Risk model training method, risk identification method, device, equipment and medium
A technology of risk model and training method, which is applied in data processing applications, forecasting, instruments, etc., can solve the problems of low identification efficiency and low accuracy of risk model, and achieve better results, high accuracy, and improved accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
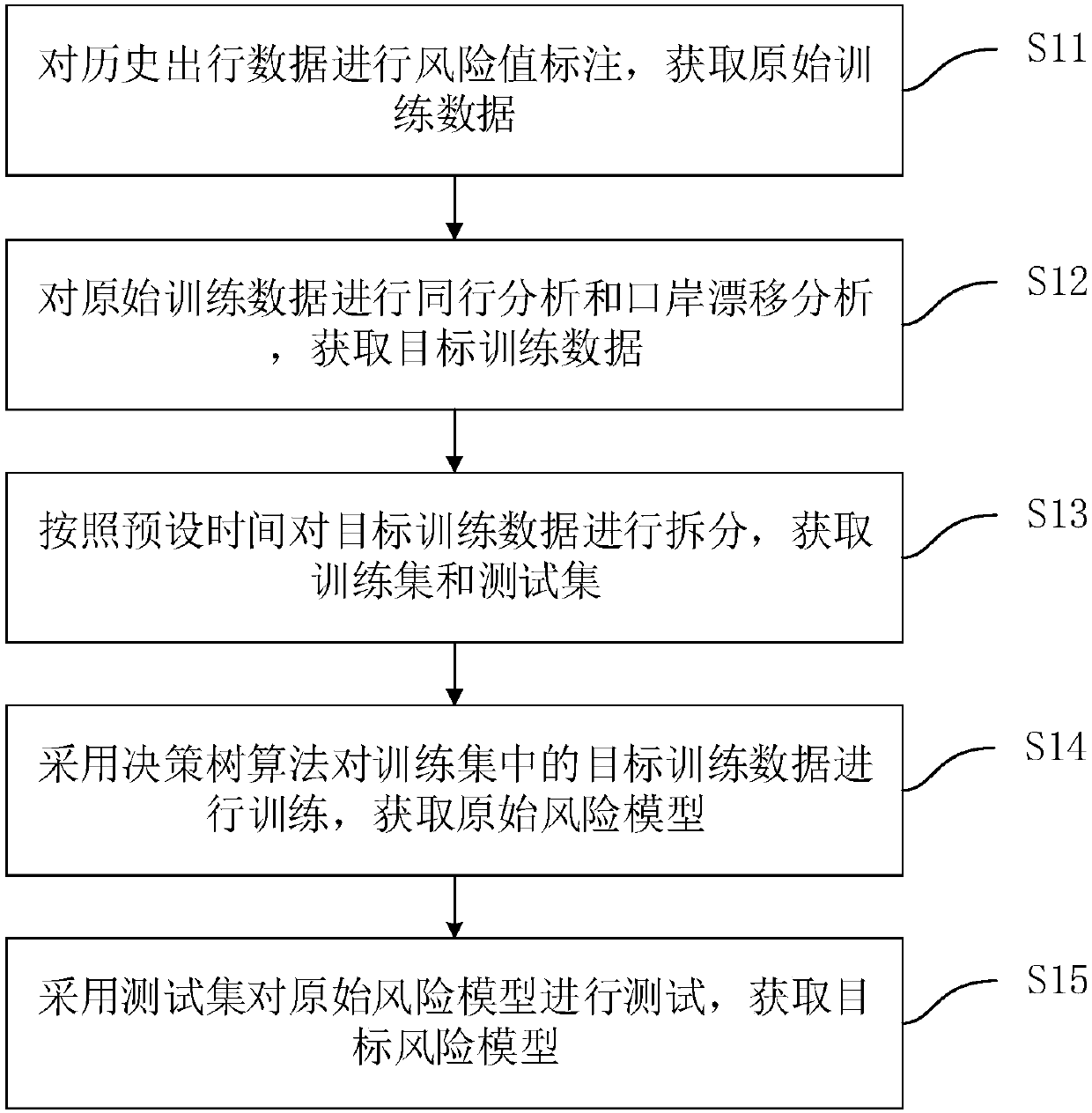
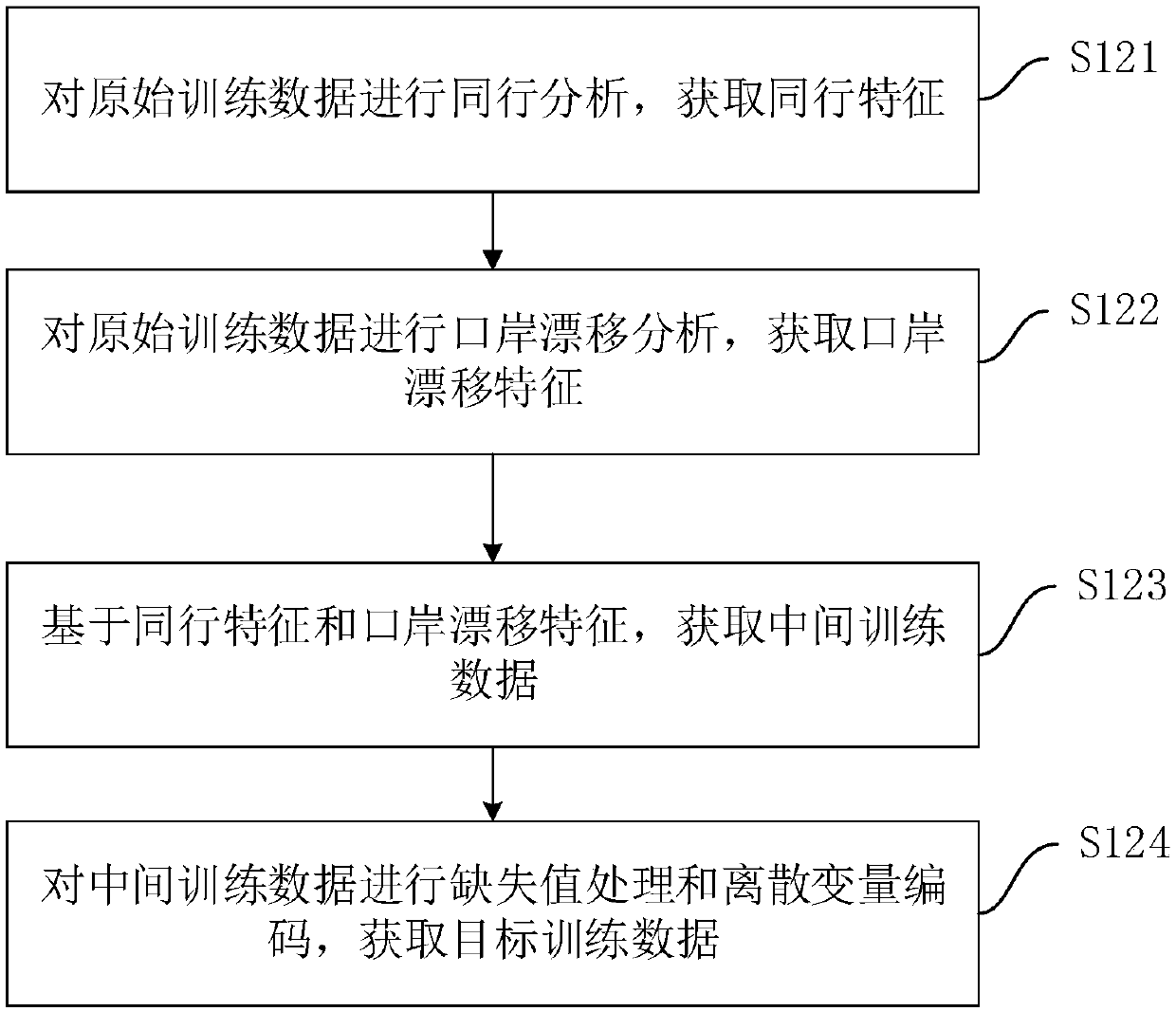
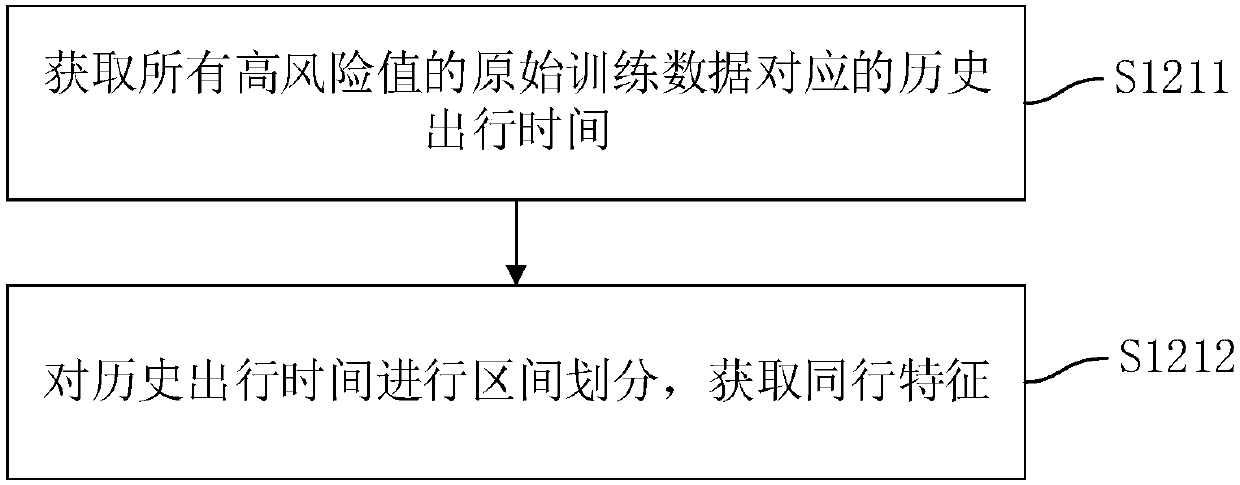
[0040] figure 1 A flow chart of the risk model training method in this embodiment is shown. The risk model training method can be applied to the computer equipment of the judiciary or other institutions, so that the trained risk model can be used to identify the transport objects (such as passengers) on the means of transport, which can effectively assist the business side in analyzing the risks of the transport objects Level to ensure the safety of other transport objects on the means of transport. like figure 1 As shown, the risk model training method includes the following steps:
[0041] S11: Mark the risk value of the historical travel data to obtain the original training data.
[0042] Wherein, the historical travel data is the travel data of the transportation object obtained from the business party. The historical travel data includes but is not limited to travel time, gender, age, inspection status and travel location, etc. The original training data is the train...
Embodiment 2
[0092] Image 6 A functional block diagram of a risk model training device corresponding to the risk model training method in Embodiment 1 is shown. like Image 6 As shown, the risk model training device includes an original training data acquisition module 11 , a target training data acquisition module 12 , a target training data division module 13 , an original risk model acquisition module 14 and a target risk model acquisition module 15 . Among them, the original training data acquisition module 11, the target training data acquisition module 12, the target training data division module 13, the original risk model acquisition module 14 and the target risk model acquisition module 15 realize the functions corresponding to the steps of the risk model training method in the embodiment One-to-one correspondence, in order to avoid redundant description, this embodiment does not describe in detail one by one.
[0093] The original training data acquisition module 11 is used to...
Embodiment 3
[0119] Figure 7 A flow chart of the risk identification method in this embodiment is shown. The risk identification method can be applied to the computer equipment of the judiciary or other institutions to check the historical travel data of the transportation object, so as to assist the business side in analyzing the risk level of the transportation object. like Figure 7 As shown, the risk model training method includes the following steps:
[0120] S21: Obtain travel data to be identified.
[0121] Among them, the travel data to be identified refers to the behavior data collected in real time by the transport object to identify whether there is a risk when traveling. The travel data to be identified includes, but is not limited to, the travel time, travel location, and inspection status of the transport object, and also includes the basic characteristics of the transport object itself (eg, gender and age). Specifically, the inspection situation refers to the situation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com