A daemon wallet block chain private key storage and encryption method
An encryption method and blockchain technology, applied in the field of master wallet blockchain private key storage and encryption, can solve problems such as theft of blockchain assets, and achieve the effect of avoiding data insecurity and loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
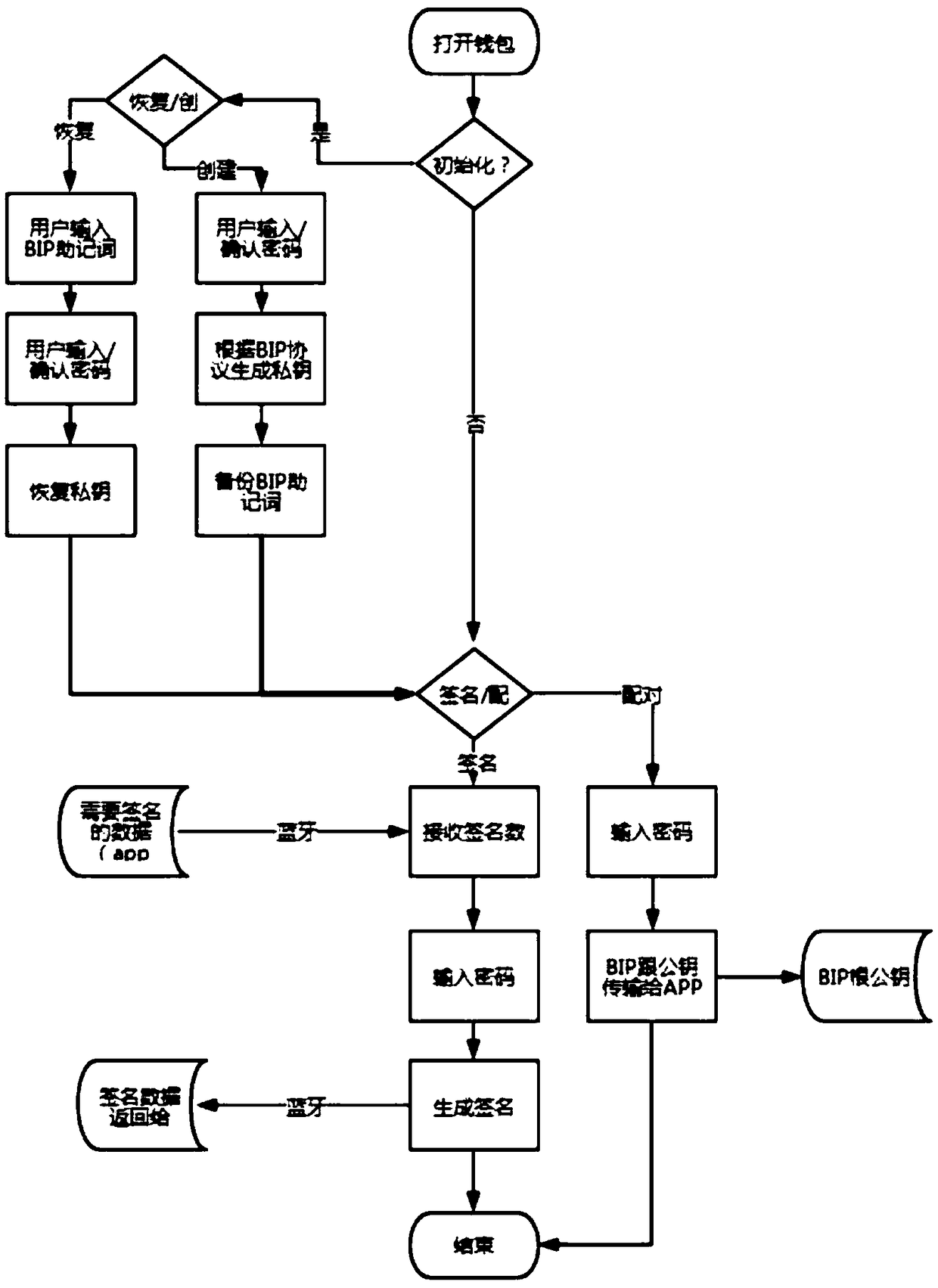
[0026] Example 1: See figure 1 , a block chain private key storage and encryption method of the master wallet, the master wallet includes a hot wallet and a hardware wallet, and the encryption method specifically includes the following steps:
[0027] A. The user opens the hardware package and enters the pin code;
[0028] B. The system generates random seeds and BIP mnemonic words; and uses AES and user Pin code encryption, while BIP mnemonic words are encoded in utf8,
[0029] C. The hot wallet initiates a transaction, and the hot wallet obtains the data NeedSignData that needs to be signed;
[0030] D. The hot wallet generates a QR code based on NeedSignData;
[0031] E. The hardware wallet scans this QR code;
[0032] F. The user enters the Pin code in the hardware wallet;
[0033] G. DEAES decoding to obtain the mnemonic;
[0034] H. The hardware wallet obtains the private key according to the Path information in the QR code, uses the private key to sign NeedSignData...
Embodiment 2
[0037] Embodiment 2, on the basis of Embodiment 1, after the transaction is completed, the hardware wallet will cancel the memory. Finally end the transaction process. This helps free up memory and speeds up processing.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com