Data encryption method, data authentication method, and related device and system
A data encryption and data technology, which is applied in digital transmission systems, transmission systems, and key distribution, can solve problems such as inability to meet QKD terminal data authentication, inability to perform data integrity verification functions, and high collision probability of CRC check values. Reduce the risk of decryption, increase the pass rate, and improve the effect of randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
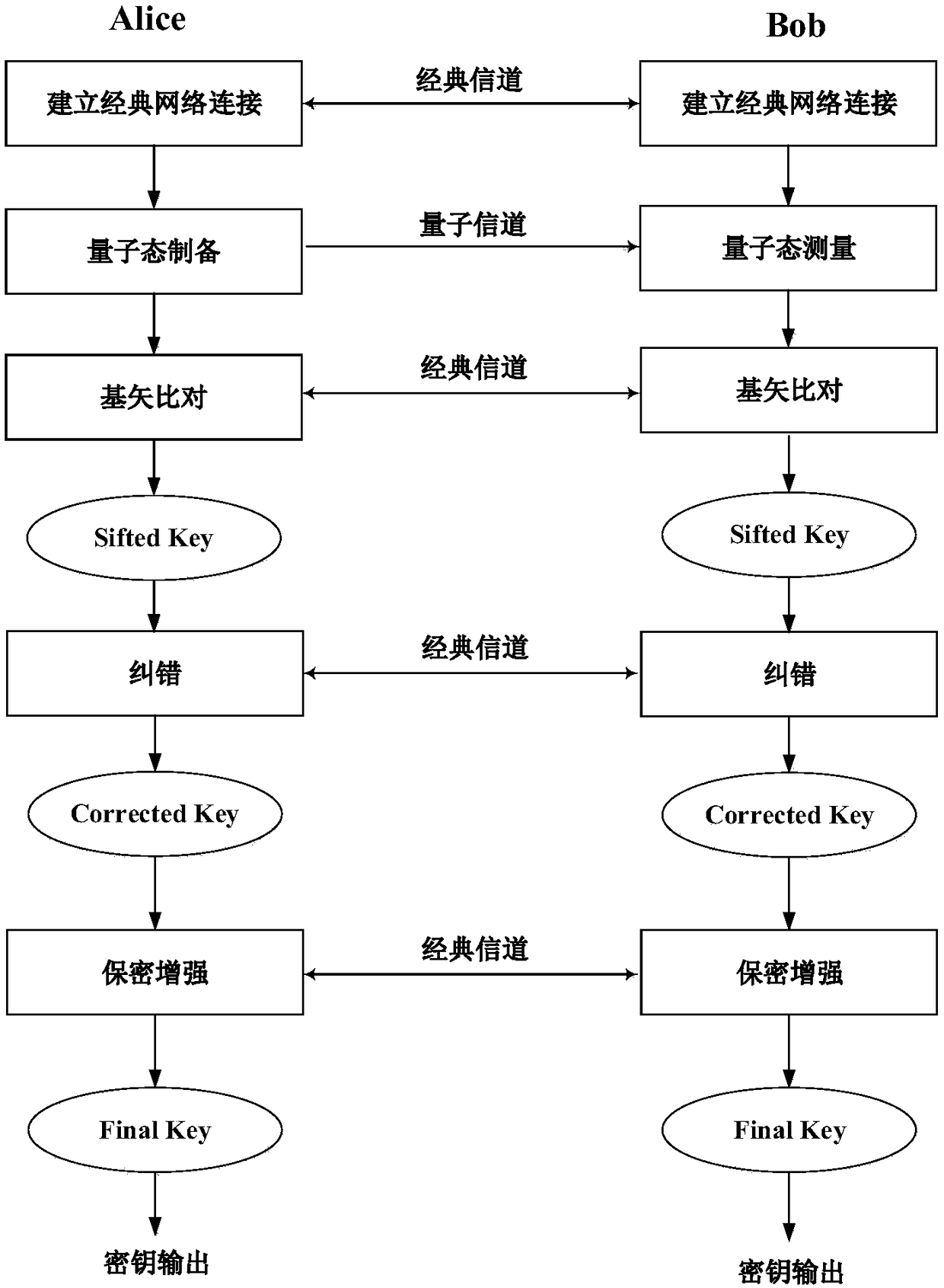
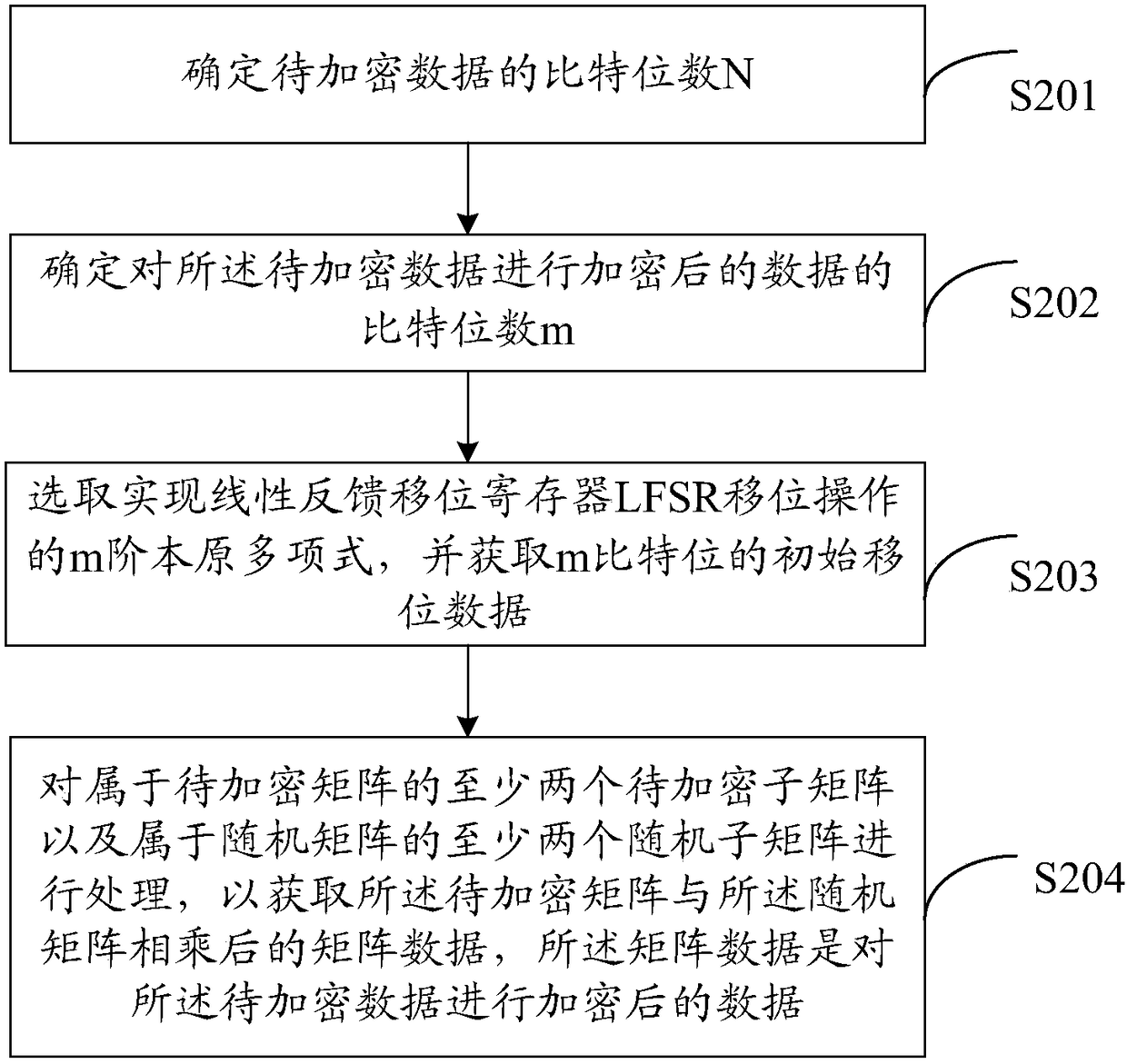
[0044] see figure 2 , which is a schematic flowchart of a data encryption method provided in the embodiment of the present application, the method includes:
[0045] S201: Determine the number of bits N of the data to be encrypted.
[0046] S202: Determine the number of bits m of the data after encrypting the data to be encrypted, where m is smaller than N.
[0047] S203: Select an m-order primitive polynomial for realizing the shift operation of the linear feedback shift register LFSR, and obtain m-bit initial shift data.
[0048] It is necessary to select an m-order primitive polynomial in the LFSR function family according to the number of bits m of the encrypted data, for example, the 64th-order primitive polynomial x^64+x^7+x^6+x^5+x^4 +x^2+x+1, its purpose is to generate new bit data by using the m-order primitive polynomial according to the LFSR shift principle. It is understandable that a primitive polynomial with a higher order can be selected, so that the LFSR ps...
Embodiment 2
[0090] The first embodiment above introduces a method for encrypting the data to be encrypted, and the second embodiment introduces a method for authenticating the integrity of the data to be encrypted based on the encryption result.
[0091] see Figure 5 , is a schematic flowchart of a data authentication method provided in an embodiment of the present application, the data authentication method is applied to a QKD system, and the QKD system includes a first QKD terminal and a second QKD terminal communicating through a classical network. The data authentication method includes the following steps:
[0092] S501: The first QKD terminal encrypts the first data to be authenticated; wherein, the first data to be authenticated includes data A sent by the first QKD terminal to the second QKD terminal within a preset period of time, and The data B received by the first QKD terminal from the second QKD terminal within the preset time period.
[0093] Among them, the first QKD ter...
Embodiment 3
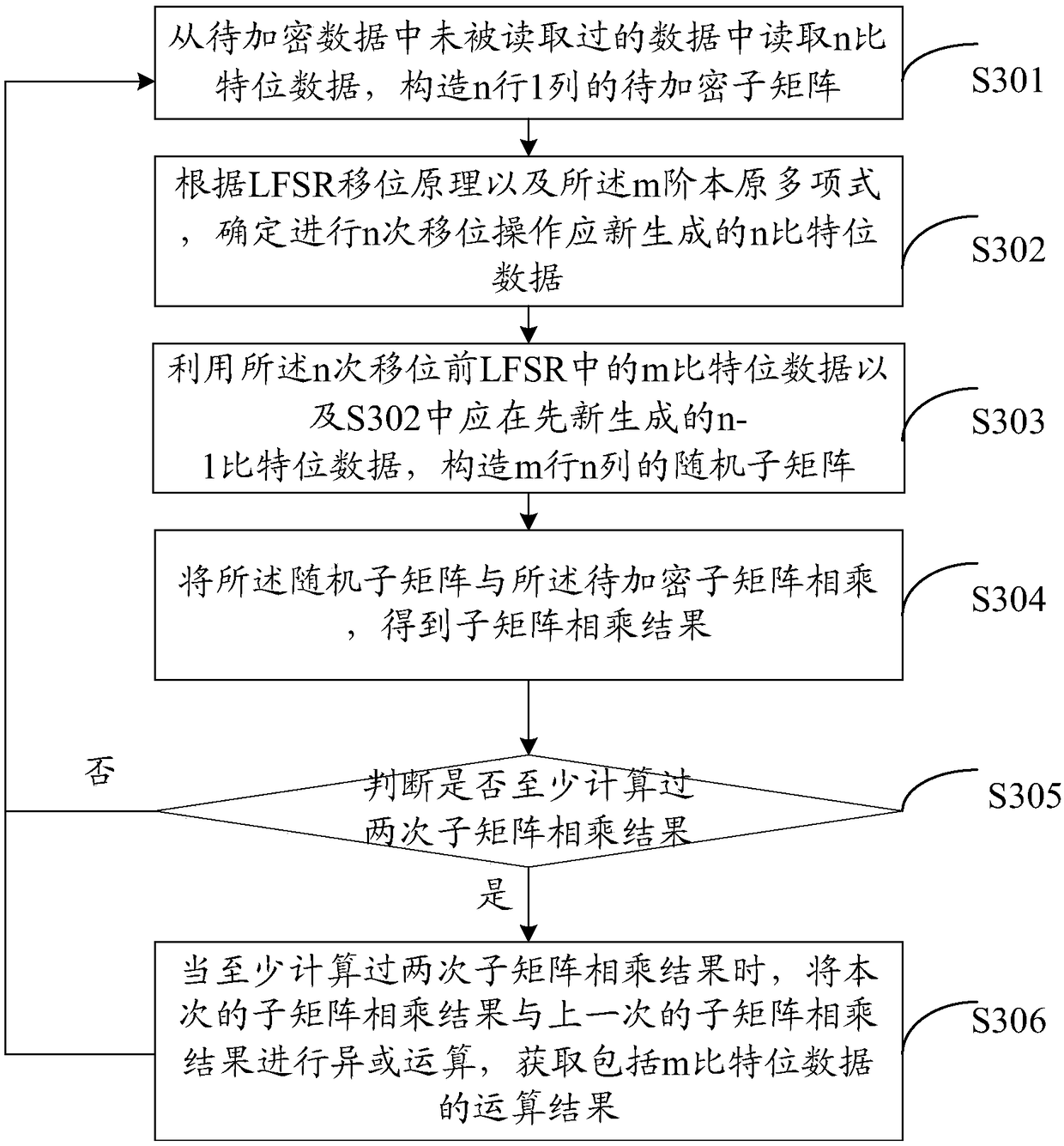
[0119] see Figure 6 , which is a schematic diagram of the composition of a data encryption device provided in the embodiment of the present application. The data encryption device 600 includes:
[0120] The number of bits determination unit 601 is configured to determine the number of bits N of the data to be encrypted, and determine the number of bits m of the data after encrypting the data to be encrypted, where m is less than N;
[0121] The shift parameter acquisition unit 602 is used to select the m-order primitive polynomial for realizing the shift operation of the linear feedback shift register LFSR, and obtain the initial shift data of m bits;
[0122] An encrypted data generation unit 603, configured to process at least two sub-matrices to be encrypted belonging to the matrix to be encrypted and at least two random sub-matrices belonging to the random matrix, so as to obtain The matrix data, the matrix data is the data after encrypting the data to be encrypted; wher...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com