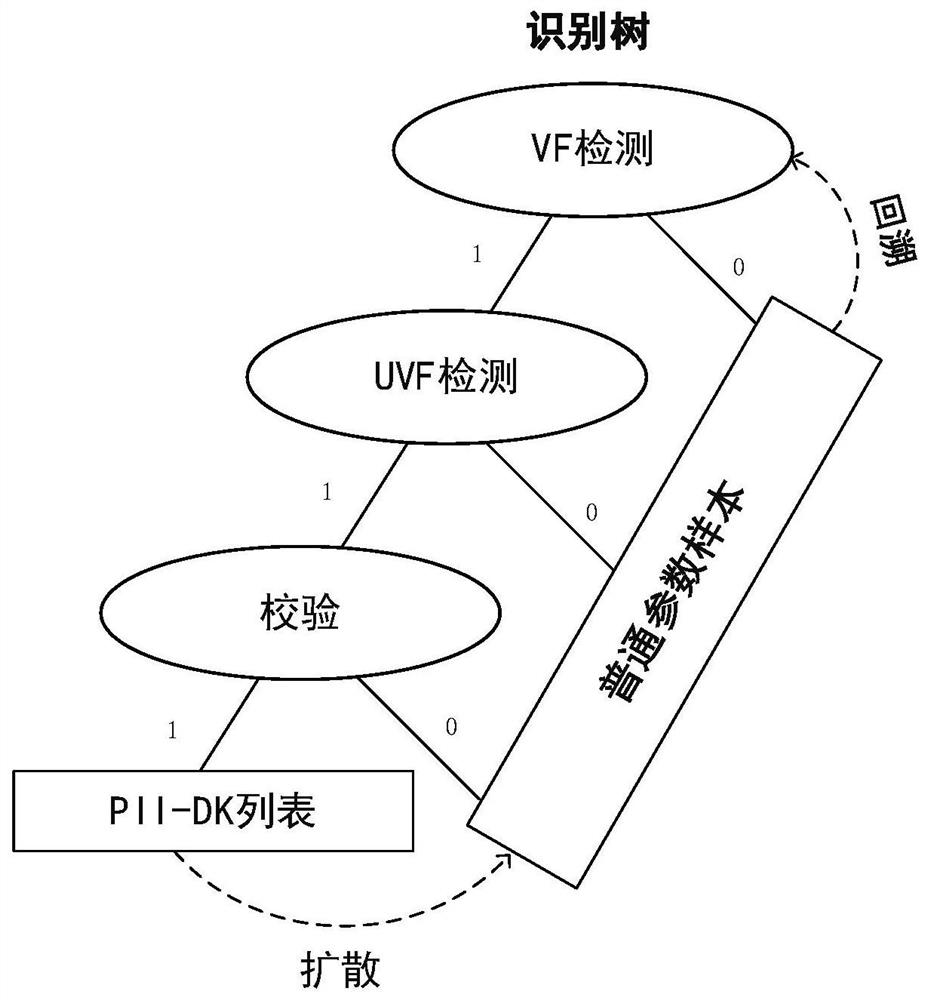
[0080]This embodiment describes in detail the process of establishing a user behavior tree in the calculation process of a personal identification information recognition system in an operator network of the present invention. Fromfigure 2 It can be seen that according to the behavior of users accessing network resources, the five-dimensional data obtained in the previous process is used to construct a user behavior tree. The five fields of the five-dimensional data can more accurately represent the user's behavior in accessing network resources. When the user or object USER accesses the network resource DOMAIN, the VALUE of FREQUENCY times is transmitted at the location KEY. According to user access behavior, the method aggregates users who access the same network resources to construct a user behavior tree. The user behavior tree is fixed to 4 levels, with DOMAIN-KEY as the root of the user behavior tree; the second level is the USER level, which means USER data with the same DOMA...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com