Malware detection method based on software genetic technology
A technology of malware and detection methods, applied in the field of information security, can solve problems such as insufficient malware identification, and achieve the effect of reducing the false negative rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
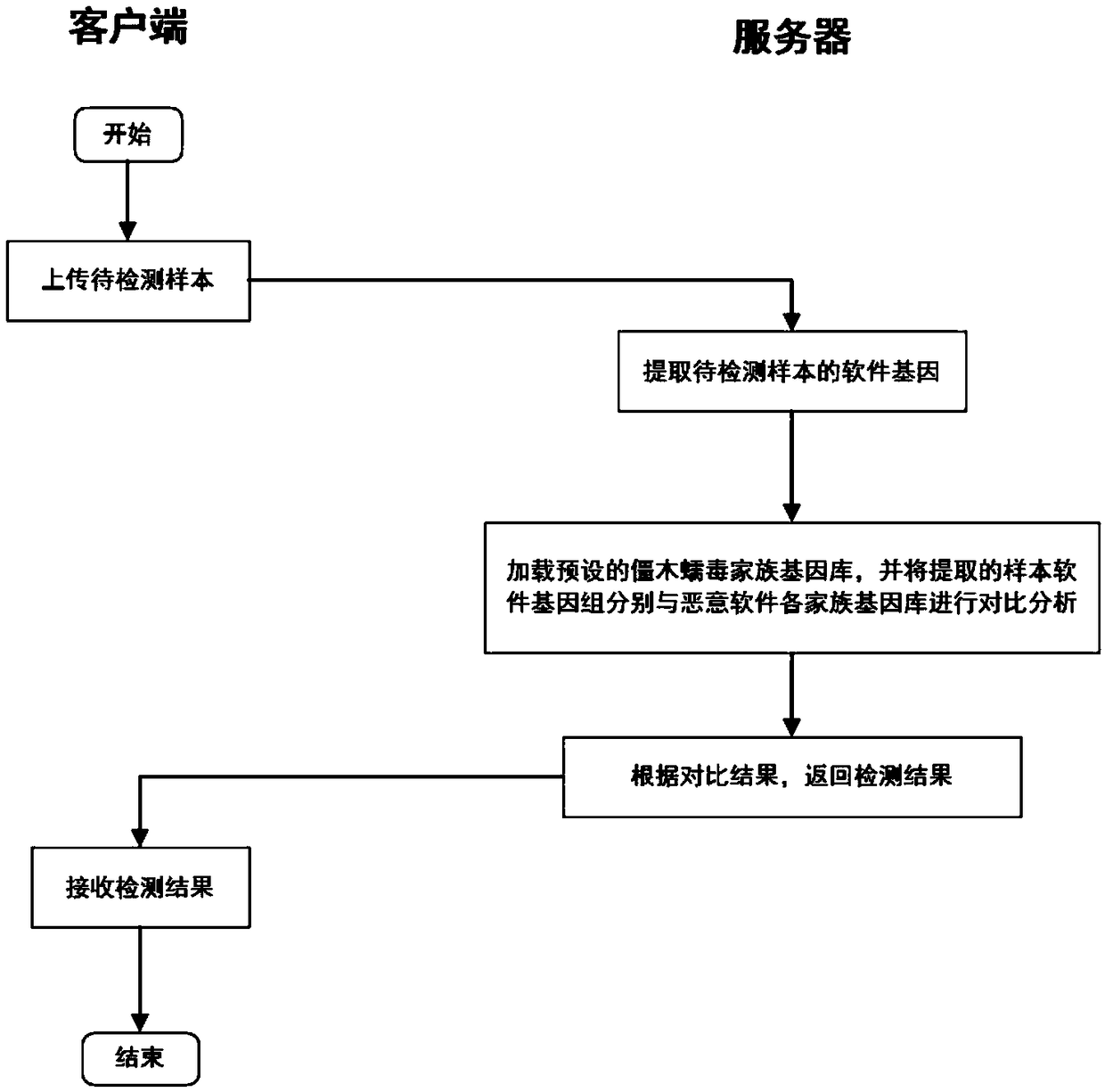
[0029] figure 1 Shown is the flow process of method provided by the present invention, and the specific embodiment of the present invention is as follows:
[0030] Step 1. On the client side, upload the local sample to be tested. Local samples to be detected may be script files, executable files, and the like.
[0031] Step 2. On the server side, perform gene extraction on the sample to be tested, including extraction of dependencies of each module and extraction of API call information, to obtain the genome of the sample to be tested.
[0032] For the extraction of the dependencies of each module, the present invention uses the Understand tool, and the Understand can automatically generate the dependency information of each module of the program, and sort out and export the data of the dependencies of each module of the generated program as CSV (Comma-Separated Values, comma-separated values) file, as part of the sample genome.
[0033] For the extraction of API call infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com