3D face live detection method, face authentication and recognition method and device
A liveness detection and face technology, applied in the computer field, can solve problems such as poor performance of liveness detection, achieve the effects of improving accuracy, effective security verification, and ensuring overall performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
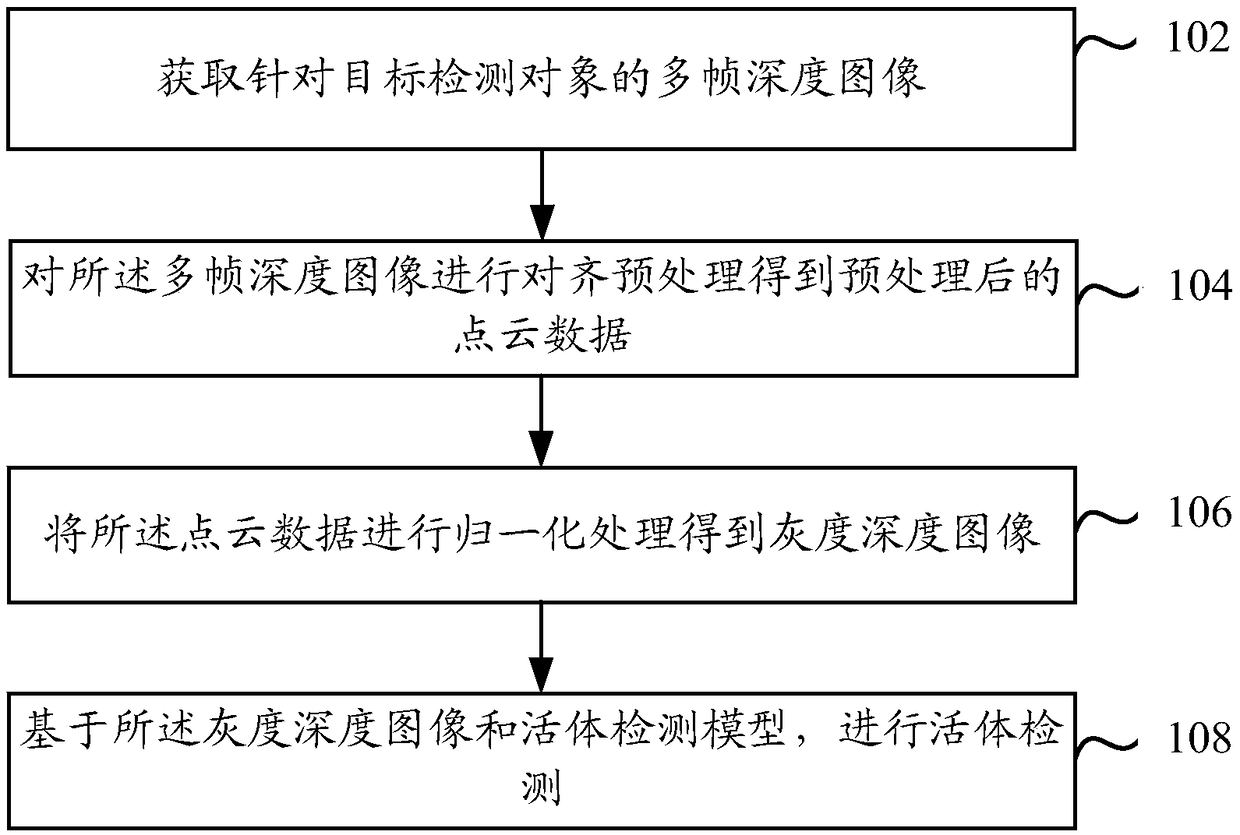
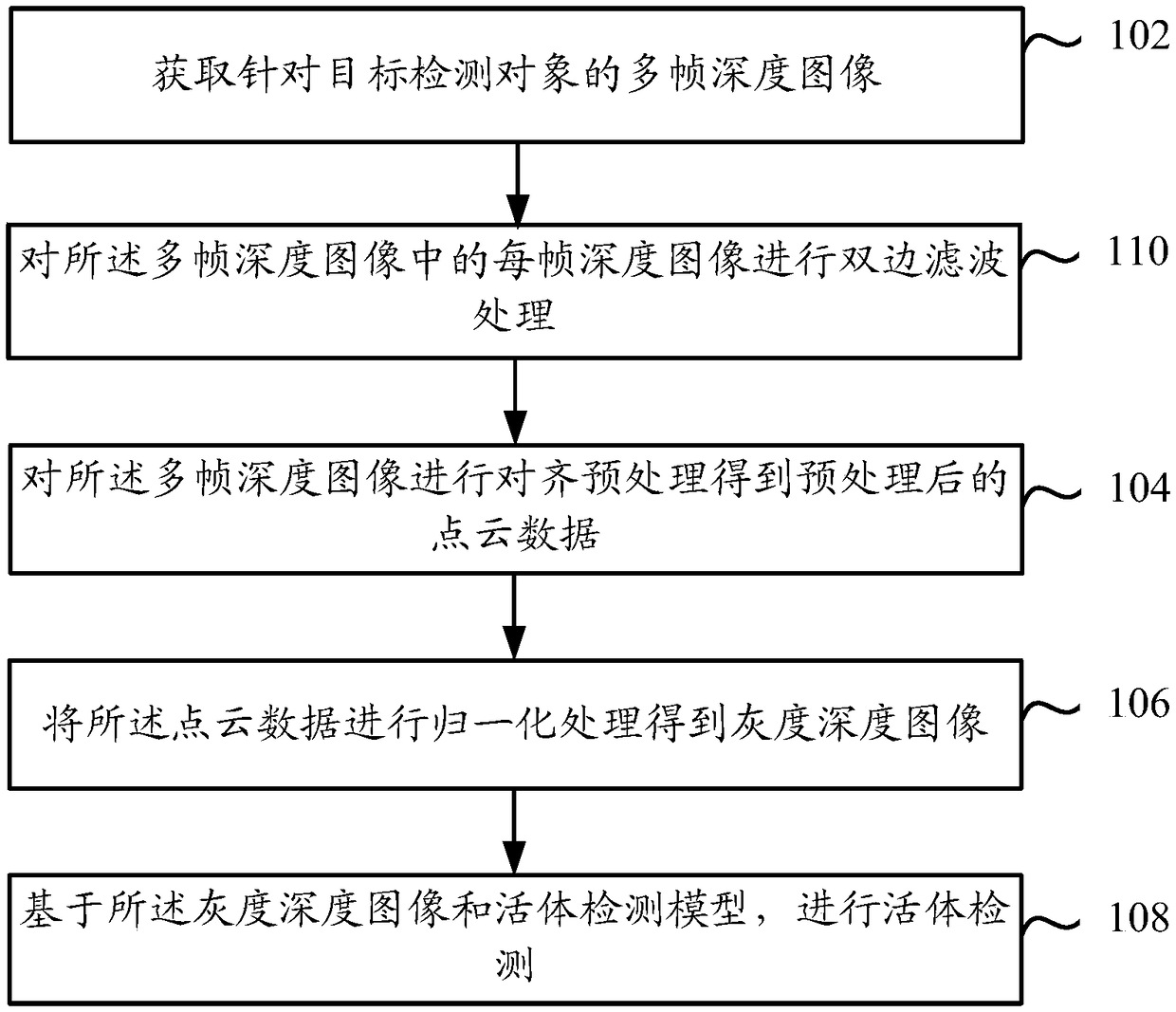
[0069] refer to Figure 1a As shown, it is a schematic diagram of the steps of the three-dimensional facial living detection method provided by the embodiment of this specification. The method can be executed by a three-dimensional facial living detection device or a mobile terminal installed with a three-dimensional facial living detection device.
[0070] The three-dimensional facial living body detection method may include the following steps:
[0071] Step 102: Obtain multiple frames of depth images for the target detection object.
[0072] It should be understood that in the embodiments of this specification, the 3D face liveness detection involved is mainly aimed at the 3D face liveness detection of human beings. According to the analysis of the 3D face image, it is determined whether the target detection object is a living body, that is, whether it is Object detection in the image The subject himself. In fact, the target detection object of the 3D face liveness detecti...
Embodiment 2
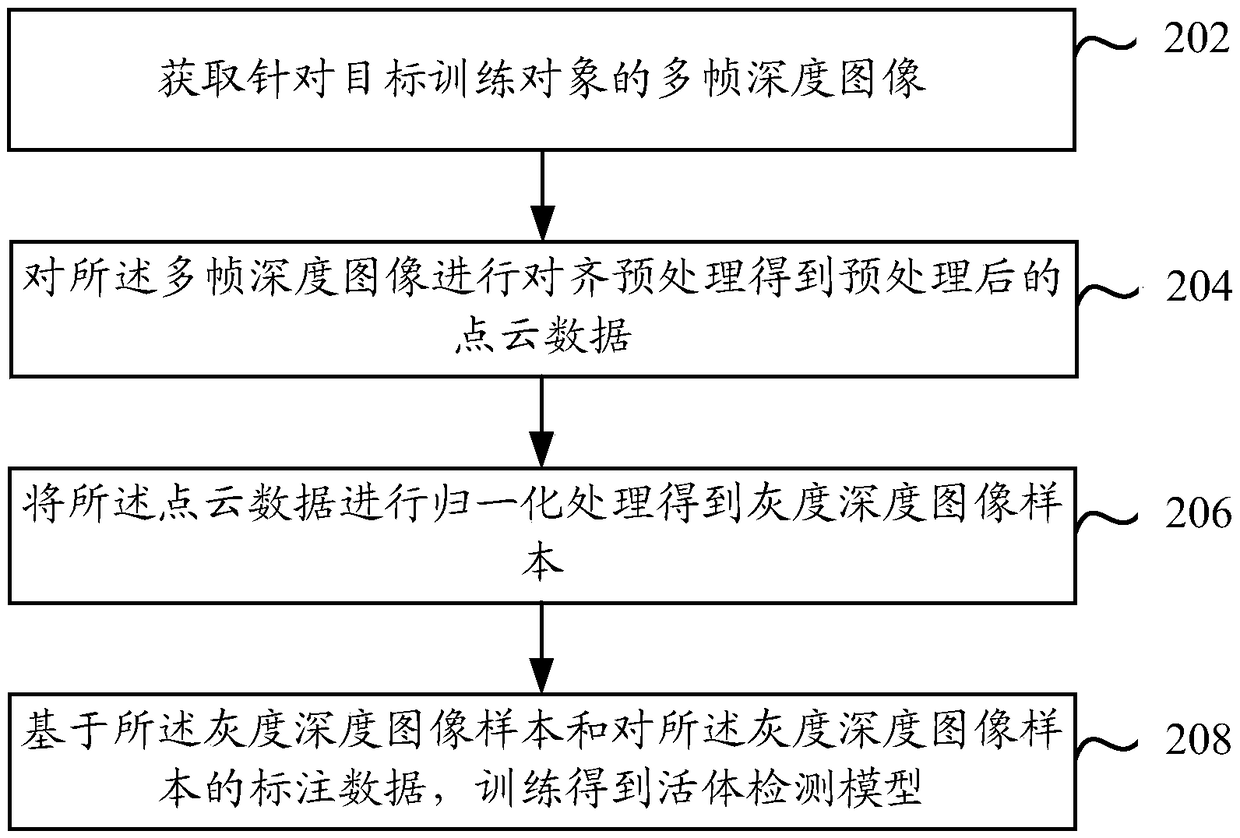
[0163] refer to Figure 4 As shown, it is a schematic diagram of the steps of the face recognition recognition method provided by the embodiment of this specification, and the method can be executed by a face recognition recognition device or a mobile terminal installed with a face recognition recognition device.
[0164] The facial recognition recognition method may include the following steps:
[0165] Step 402: Obtain multiple frames of depth images for the target detection object.
[0166] For the specific implementation of step 402, reference may be made to step 102.
[0167] Step 404: Perform alignment preprocessing on the multi-frame depth images to obtain preprocessed point cloud data.
[0168] For the specific implementation of step 404, reference may be made to step 104.
[0169] Step 406: Perform normalization processing on the point cloud data to obtain a grayscale depth image.
[0170] For the specific implementation of step 406, reference may be made to step ...
Embodiment 3
[0177] Refer below Figure 5 The electronic equipment of the embodiment of this specification is introduced in detail. Please refer to Figure 5 , at the hardware level, the electronic device includes a processor, and optionally also includes an internal bus, a network interface, and a memory. Wherein, the memory may include a memory, such as a high-speed random-access memory (Random-Access Memory, RAM), and may also include a non-volatile memory (Non-Volatile Memory), such as at least one disk memory. Of course, the electronic device may also include hardware required by other services.
[0178] The processor, network interface, and memory can be interconnected by an internal bus, which can be an Industry Standard Architecture (ISA) bus, a Peripheral Component Interconnect (PCI) bus, or an extended industrial bus. Standard structure (Extended Industry Standard Architecture, EISA) bus, etc. The bus can be divided into address bus, data bus, control bus and so on. For conv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com