User identity verification and permission identification method and system
A technology of user identity and identification method, which is applied in the field based on the combination of user ID extraction and face recognition of mobile communication terminals, can solve problems such as unusable, achieve great social and economic benefits, improve mobile payment experience, and improve traffic The effect of experience and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the drawings and specific embodiments.
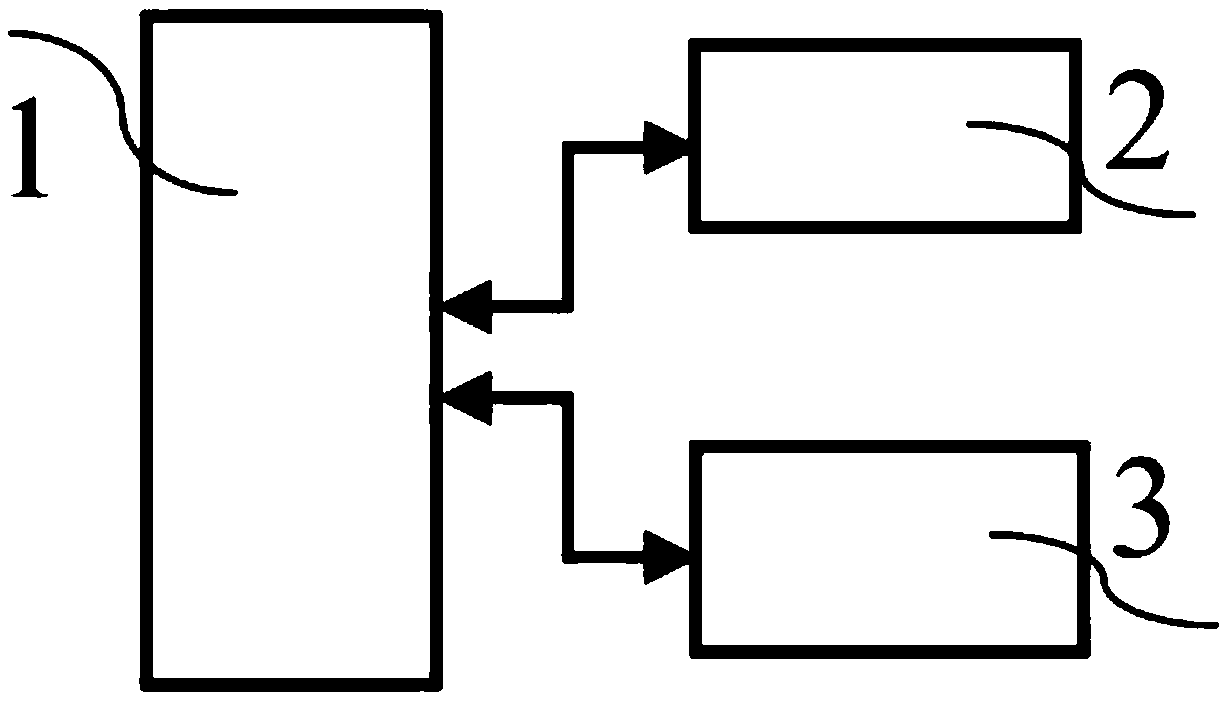
[0036] Such as figure 1 As shown, the embodiment discloses a fast, accurate and safe user identity verification and permission recognition system, including a service system, camera equipment, and mobile communication terminal perception equipment. The camera captures the face image that enters the shooting area in real time, compares the face image captured in real time with the user data in the temporary database, verifies the legitimacy of the identity of the user holding the mobile communication terminal, and when the verification is legal Send a corresponding service signal to a device that provides a specific service.
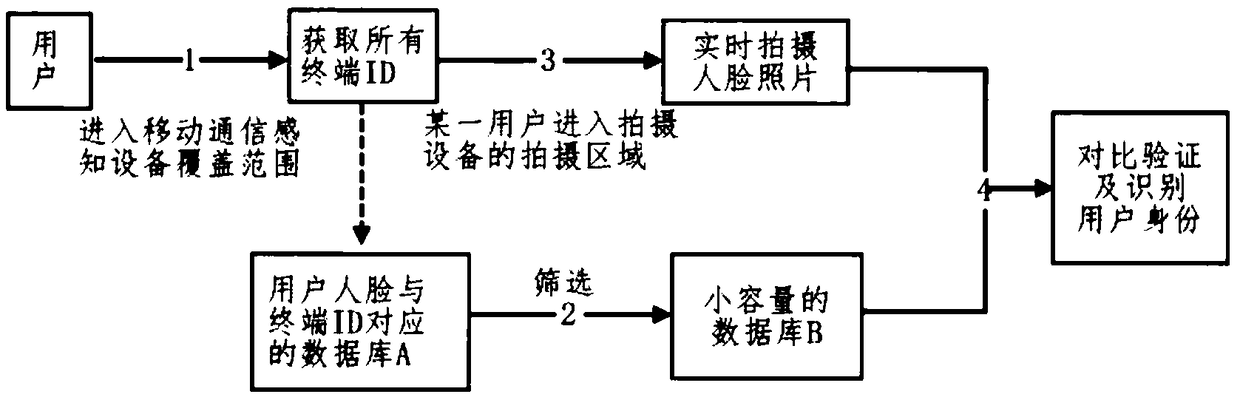
[0037] Correspondingly, such as figure 2 As shown, the embodiment also discloses a fast, accurate and safe user identity verification and permission recognition method, which establishes a safe and sound user's face image and the user's m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com