Systems and methods for security breach detection in vehicle communication systems
A vulnerability and security technology, applied in the direction of vehicle wireless communication service, anti-theft vehicle accessories, wireless communication, etc., can solve the problems of impossible, difficult DMO output, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
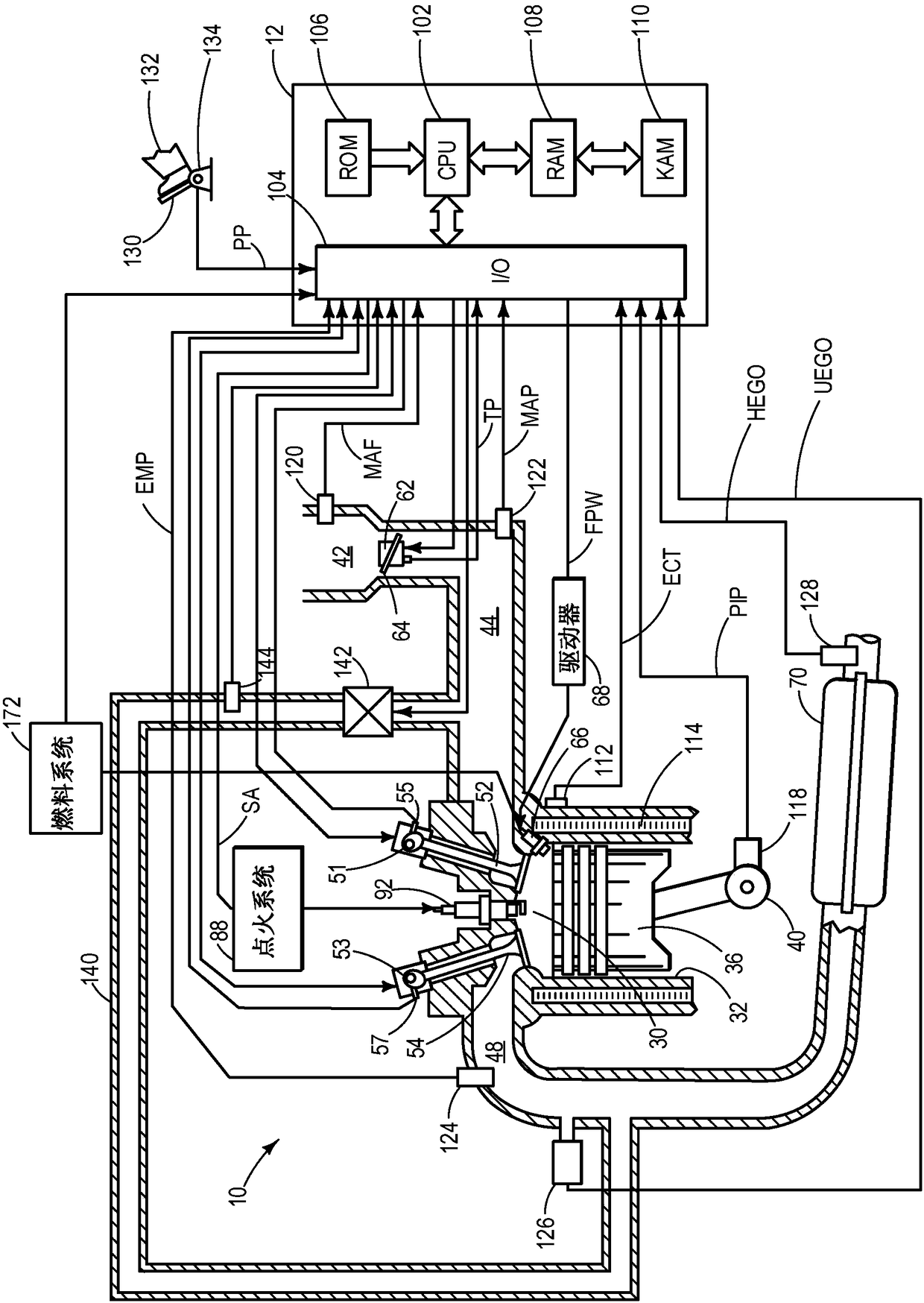
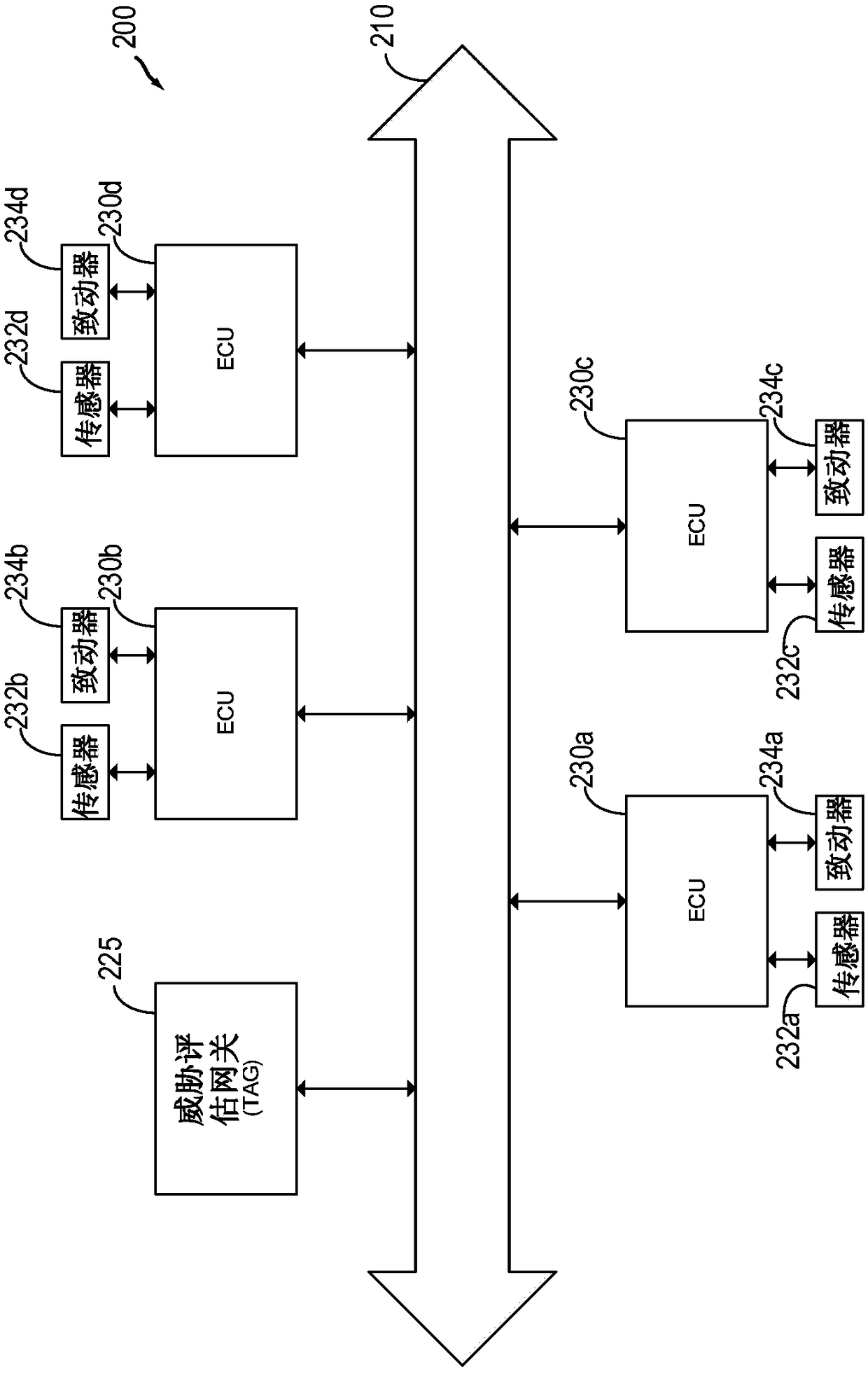
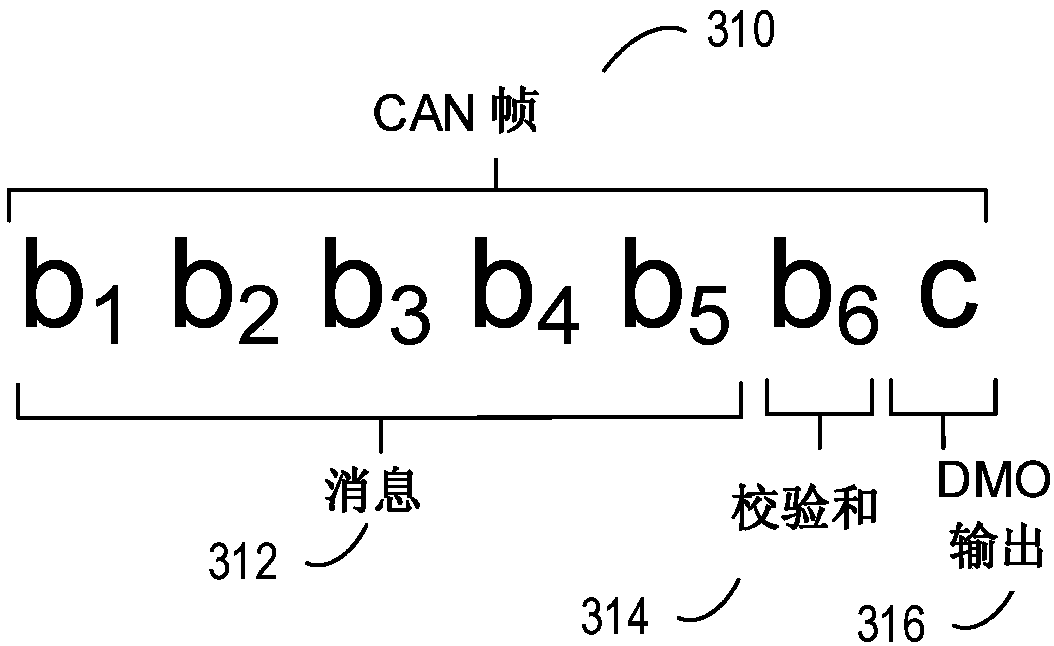
[0014] The following description relates to systems and methods for determining the presence of hacking or malicious interference in a communication system in a vehicle. in figure 1 Shown in is a vehicle engine system, which may include sensors and actuators communicatively coupled to an ECU, which communicates / communicates with a CAN bus including a Threat Assessment Gateway (TAG). in figure 2 The CAN bus is described in, which includes related CAN nodes such as TAG and various ECUs. Communication on the CAN bus can be via such as Figure 3A The CAN frame described in the CAN frame may include a checksum and DMO according to the present disclosure, such as Figure 3B Those described in. according to Figure 4 The method shown in can use DMO to detect the existence of hacking, or to distinguish hacking and transmission errors. according to Figure 5 The method shown in can also use engine operating parameters and other considerations to help distinguish between errors caused ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com