A method of mining and analyzing information security vulnerabilities
A technology of information security and analysis methods, applied in computer security devices, special data processing applications, instruments, etc., can solve problems such as high rate of false positives and false positives, damage to user programs, failure to detect applications, etc., to achieve false negatives and false positives Low reporting rate, reduced computing load, and the effect of defending against secondary attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
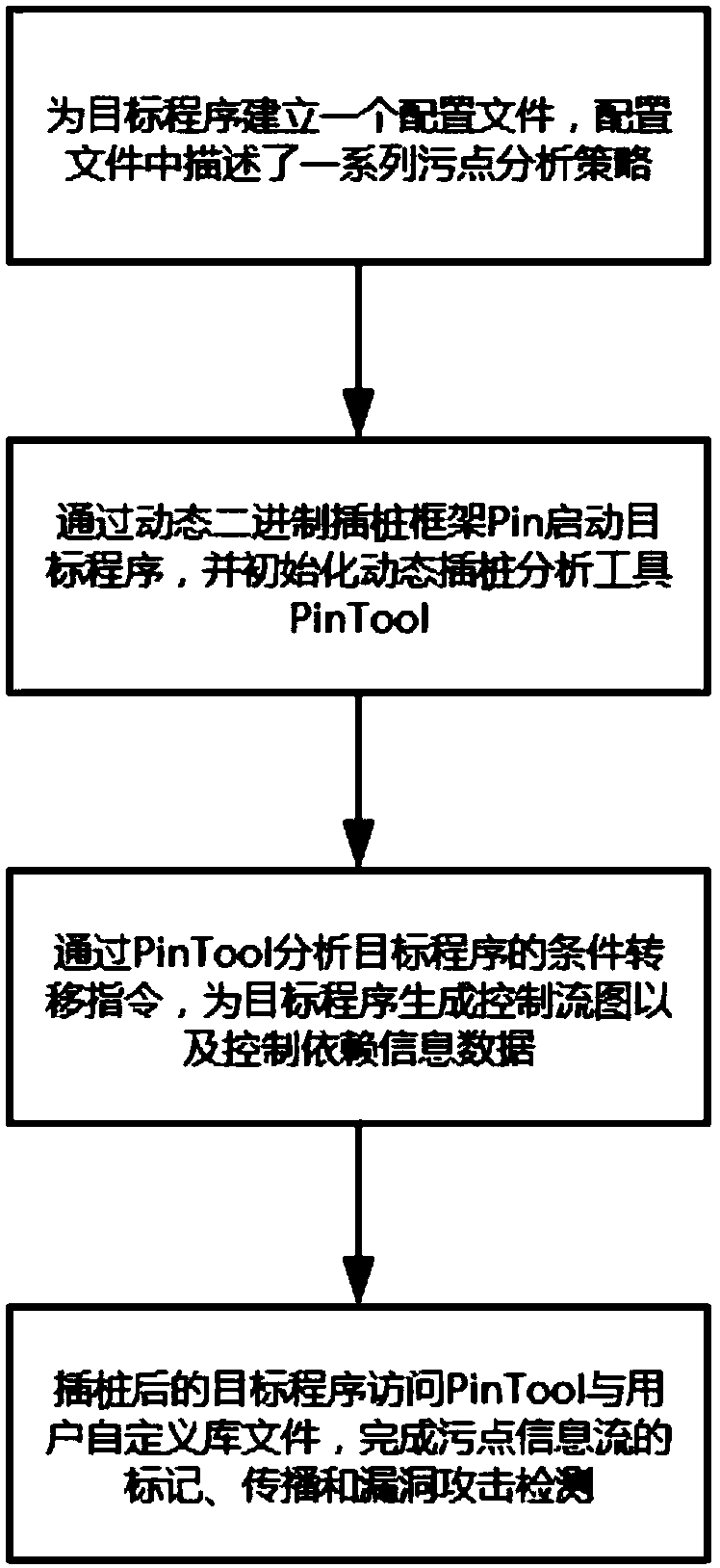
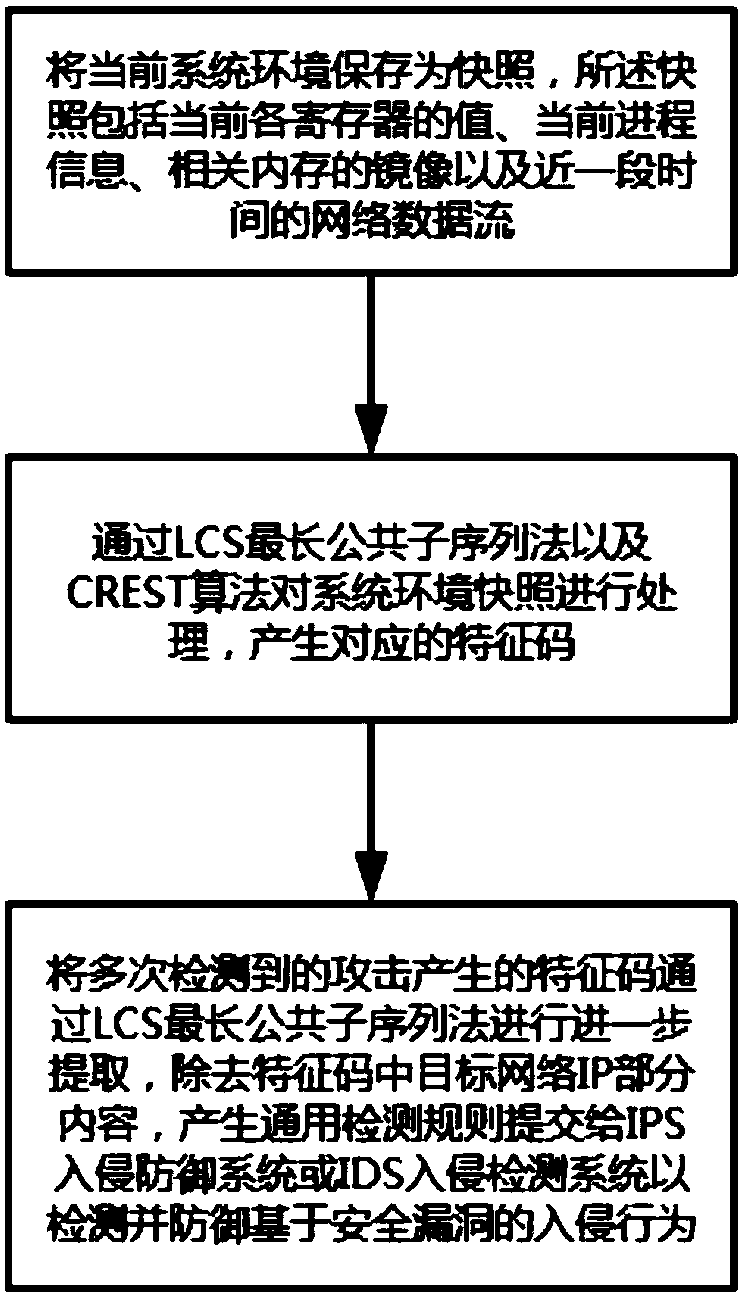
[0025] The principles and features of the present invention will be described below in conjunction with the accompanying drawings, and the enumerated embodiments are only used to explain the present invention, and are not intended to limit the scope of the present invention.
[0026] The attack process of a general vulnerability is usually as follows: once the attacker discovers a security hole in the software system, he will find an opportunity to send the shellcode code and malicious attack string as the core of the overflow program and worm virus to the host running the software system through the network , and the software system will put the received external data into the memory buffer, these external data will cause the memory buffer to overflow, and then overwrite the return address or function pointer of the normal function, resulting in a change in the software system process, and then run the attacker's prior The set shellcode code attacks the user's host. Through t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com