A security monitoring method for power industrial control terminals based on business logic consistency
An industrial control terminal, business logic technology, applied in electrical components, data processing applications, instruments, etc., can solve problems such as virus spread, terminal anti-virus software cannot be detected and killed, and power system damage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The purpose and effects of the present invention will become more apparent by referring to the accompanying drawings in detail of the present invention.
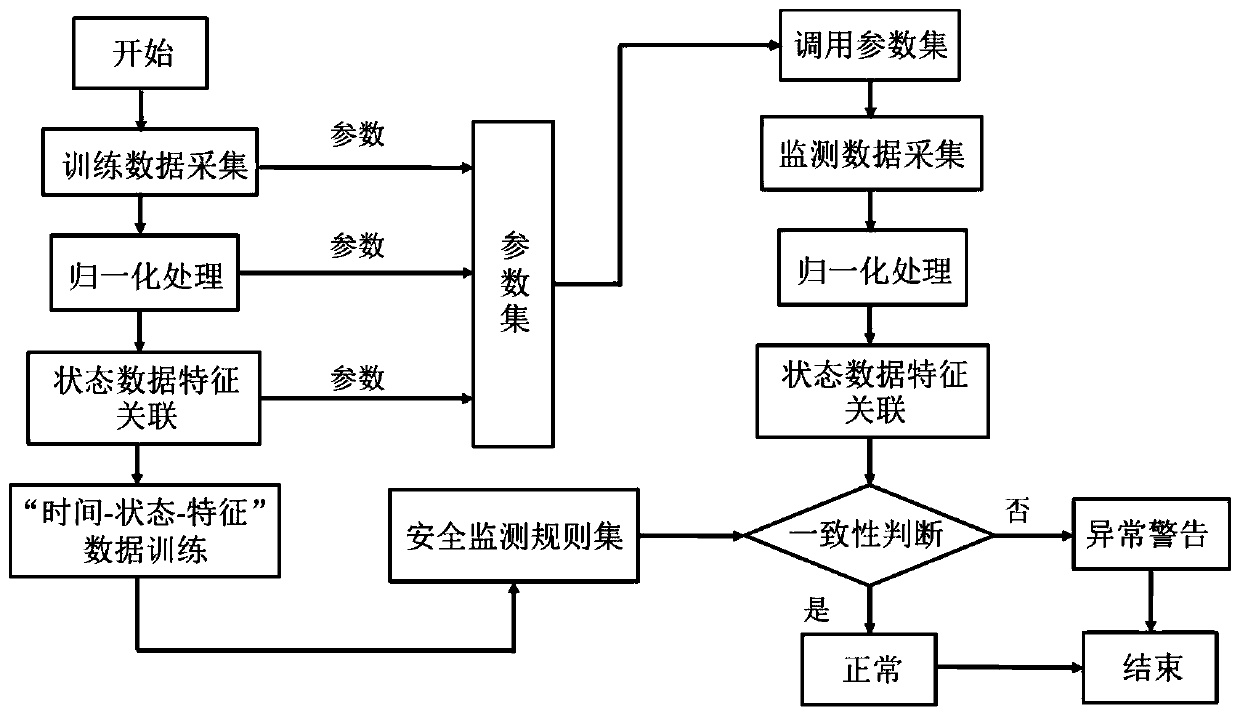
[0059] figure 1 It is a flow chart of a method for monitoring security of an electric power industrial control terminal based on business logic consistency, and the flow chart includes (i) the process of generating a security rule set with training data; and (ii) performing security monitoring of an electric power industrial control terminal based on a security rule set and a parameter set Methods. in particular:
[0060] Step 1: Collecting status data from the power industrial control terminal, the method specifically includes:
[0061] (1) Select all equipment terminals participating in the business according to the specific power business process. For example, a specific business needs equipment A and B to cooperate to complete;
[0062] (2) During the service life cycle, continuously monitor and collect status...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com