A secure knn query method based on lbs
A query method and secure two-party computing technology, applied in the field of data privacy protection, can solve problems such as large time cost, difficult balance between query service security and query cost, leaked data access mode, etc., and achieve the effect of avoiding reasoning attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
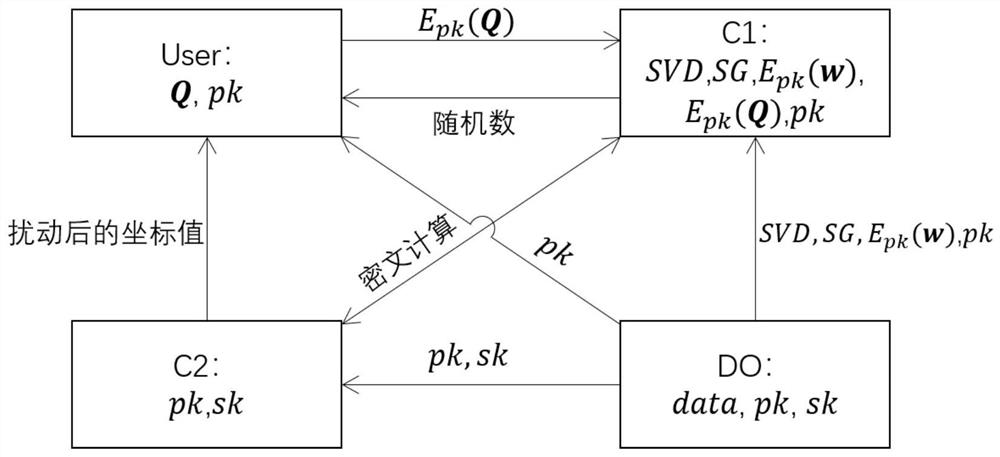
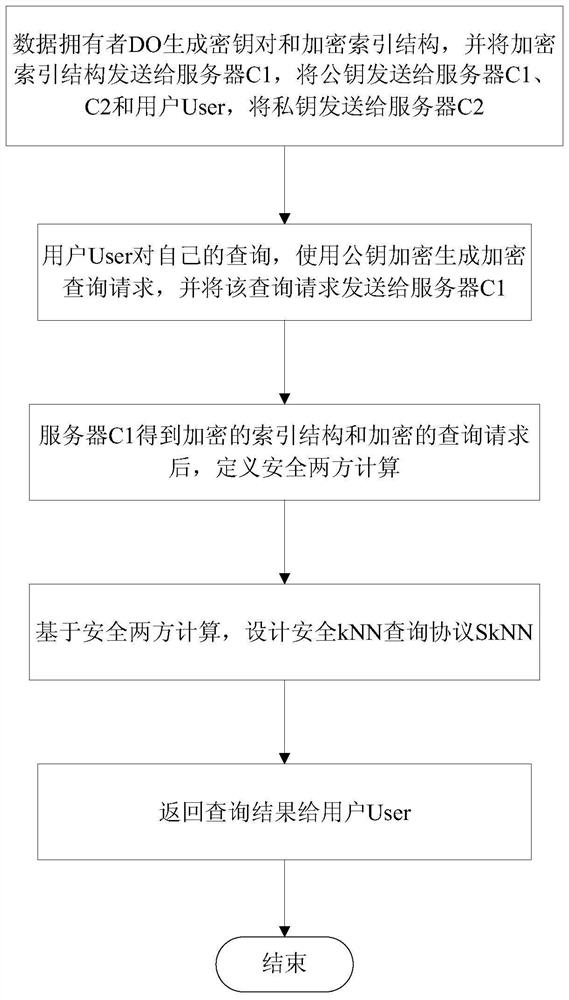
[0152]Further explanation will be further described below with reference to the accompanying drawings and specific embodiments, such asfigure 1 versusimage 3 As shown, specific processes include:
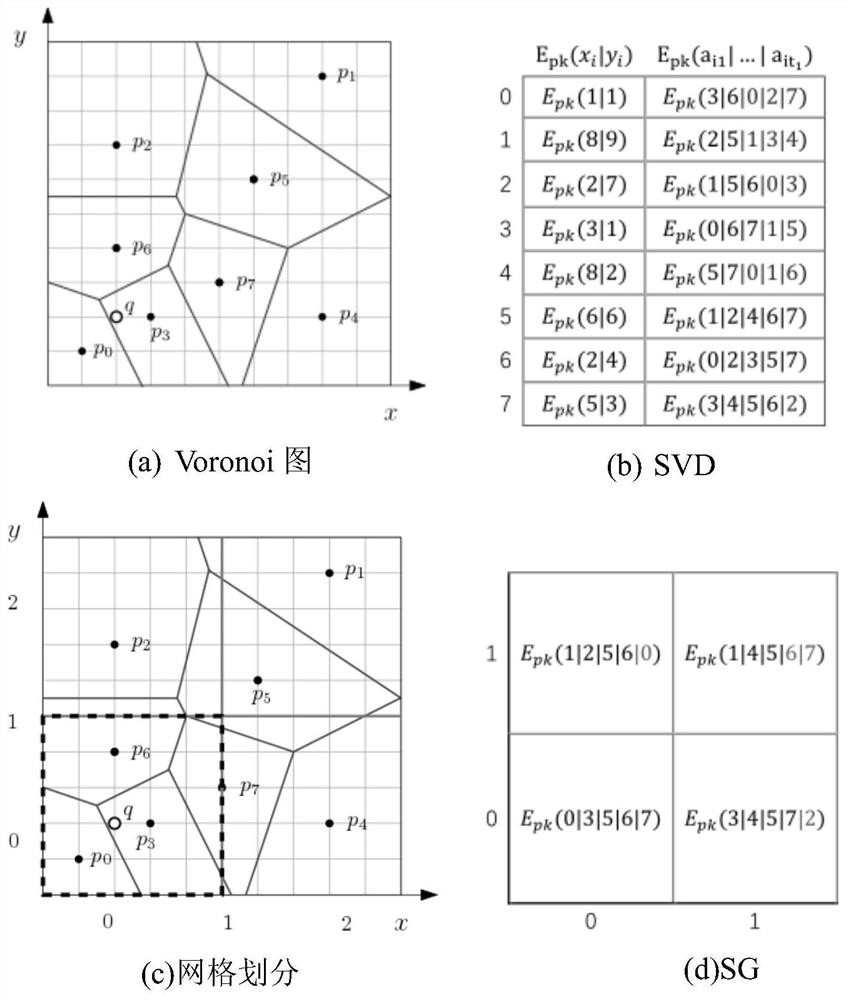
[0153]Step 1, the data owner DO generates a key pair (PK, SK), and encryption index structure, where the generated paillier has a key length of 1024 bits, and transmits the encrypted index structure to the server C1, send the public key PK. Servers C1, C2, and User User, send private key SK to the server C2. Use GOWALLA to check in the data set, and randomly select 1000 points to test, the points point POI is used as the data point, and the data is standardized to 16-bit large integers, each integer is used to use the data owner DO to process the processed data point as a seed Node, use Fortune's Algorithm to build a Voronoi diagram, then grid divide, generate an encrypted index structure SVD and SG;
[0154]The encryption index structure includes: secure Voronoi map SVD and security grid divid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com