A buffer overflow vulnerability automatic utilization method based on path analysis
A buffer overflow and path analysis technology, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve the problem of not being able to find and repair vulnerabilities in time, difficult to accurately confirm the location and type of vulnerabilities, and speed up the repair. and other problems to achieve the effect of improving vulnerability scanning performance, reducing false negative rate, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
[0035] Such as figure 1 , 2 As shown, the method for automatically exploiting buffer overflow vulnerabilities based on path analysis in this embodiment, the steps include:
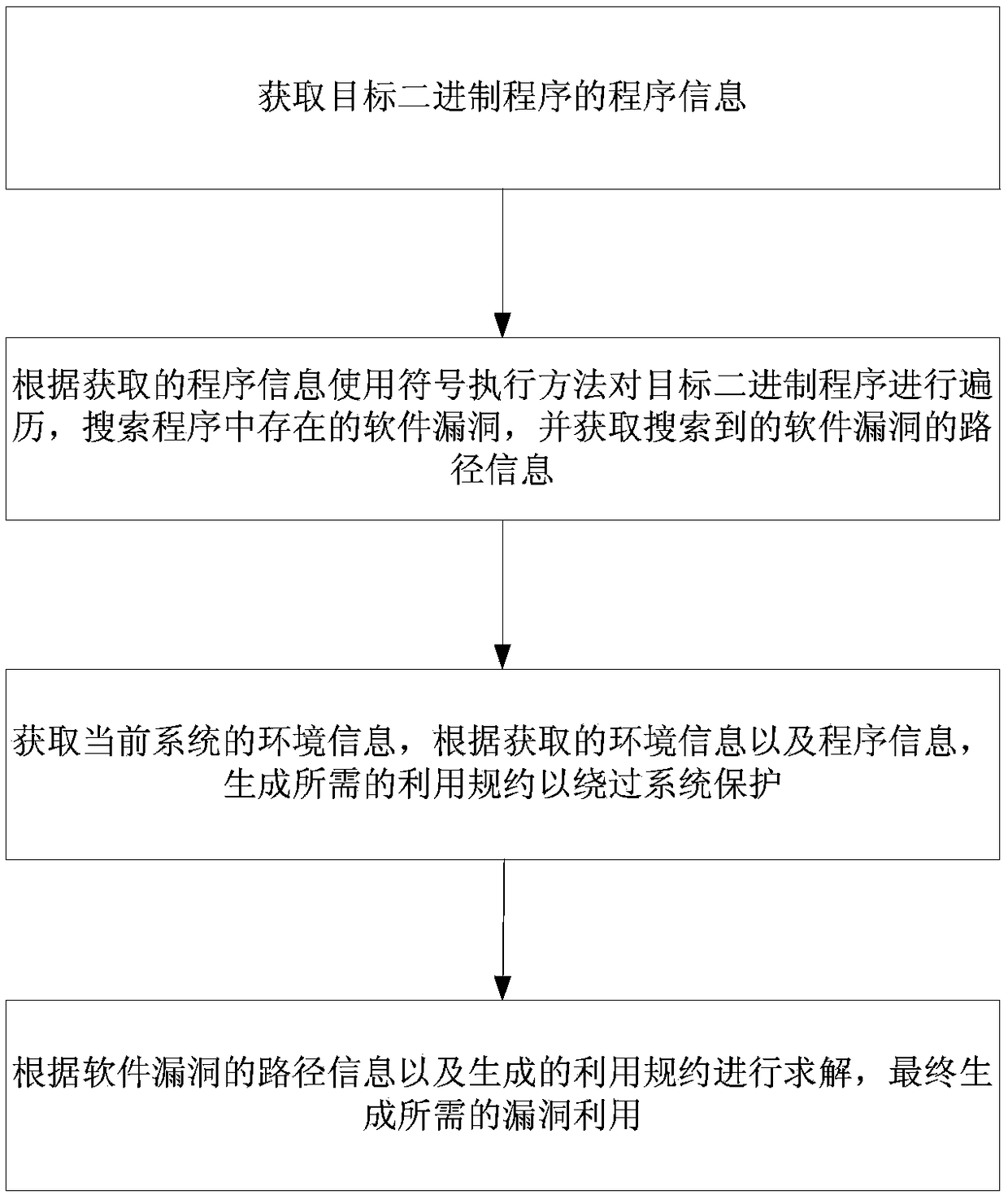
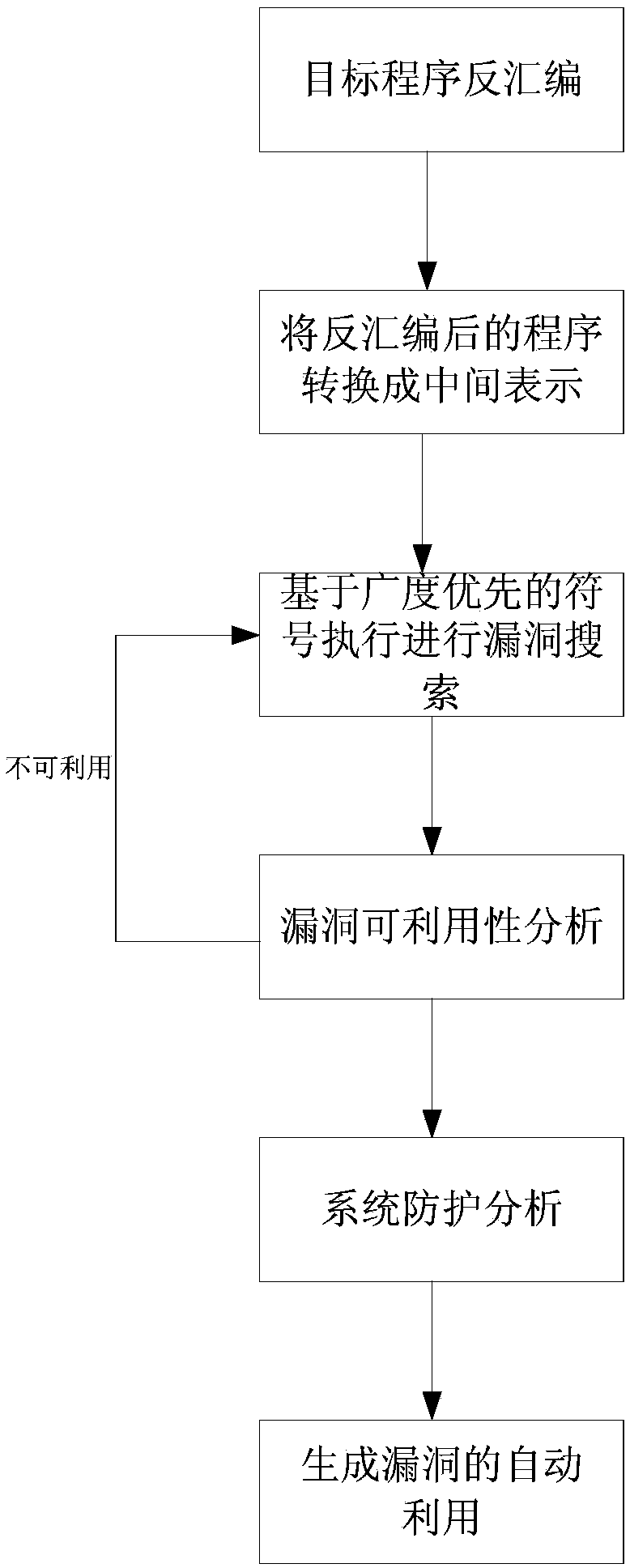
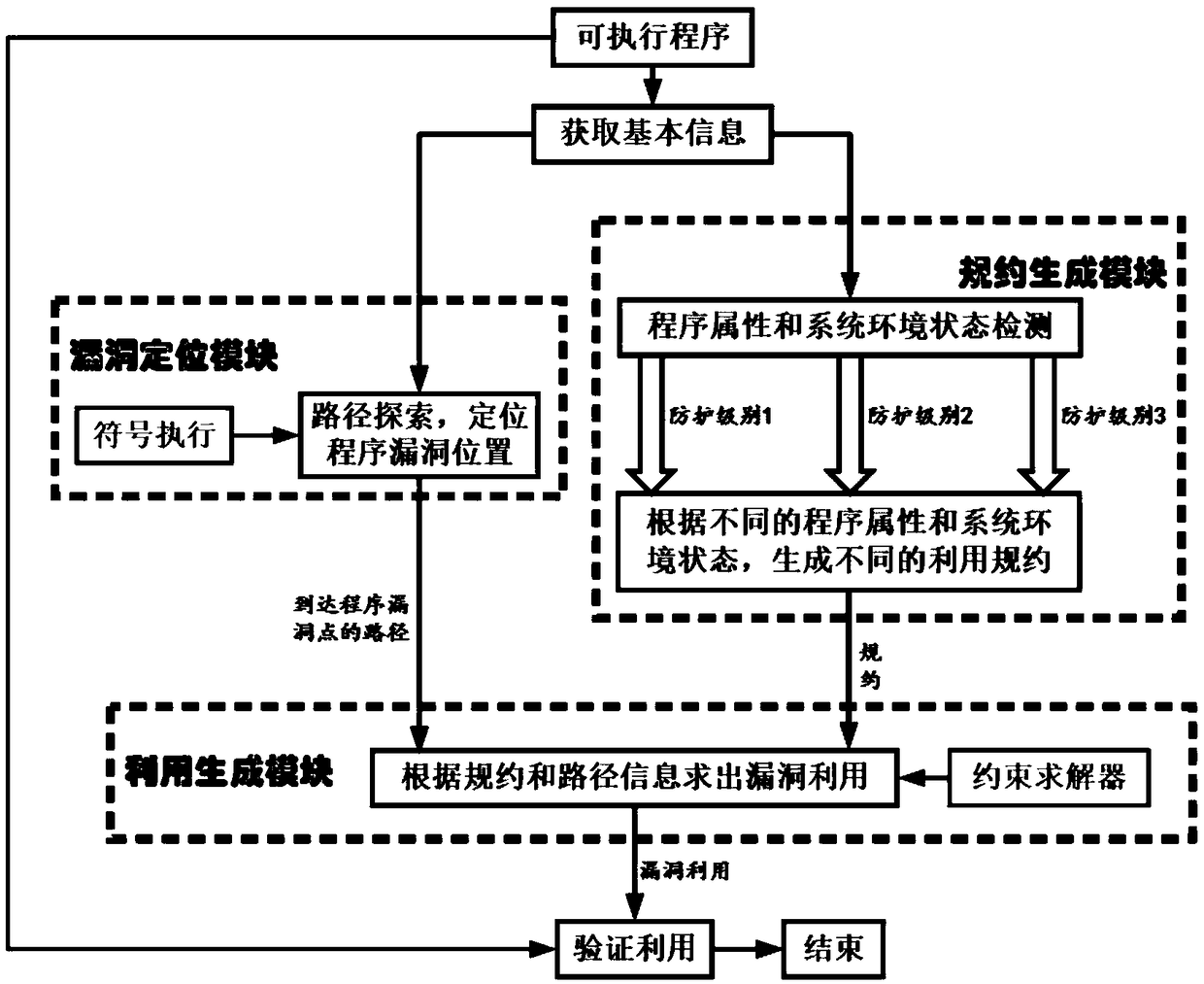
[0036] S1. Obtain program information of the target binary program;
[0037] S2. Traversing the target binary program using a symbolic execution method according to the obtained program information, searching for software vulnerabilities existing in the program, and obtaining path information of the searched software vulnerabilities;
[0038] S3. Obtain the environmental information of the current system, and generate the required utilization protocol to bypass system protection according to the acquired environmental information and program information;
[0039] S4. Solve according to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com