Load balancing method, apparatus, device and storage medium
A load balancing and server-side technology, applied in the field of network communication, can solve problems such as sudden increase in traffic on the server side, sudden increase in visits, hot spots on the server side, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
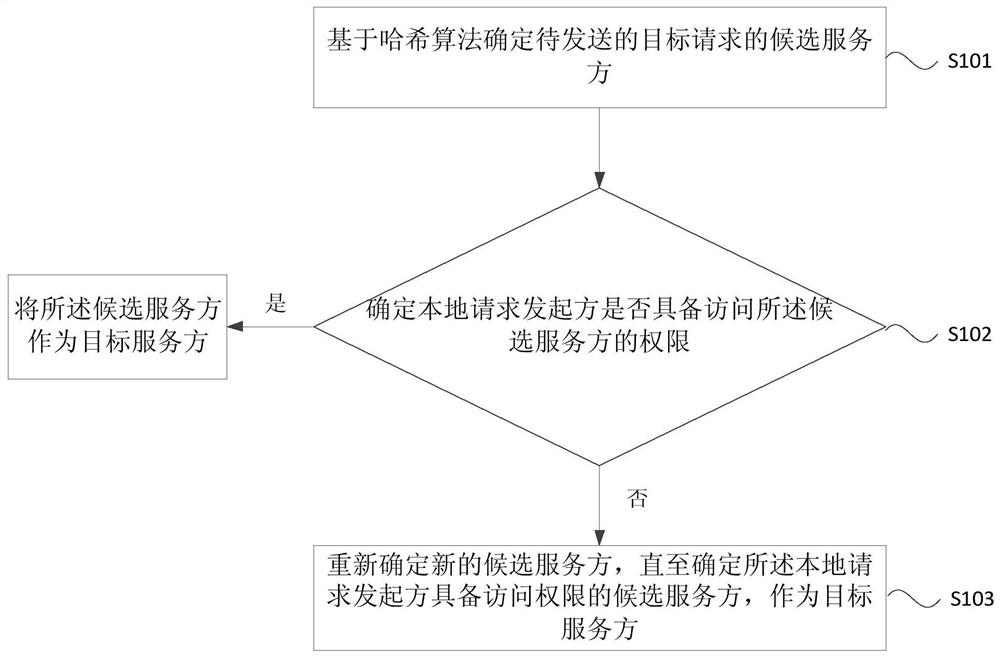
[0025] figure 1 It is a flowchart of a load balancing method provided by Embodiment 1 of the present invention. This embodiment is used in network communication to prevent the situation that a sudden increase in the traffic of a certain request causes the service party to be instantly overwhelmed by the sudden increase in traffic. The method can be executed by the load balancing device provided by the embodiment of the present invention, and the device can be integrated into a device for network communication. see figure 1 , the method specifically includes:
[0026] S101. Determine a candidate server of a target request to be sent based on a hash algorithm.
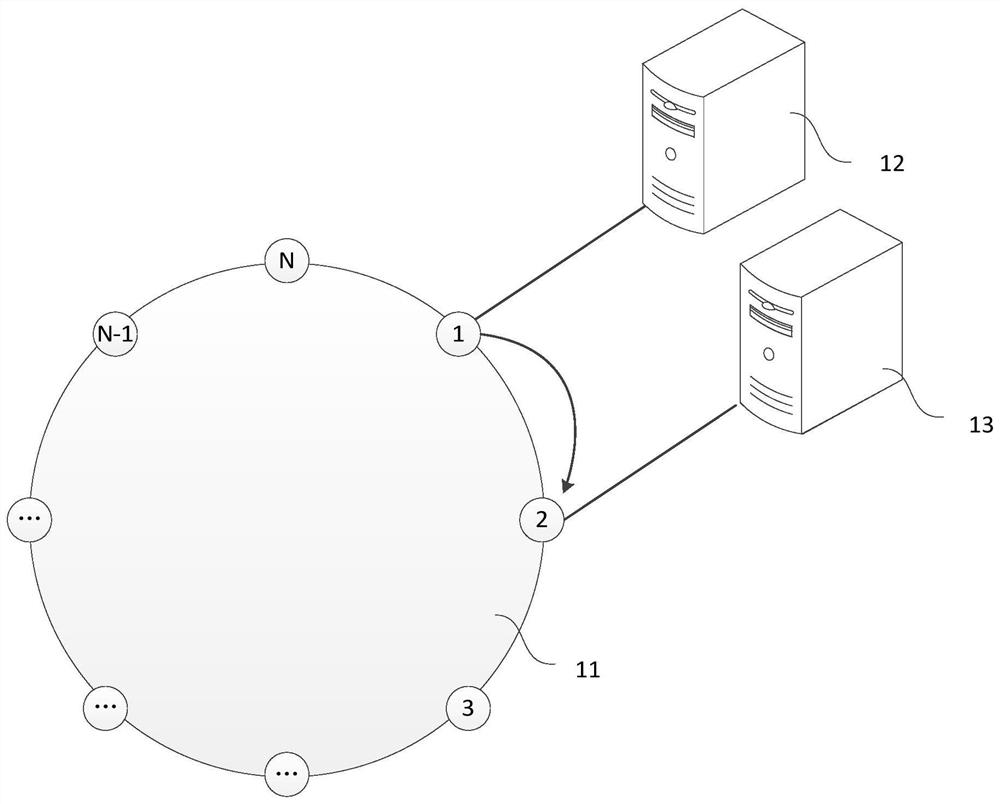
[0027] Among them, the hash algorithm is also called the hash algorithm, which maps a binary value of any length to a shorter fixed-length binary value. Like a fingerprint, it is a sign that uses shorter information to ensure the uniqueness of a file. Flags are associated with every byte of the file, and it's hard to...
Embodiment 2
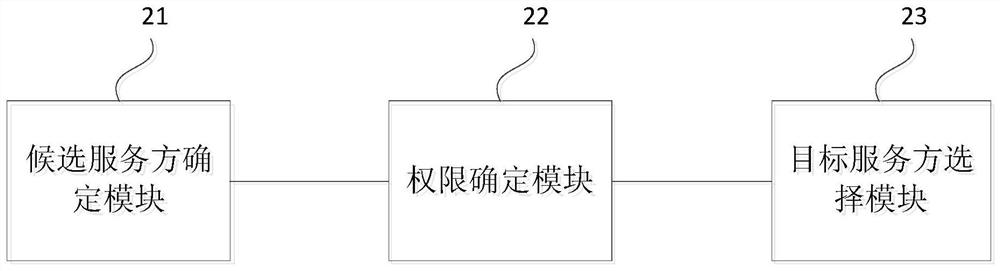
[0038] image 3 It is a schematic structural diagram of a load balancing device provided in Embodiment 2 of the present invention. The device can execute the load balancing method provided in any embodiment of the present invention, and has corresponding functional modules and beneficial effects for executing the method. Such as image 3 As shown, the device may include:
[0039] Candidate service party determination module 21, for determining the candidate service party of the target request to be sent based on the hash algorithm;
[0040] An authority determination module 22, configured to determine whether the local request initiator has the authority to access the candidate server;
[0041] A target server selection module 23, configured to select a target server from the servers with which the local requester has access authority, and send the target request to the target server.
[0042] On the basis of the above-mentioned embodiments, the target server selection modu...
Embodiment 3
[0047] Figure 4 A schematic structural diagram of a load balancing device provided by Embodiment 3 of the present invention, as shown in Figure 4 As shown, the load balancing device includes a processor 30, a memory 31, an input device 32 and an output device 33; the number of processors 30 in the load balancing device may be one or more, Figure 4 Take a processor 30 as an example; the processor 30, memory 31, input device 32 and output device 33 in the load balancing device can be connected by bus or other methods, Figure 4 Take connection via bus as an example.
[0048] The memory 31, as a computer-readable storage medium, can be used to store software programs, computer-executable programs and modules, such as program instructions / modules corresponding to the load balancing method in the embodiment of the present invention (for example, the candidate server determination module 21, Authority determination module 22 and target server selection module 23). The processo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com