Method, device, computer equipment and storage medium for port scan detection
A port scanning and port technology, applied in the field of information security, can solve the problems of high false alarm rate and low detection accuracy, and achieve the effect of reducing false alarm rate, improving detection accuracy, and convenient and effective detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
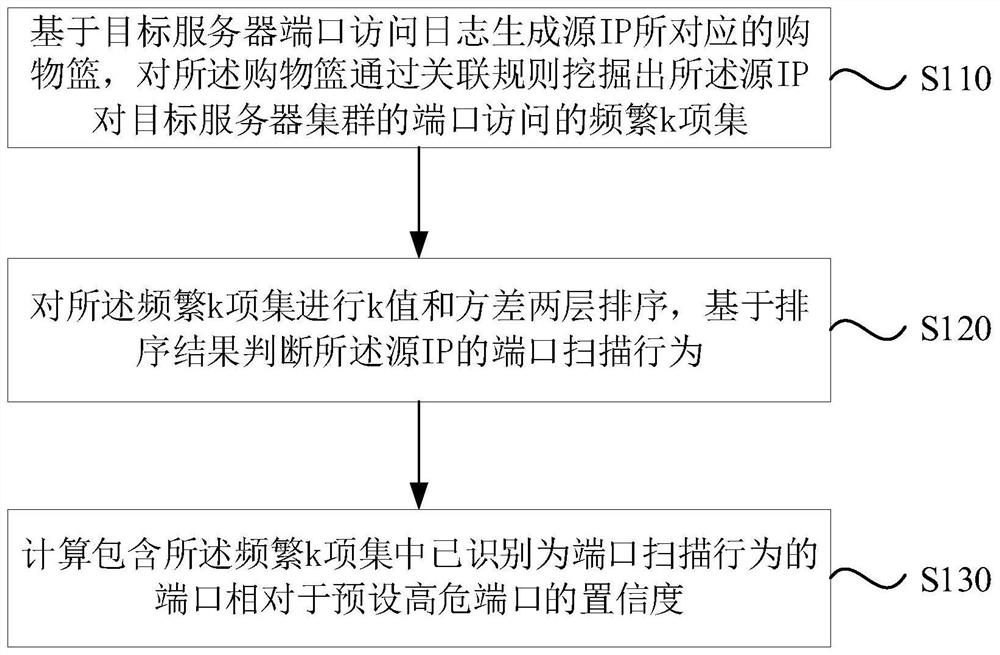
[0024] figure 1 It is a flow chart of a method for port scan detection provided in Embodiment 1 of the present invention. This embodiment is applicable to the situation of inspecting port scan behavior and identifying high-risk ports. The method can be implemented by configuring hardware and / or software The device of port scanning detection is carried out, specifically comprises the following steps:
[0025] Step S110: Generate a shopping basket corresponding to the source IP based on the port access log of the target server, and mine the frequent k-item sets of the port access of the source IP to the target server cluster through association rules for the shopping basket.
[0026] Extract the access records within the time slice from the target server port access log of the operation and maintenance security audit system, including source IP, destination IP, port and access time. According to the port access log of the target server, generate its own shopping basket for each...
Embodiment 2
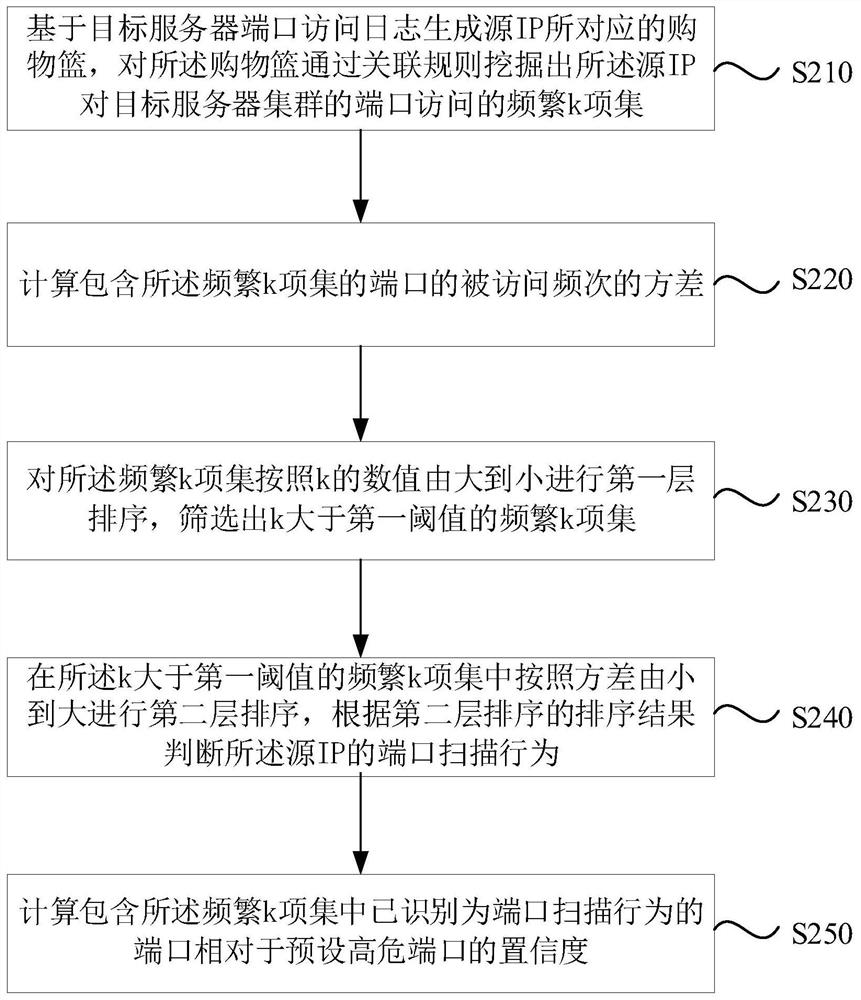
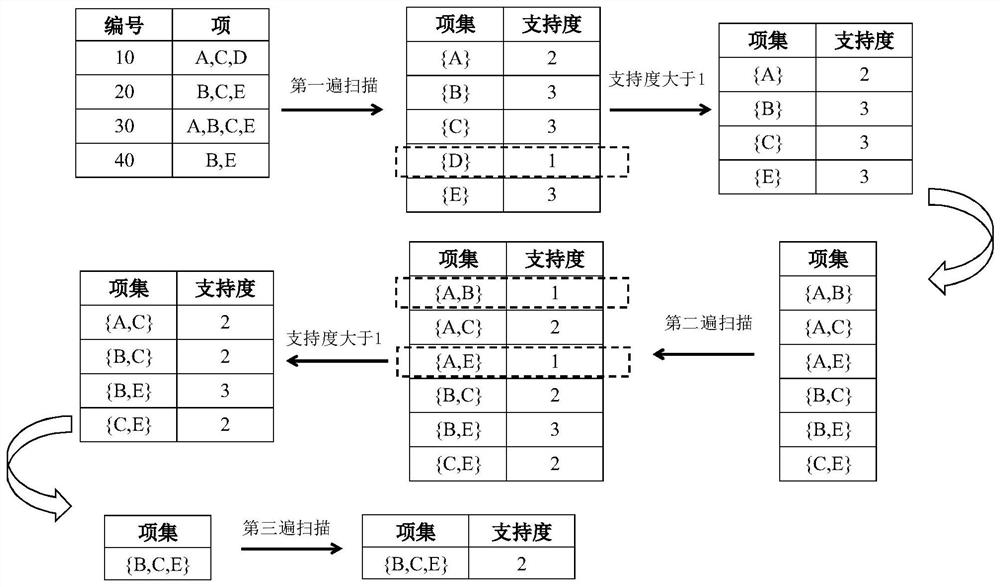
[0040] figure 2 It is another flow chart of a method for port scan detection in Embodiment 2 of the present invention. This solution proposes to use the Apriori association rule algorithm to find out the frequent item sets of port access to detect port scanning behavior, and then find out the association relationship between high-risk ports according to the frequent item sets, improve the port detection accuracy, and reduce the false alarm rate. The basic principle of Apriori algorithm is to use support to represent the strength of association rules, and regard items with association rules as a set. The strength of a rule association can be measured by support and confidence. Such as figure 2 As shown, a method for port scan detection provided in this embodiment specifically includes:
[0041] Step S210: Generate a shopping basket corresponding to the source IP based on the port access log of the target server, and mine the frequent k-item sets of the port access of the s...
Embodiment 3
[0055] Figure 4 A schematic structural diagram of a device for port scan detection provided by Embodiment 3 of the present invention, as shown in Figure 4 As shown, the device includes: a frequent itemset generating module 310 , a port scanning judging module 320 and a high-risk port judging module 330 .
[0056] Wherein, the frequent itemset generation module 310 is used to generate the shopping basket corresponding to the source IP based on the target server port access log, and dig out the frequent k of the port access of the source IP to the target server cluster through association rules for the shopping basket itemsets.
[0057] The port scanning judging module 320 is configured to sort the frequent k-itemsets in two layers of k value and variance, and judge the port scanning behavior of the source IP based on the sorting result.
[0058]The high-risk port judging module 330 is configured to calculate the confidence of the port identified as the port scanning behavio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com