Method and device for processing false user recognition, equipment and storage medium
A technology for user identification and processing methods, applied in the field of equipment and storage media, devices, and processing methods for false user identification, can solve problems such as inaccurate identification, and achieve the effect of reducing false traffic and improving real validity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] This embodiment provides a processing method for false user identification, which is used to judge the authenticity of users who generate data traffic, so as to improve the authenticity of data traffic. The execution subject of this embodiment is a processing device for false user identification, and the device can be set in a computing device, such as a computing device such as a computer or a server.
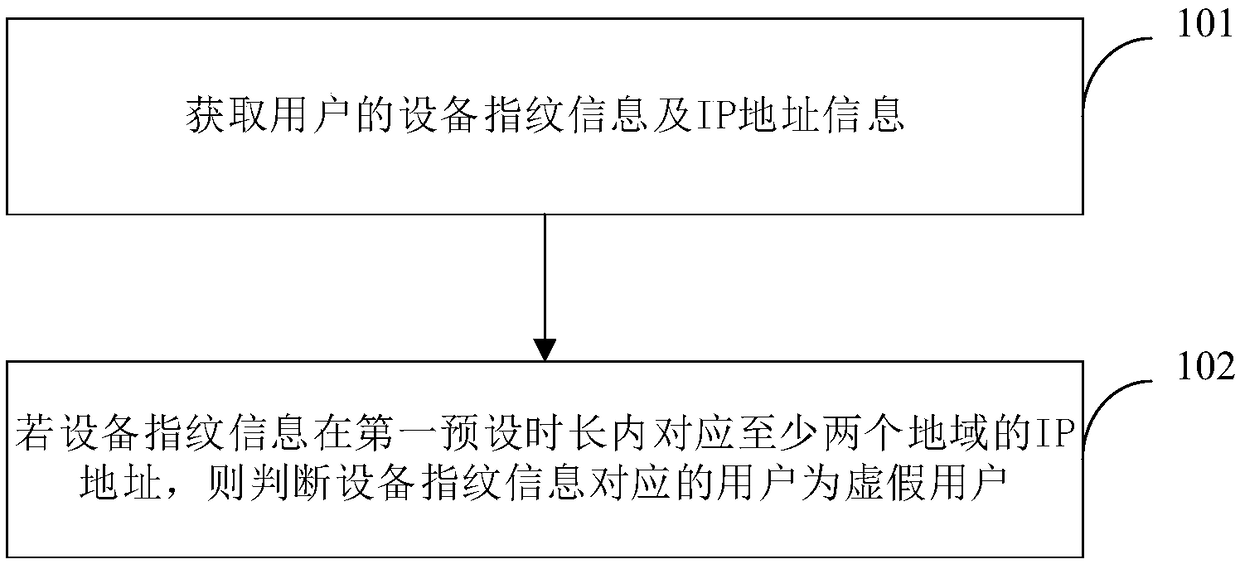
[0057] Such as figure 1 As shown, it is a schematic flow chart of the processing method for false user identification provided in this embodiment, the method includes:
[0058] Step 101, acquiring user's device fingerprint information and IP address information.
[0059] Specifically, the device fingerprint information is the unique device fingerprint information planted directly by embedding executable code in the application program APP. When the user accesses the server through the APP on the client side, the server can obtain the user's device fingerprint informati...
Embodiment 2
[0069] This embodiment provides a further supplementary description of the method provided in the first embodiment.
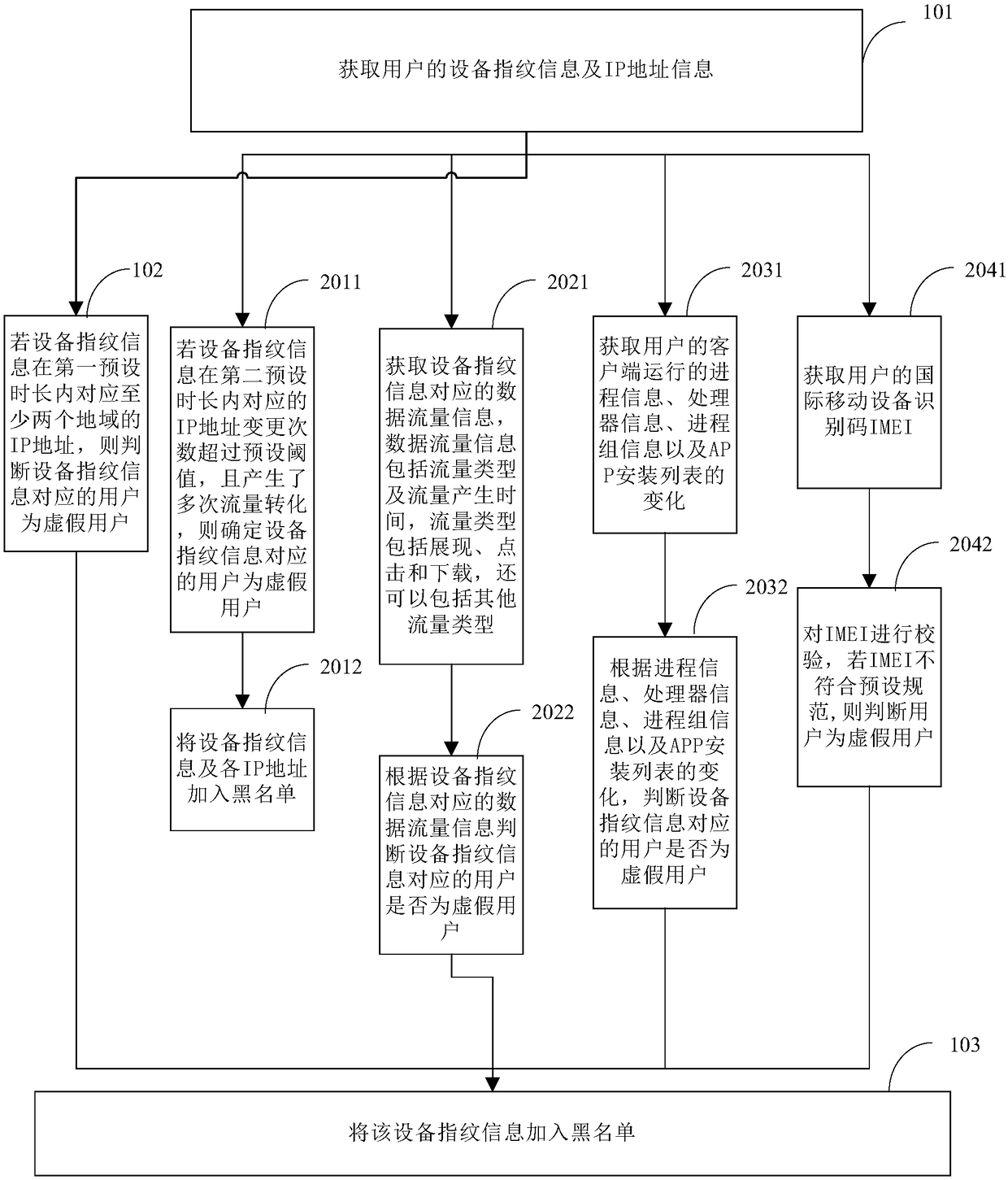
[0070] Such as figure 2 As shown in , it is a schematic flowchart of the processing method for false user identification provided in this embodiment.
[0071] As an implementable manner, on the basis of the first embodiment above, optionally, the method may further include:
[0072] Step 2011, if the number of IP address changes corresponding to the device fingerprint information within the second preset time span exceeds a preset threshold and multiple traffic conversions occur, then determine that the user corresponding to the device fingerprint information is a fake user.
[0073] Step 2012, adding device fingerprint information and IP addresses to the blacklist.
[0074] Specifically, if within a period of time (the second preset duration), the IP address of the device corresponding to the fingerprint information of the same device often changes, and the...
Embodiment 3
[0125] This embodiment provides a device for processing false user identification, which is used to execute the method in the first embodiment above.
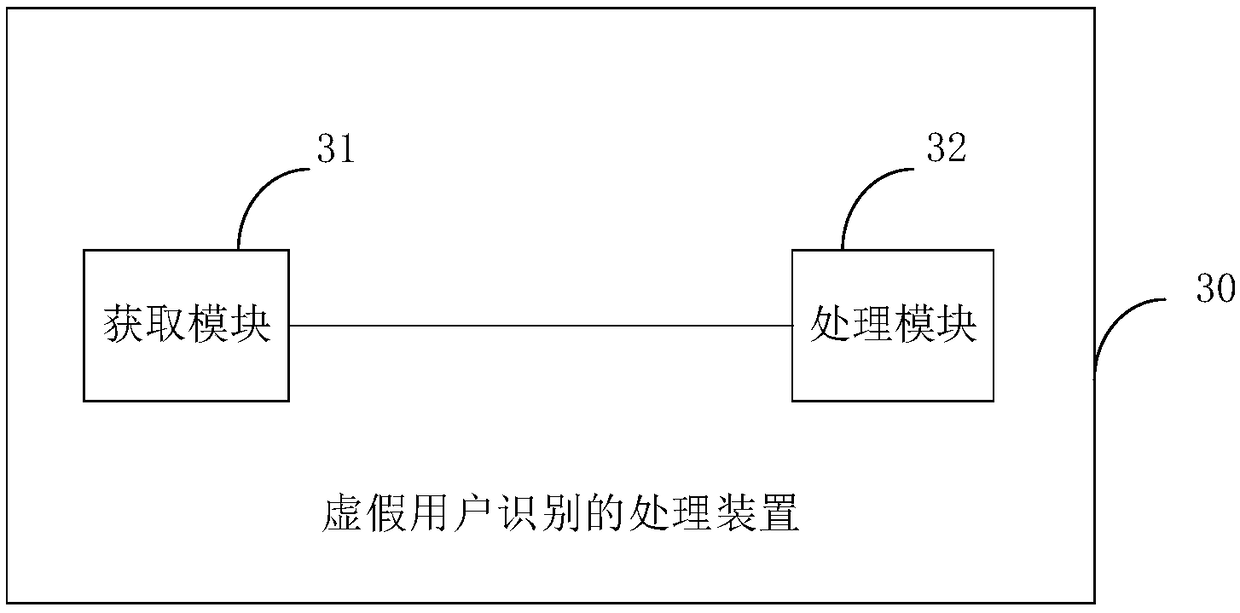
[0126] Such as image 3 As shown in , it is a schematic structural diagram of a processing device for false user identification provided in this embodiment. The device 30 for processing false user identification includes an acquisition module 31 and a processing module 32 .
[0127] Among them, the obtaining module 31 is used to obtain the user's device fingerprint information and IP address information; the processing module 32 is used to determine the IP address corresponding to the device fingerprint information if the device fingerprint information corresponds to at least two regional IP addresses within the first preset time length. The user is a fake user.
[0128] Regarding the apparatus in this embodiment, the specific manner in which each module executes operations has been described in detail in the embodiment of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com