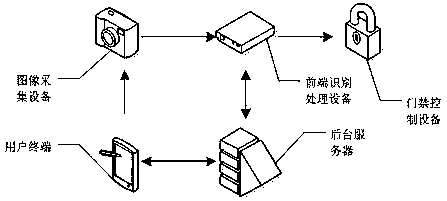
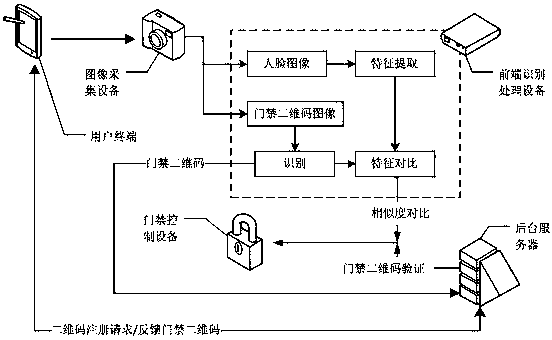
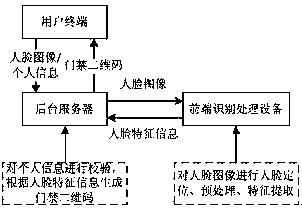
Two-dimensional code access control system based on face feature values, and running method thereof
A face feature and control system technology, applied in the field of access control based on biometrics, can solve problems such as theft of two-dimensional codes and the inability to verify the legality of the two-dimensional code holder's identity, so as to improve security and ensure convenience Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0046] The two-dimensional code registration request carries the user's face image (such as selfie, registration photo, etc.) and the user's personal information (generally including name, phone number, address, ID number); the background server verifies the personal information, The face image is also sent to the front-end recognition processing device, so that the front-end recognition processing device extracts the face feature information of the face image, specifically, the background server sends the face image to the front-end recognition processing device, and also sends the front-end recognition processing device The processing device sends an instruction to analyze the face image. After receiving the analysis instruction, the front-end recognition processing device extracts the face feature information from the face image sent by the acquired server, and sends the extracted face feature information to the background server; the background server According to the face ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com