Method and apparatus for requesting use of memory
A memory and memory information technology, applied in the field of resource management, can solve problems such as memory leaks, increased program complexity, and low resource utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
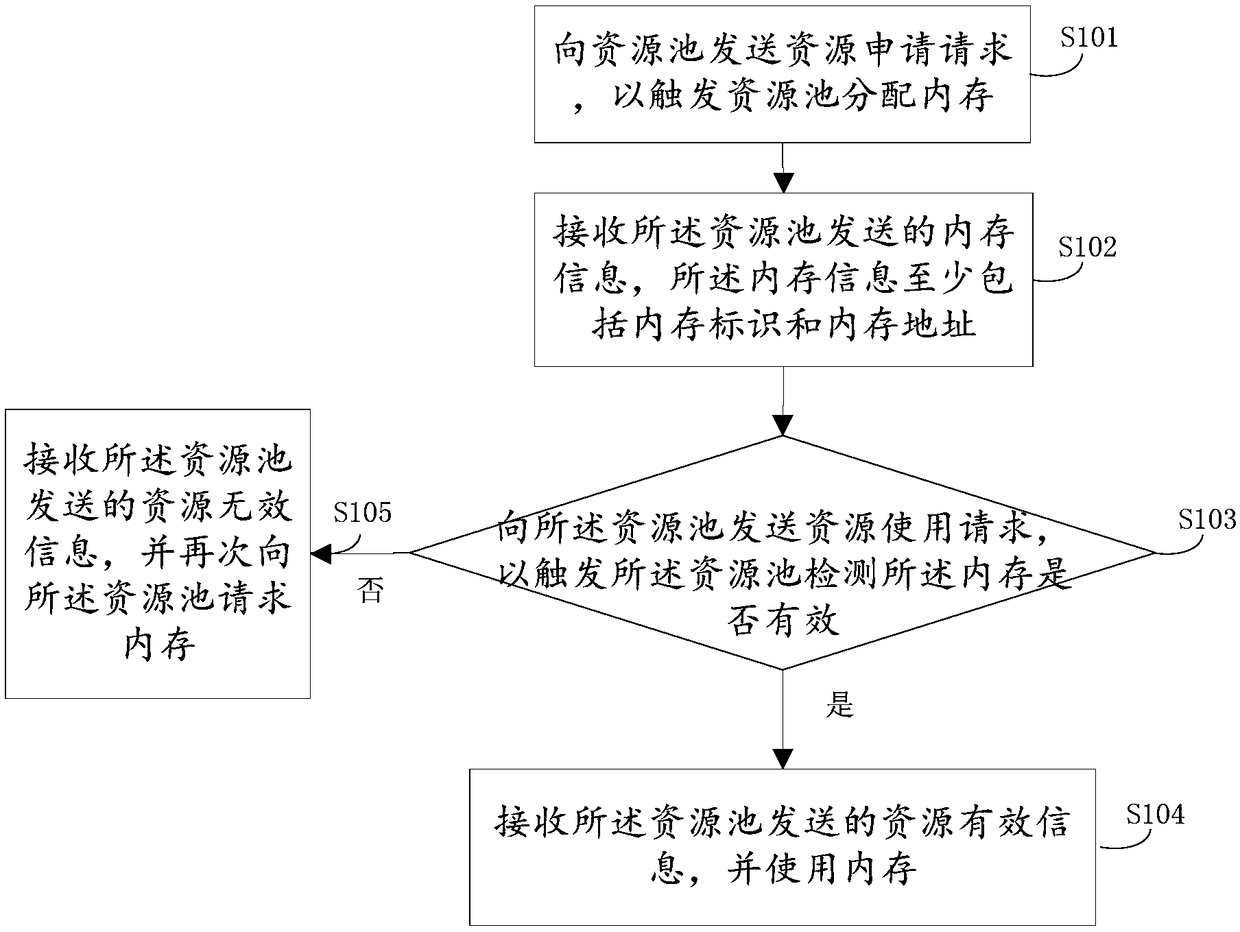
[0049] see figure 1 A flow chart of a method for applying and using memory is shown, the method is applied to task threads, and the task threads include task allocation threads and task processing threads, specifically including the following steps:
[0050] S101. Send a resource application request to the resource pool to trigger the resource pool to allocate memory;
[0051] Specifically, the task allocation thread receives a user request and applies for memory from the resource pool.
[0052] S102. Receive memory information sent by the resource pool, where the memory information includes at least a memory identifier and a memory address;
[0053] Wherein, the memory identifier can be a 64-bit integer ID, and the ID is only valid within the life cycle of the resource. The ID is incremented by 64 bits to ensure that the ID is not repeated in the software running cycle.
[0054] For example, the resource pool returns the memory whose ID is 100 and whose address is 0x123400...
Embodiment 2
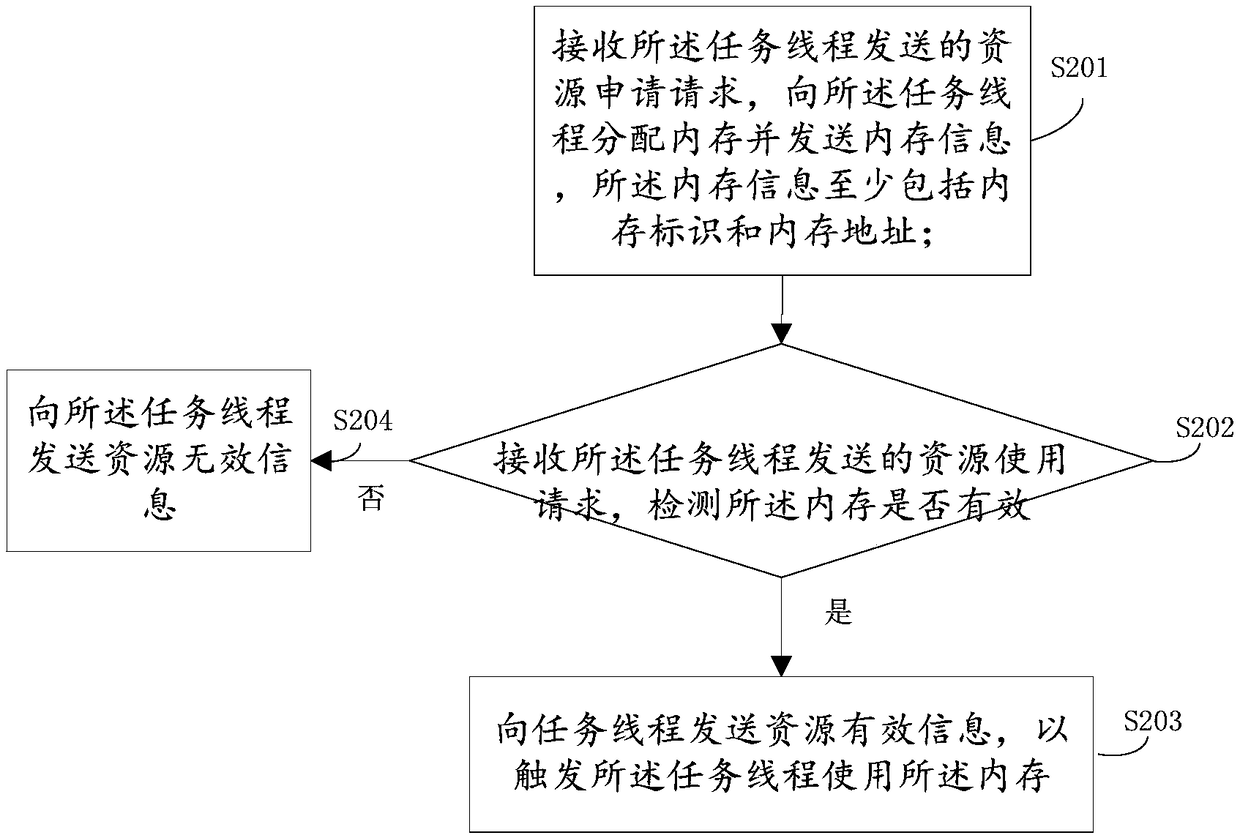
[0064] see figure 2 A flow chart of a memory application and usage method is shown, the method is applied to a resource pool, and specifically includes the following steps:
[0065] S201. Receive a resource application request sent by the task thread, allocate memory to the task thread and send memory information, where the memory information includes at least a memory identifier and a memory address;
[0066] S202. Receive a resource usage request sent by the task thread, and detect whether the memory is valid;
[0067] If valid, execute step S203
[0068] S203. Send resource availability information to the task thread, so as to trigger the task thread to use the memory.
[0069] The resource release request sent by the task thread is received, the memory is released, and release success information is sent to the task thread.
[0070] If invalid, execute step S204.
[0071] S204. Send resource invalidation information to the task thread.
Embodiment 3
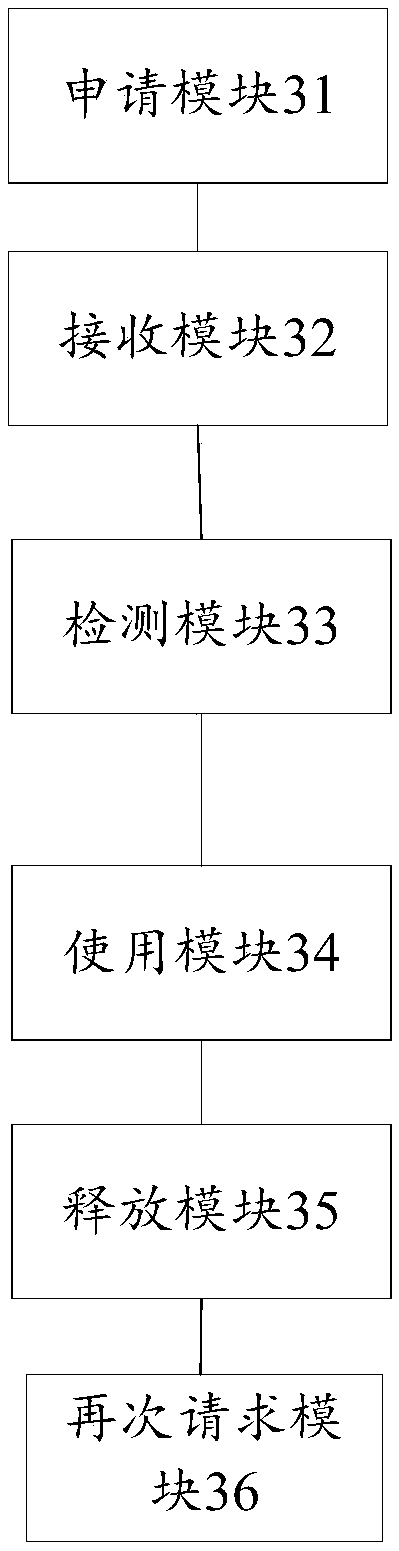
[0073] For the memory application and use method provided in the foregoing embodiments, the embodiment of the present invention provides a memory application and use device, see image 3 A structural block diagram of a device for applying for memory is shown, the device is applied to task threads, and includes the following parts:
[0074] The application module 31 is configured to send a resource application request to the resource pool, so as to trigger the resource pool to allocate memory;
[0075] A receiving module 32, configured to receive memory information sent by the resource pool, where the memory information includes at least a memory identifier and a memory address;
[0076] A detection module 33, configured to send a resource usage request to the resource pool, so as to trigger the resource pool to detect whether the memory is valid;
[0077] The use module 34 is configured to receive resource availability information sent by the resource pool if valid, and use t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com