A mobile terminal file encryption and decryption system and method based on hardware encryption TF card
A hardware encryption and mobile terminal technology, applied in the field of information security, can solve the problems that the software encryption method cannot meet the requirements, multiple security risks, and be cracked, so as to save hardware design costs and driver software adaptation costs, ensure safety, and speed. The effect of encryption and decryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
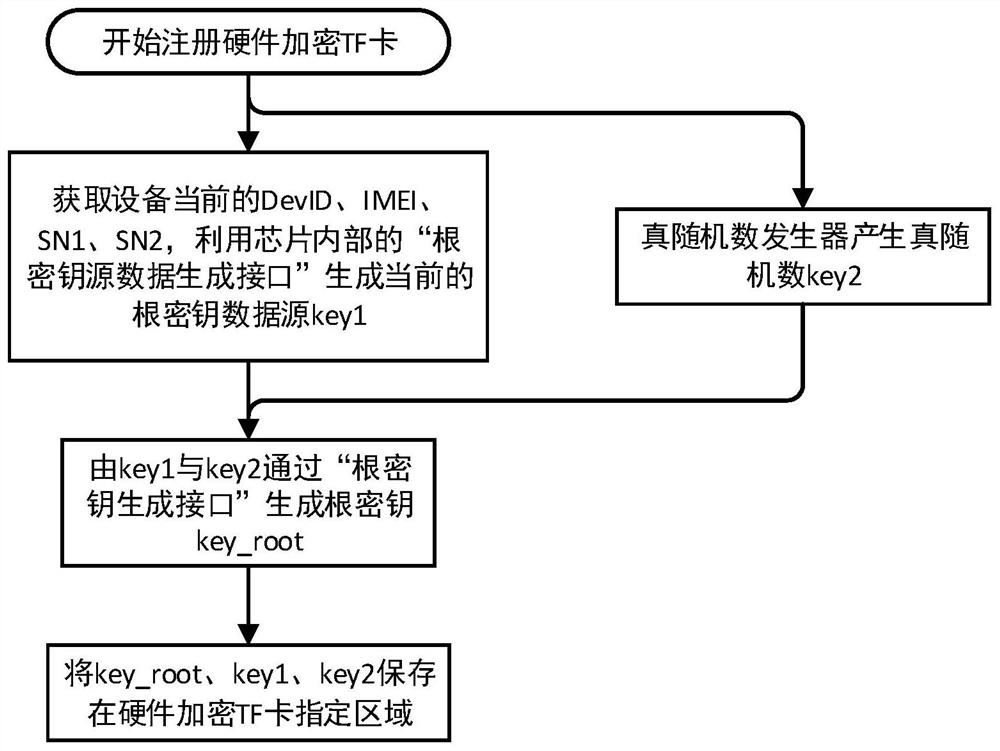
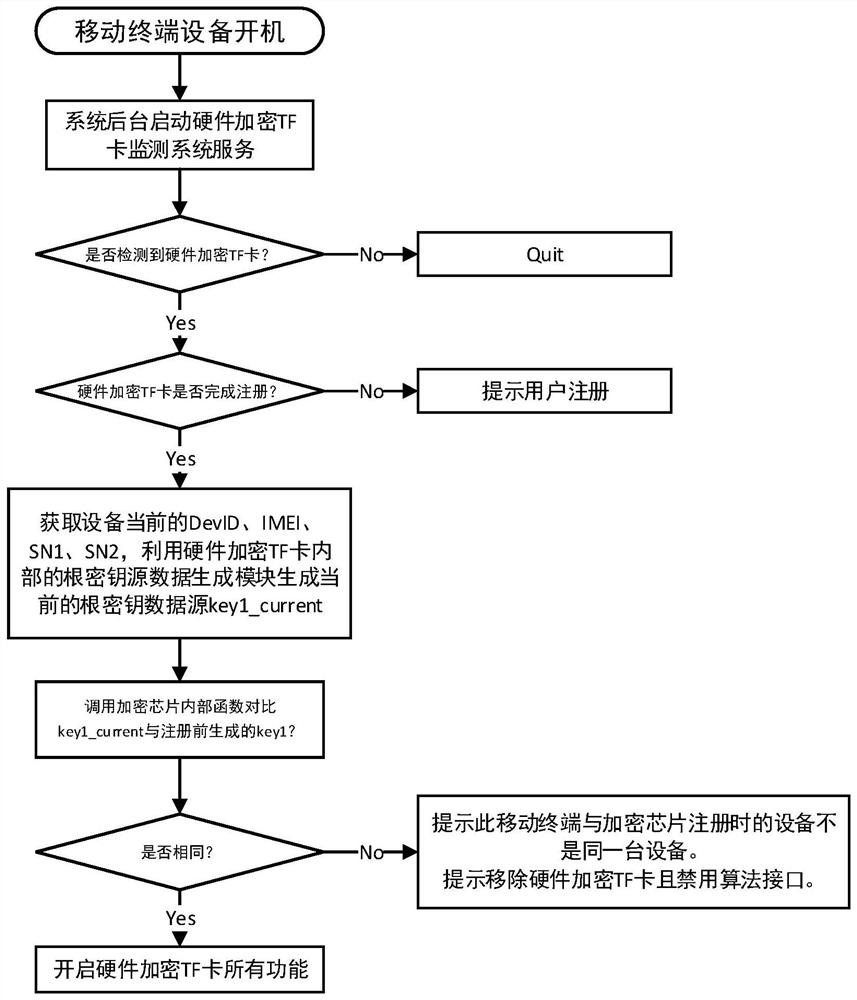
[0043] The design scheme in the embodiment of the present invention will be clearly and completely described below in conjunction with the accompanying drawings in the embodiment of the present invention. Obviously, the described embodiment is only a part of the embodiment of the system of the present invention, not the entire implementation example.
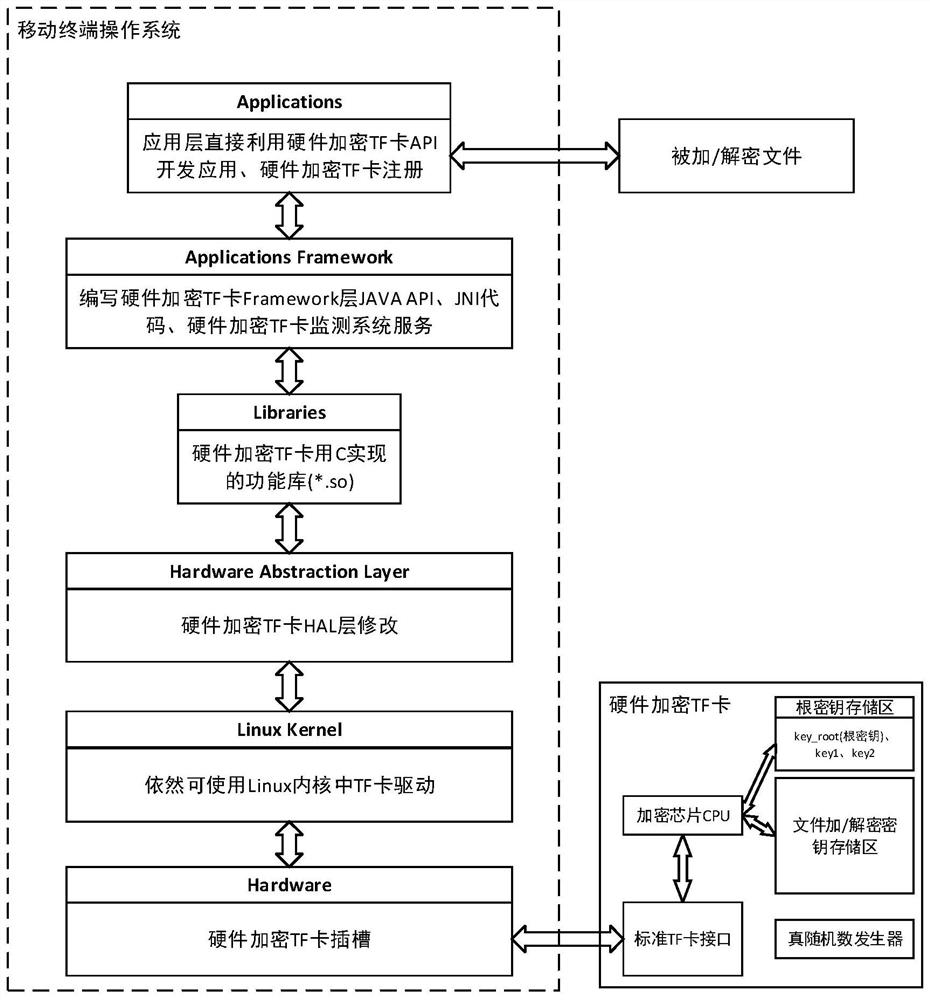
[0044] Such as figure 1 As shown, a kind of mobile terminal file encryption and decryption system based on hardware encryption TF card is proposed, wherein the mobile terminal operating system (for the support framework of the operating system underlying system of hardware encryption TF card, hardware encryption TF card monitoring system service and application layer Registration) and hardware encrypted TF card system (encrypted TF card internal file encryption / decryption key storage area, root key storage area, true random number generator, encryption chip CPU);
[0045] The mobile terminal operating system refers to the syste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com