Pixel-level image authentication, tampering detection and restoration method
An image authentication and tampering detection technology, applied in image enhancement, image data processing, image data processing, etc., can solve the problem that the block-level scheme cannot locate tampered pixels, the recovery quality of non-smooth image blocks is poor, and the tampering localization ability It can improve the practicality of the technology, save the storage space, and improve the detection rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0089] The specific implementation manners of the present invention will be described below in conjunction with the accompanying drawings.
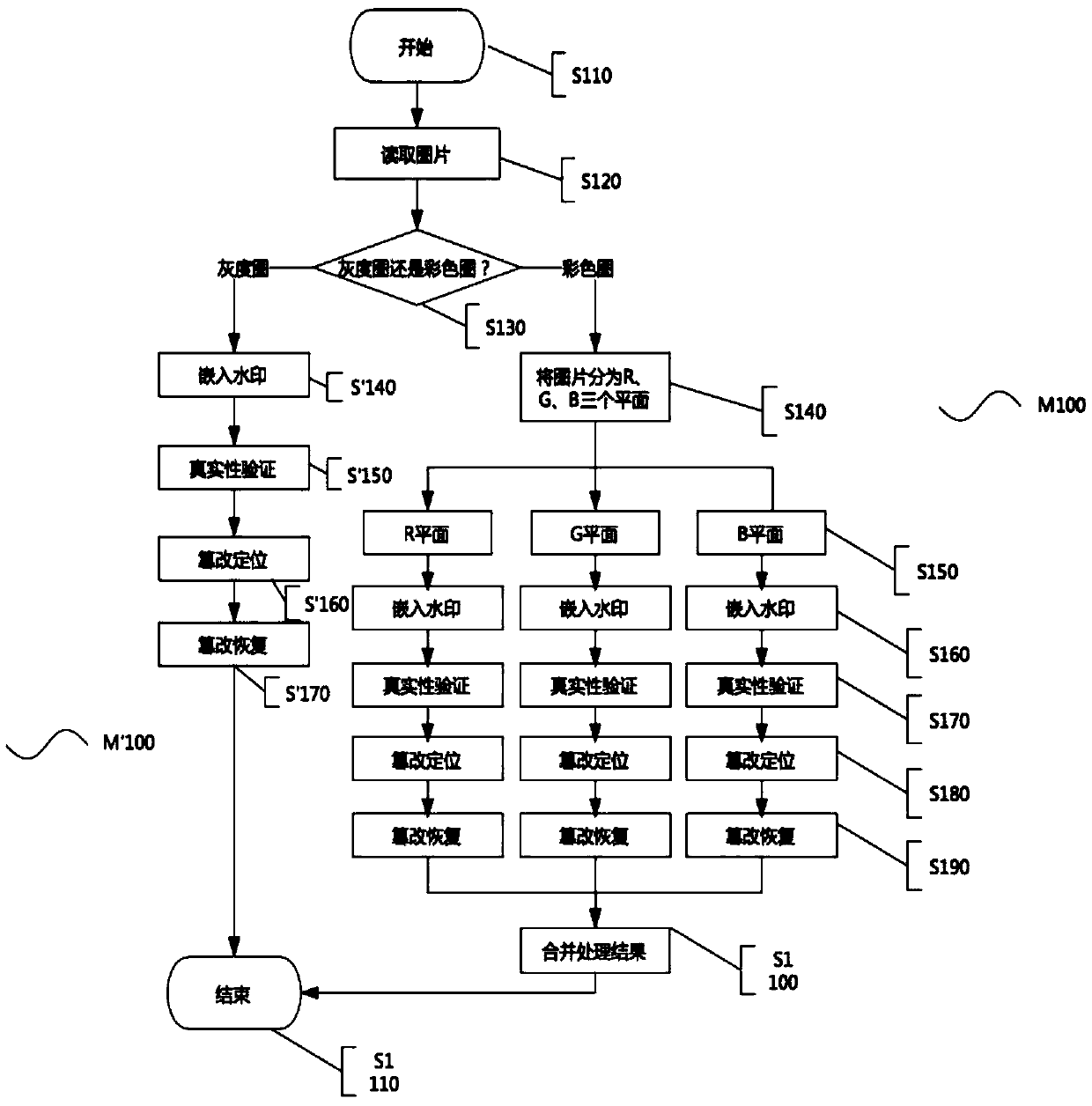
[0090] figure 1 A flow chart of processing operations on different types of pictures in the present invention is given. In the present invention, related operations can be performed on images such as gray scale images and color images, so the judgment operation can be performed on the pictures before implementing the scheme on the pictures.
[0091] Such as figure 1 As shown, the method M100 starts from step S110, step S120 reads a picture to be processed, and step S130 determines the type of the picture. If the picture belongs to the color picture, then execute step S140, divide the picture into three planes of R, G, and B, and perform the embedding watermark mentioned later on the picture in steps S150, S160, S170, S180, and S190 , authenticity verification, tampering location, tampering recovery and other operations, and finally in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com