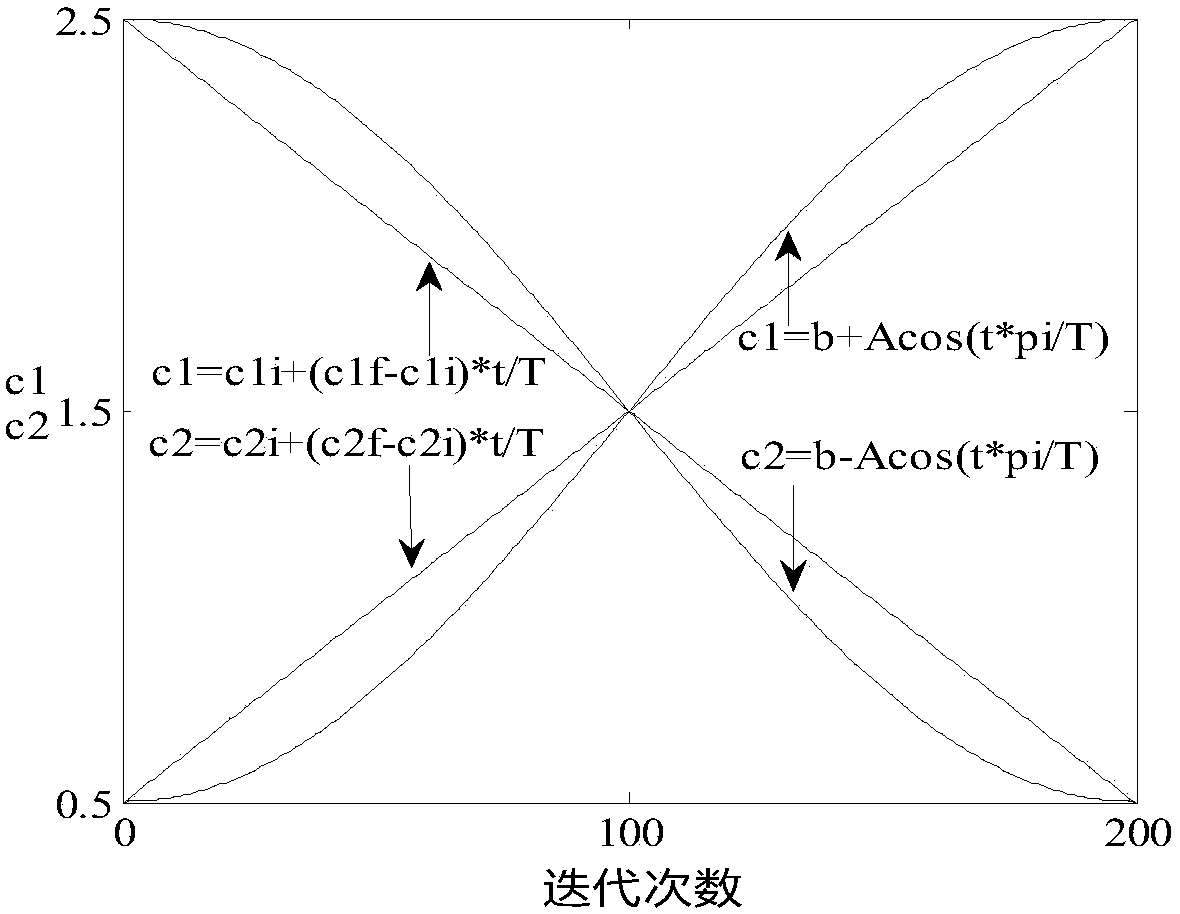
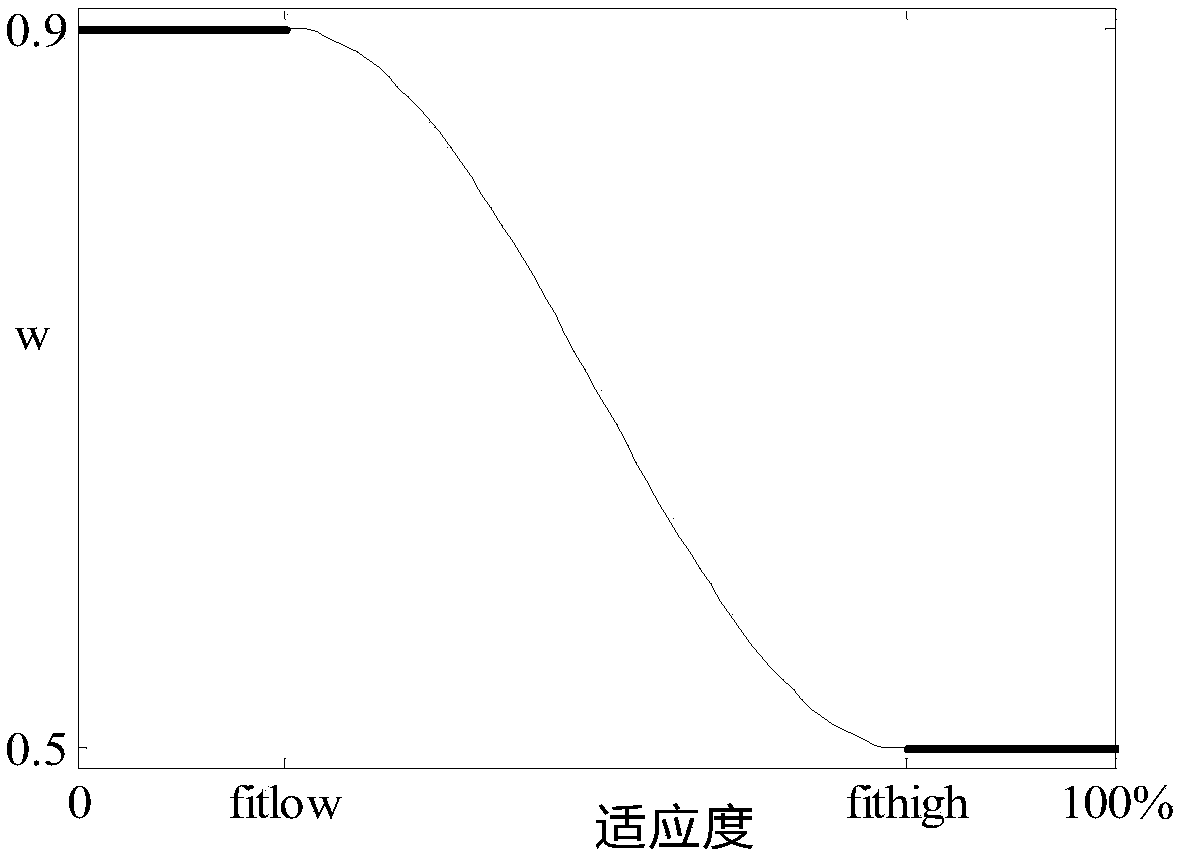
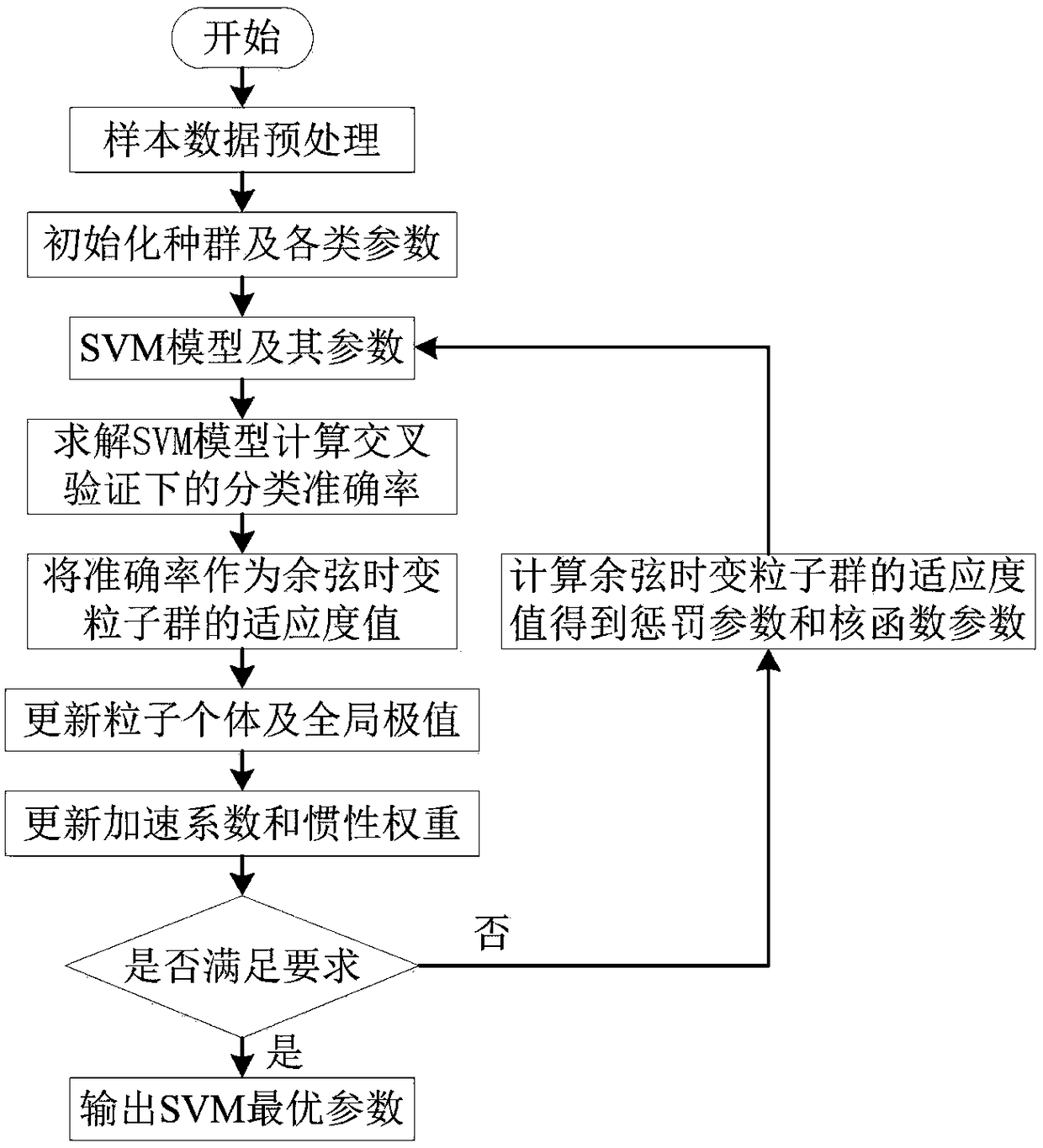
Intrusion detection method of cosine time-variant PSO-SVM
An intrusion detection and cosine technology, applied in the field of network information security, can solve the problems of PSO algorithm's local optimal search ability, particle imbalance, high false alarm rate, etc., to improve learning ability, increase detection rate, and good search ability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] Step 1: Numericalization and normalization in data preprocessing.
[0044] The NSL-KDD data set contains the basic characteristics of TCP connections, the content characteristics of TCP connections, time-based network traffic statistics and host-based network traffic statistics. Among them, there are 39 types of abnormal attacks in four categories: DOS, R2L, U2R, and PROBING. Normal is marked as 0, PROBING is marked as 1, DOS is marked as 2, and U2R is marked as 3; for the protocol type, 1 is icmp, 2 is tcp, 3 is udp, and 4 is others. For the ADFA data set, it is divided into Normal (Training and Validation) and Attack, and the Normal is marked as 1, and the Attack is marked as 2. At the same time, in order to reduce the interaction between different features, so that the importance of each feature is not affected by the value, the value is normalized, and the Min-Max standardization method is used to make it belong to [0,1]. The formula is as follows:
[0045]
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com