Non-contact electricity-stealing prevention real-time monitoring device and method
A real-time monitoring, non-contact technology, applied in measurement devices, measurement of electrical variables, measurement of time integration, etc., can solve the problem of inability to effectively prevent non-contact electricity theft, inability to accurately locate users of electricity theft, and inability to upload electricity theft information in real time. and other problems, to achieve the effect of meeting important events and real-time requirements, alleviating the anti-stealing pressure, and reducing the scope of suspected electricity theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
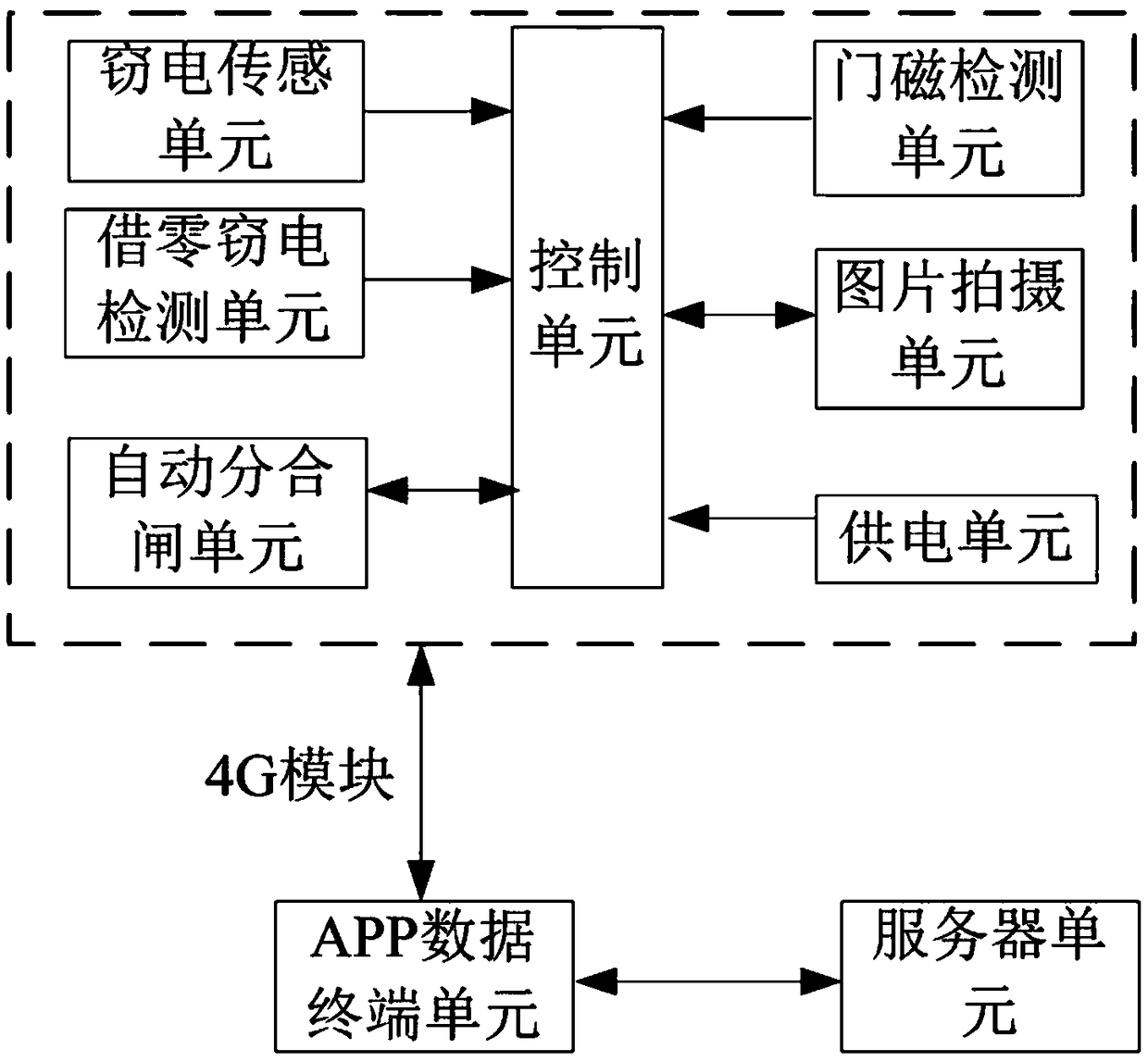
[0026] This embodiment discloses a real-time monitoring device for preventing non-contact electricity theft, such as figure 1 As shown, the device includes a control unit, a power stealing sensor unit connected to the control unit, a zero power stealing detection unit, a door magnetic detection unit, an automatic tripping and closing unit, a picture shooting unit, an APP data terminal unit and a power supply unit .
[0027] The electric stealing sensing unit includes a high-voltage electric shock detection module and a strong magnetic pulse detection module, which are used to receive external non-contact interference signals, and upload the collected interference voltage values to the control unit. For the multi-surface low-voltage metering box, it can realize the separate detection of strong magnetic signals of up to 6 epitopes in three phases and 15 epitopes in single phase. For the multi-meter metering box, a strong magnetic pulse detection module is installed behind eac...
Embodiment 2
[0046] This embodiment discloses a non-contact anti-electricity theft real-time monitoring method, which includes two parts: identity authentication out-of-the-box anti-theft and non-open-box anti-theft, such as Figure 7 As shown, identity authentication to open the box to prevent electricity theft includes the following steps: S01), log in to the APP data terminal, and remotely monitor the protection status of the metering box in real time; S02), the control unit judges whether the metering box is opened according to the signal detected by the door magnetic detection unit , if the box has not been opened, then end the judgment, if the box has been opened, then judge whether it is a normal open box according to the identity information; S03), if the identity authentication is successful, the display is normal after the access control interaction, then the metering box is opened normally, and the judgment ends , if the identity authentication fails and the access control intera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com