Vehicle-mounted industrial control computer login method, device, system, computer equipment and medium
A login method and industrial computer technology, applied in the field of security certification, can solve problems such as hacker cracking, technology leakage of self-driving vehicles, and impact on the safety of self-driving vehicles, so as to ensure security, increase the difficulty of cracking, and improve user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
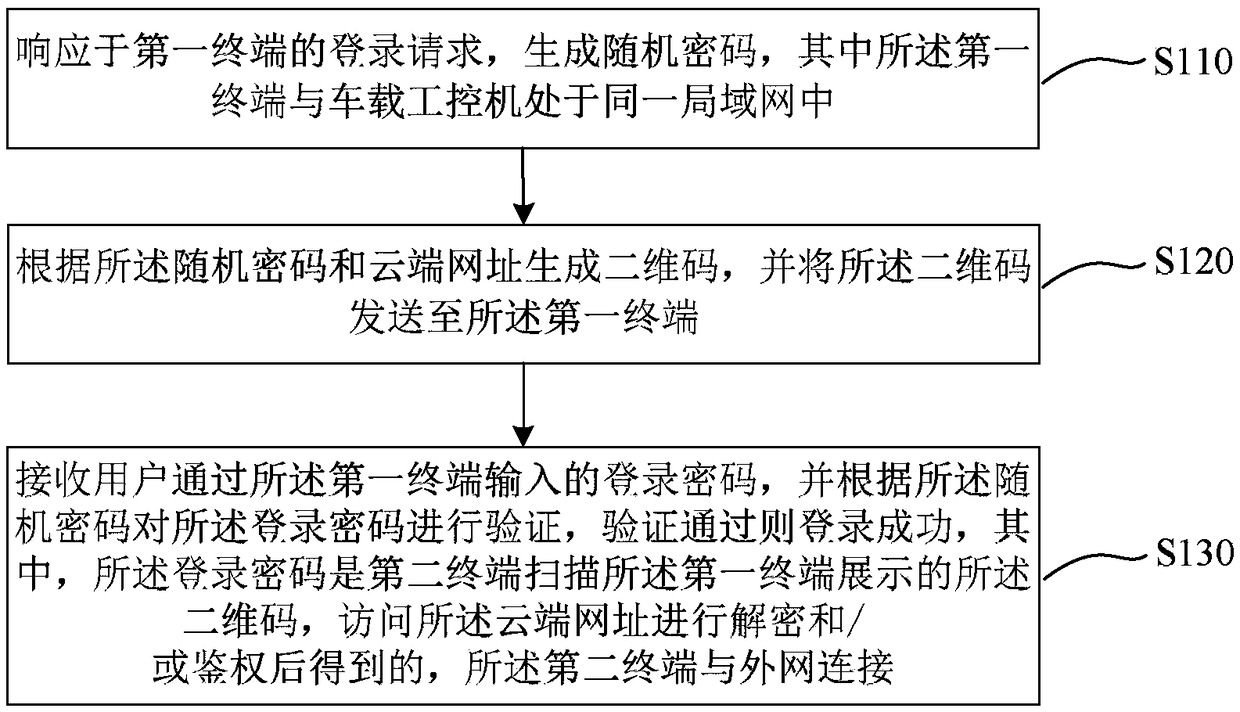
[0051] figure 1 It is a flow chart of the login method of the vehicle-mounted industrial computer provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of logging into the vehicle-mounted industrial computer for operation during the development or maintenance of the vehicle. The method can be executed by the vehicle-mounted industrial computer login device , the device can be implemented by software and / or hardware, and generally can be integrated in the vehicle-mounted industrial computer. Such as figure 1 As shown, the method specifically includes:
[0052] S110. Generate a random password in response to the login request of the first terminal, where the first terminal is in the same local area network as the vehicle-mounted industrial computer.
[0053]Among them, remote login can be performed through SSH (Secure Shell, Secure Shell Protocol), the vehicle-mounted industrial computer is used as an SSH server, and the first termin...
Embodiment 2
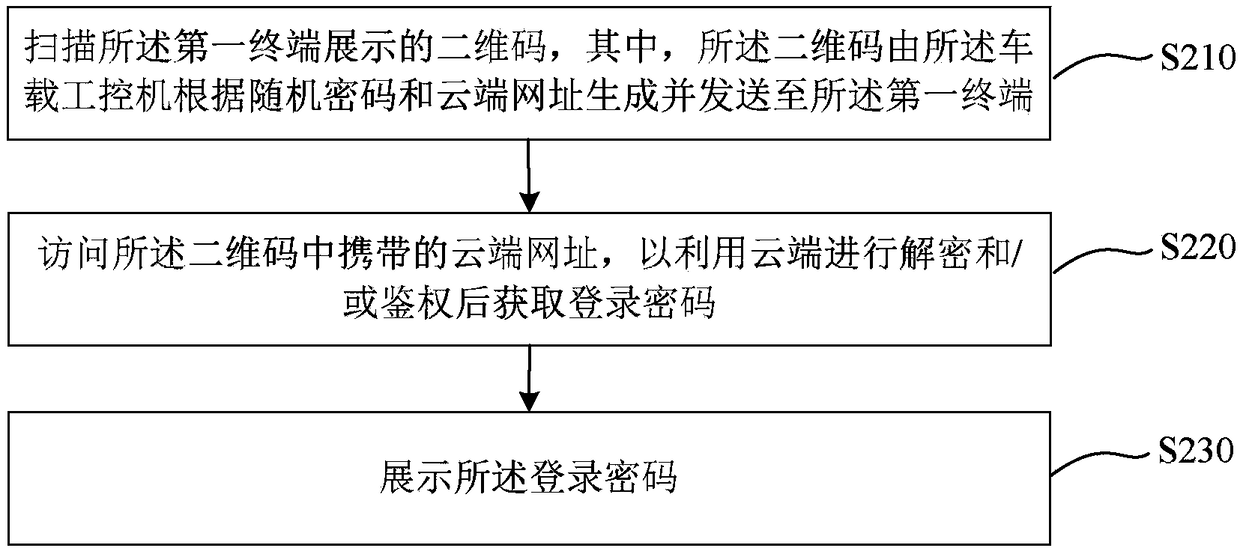
[0074] This embodiment provides a method for logging in to a vehicle-mounted industrial computer. This embodiment is applicable to the situation of logging in to a vehicle-mounted industrial computer for operation during vehicle research and development or maintenance. The method can be performed by a vehicle-mounted industrial computer login device, which can It is implemented by software and / or hardware, and generally can be integrated in the second terminal. The second terminal may be a user's mobile terminal capable of scanning two-dimensional codes, such as a mobile phone. In this embodiment, the first terminal and the vehicle-mounted industrial computer are in the same local area network, and the second terminal is connected to the external network. For technical details that are not described in detail in this embodiment, refer to the login method for a vehicle-mounted industrial computer provided in Embodiment 1 of the present invention.
[0075] figure 2 It is a fl...
Embodiment 3
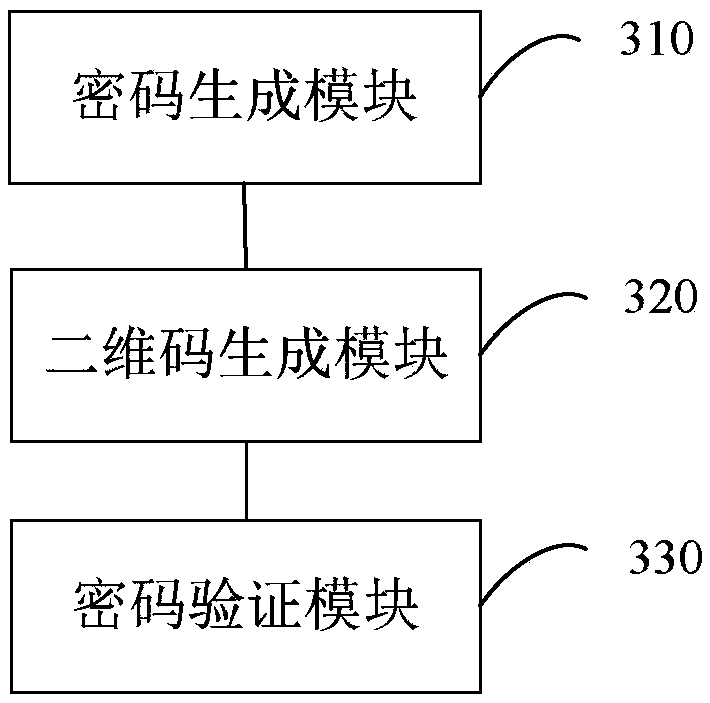
[0098] image 3 It is a schematic diagram of the structure of the vehicle-mounted industrial computer login device provided by the third embodiment of the present invention. This device can be applied to the vehicle-mounted industrial computer, such as image 3 As shown, the device includes:
[0099] A password generating module 310, configured to generate a random password in response to a login request of a first terminal, wherein the first terminal and the vehicle-mounted industrial computer are in the same local area network;
[0100] A two-dimensional code generation module 320, configured to generate a two-dimensional code according to the random password and the cloud URL, and send the two-dimensional code to the first terminal;
[0101] A password verification module 330, configured to receive a login password input by the user through the first terminal, and verify the login password according to the random password, and if the verification passes, the login is succe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com