A defense method and system against short message interception attack
A short message and user technology, applied in the computer field, can solve problems such as inconvenient portability, reduced user experience due to security, poor user experience, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
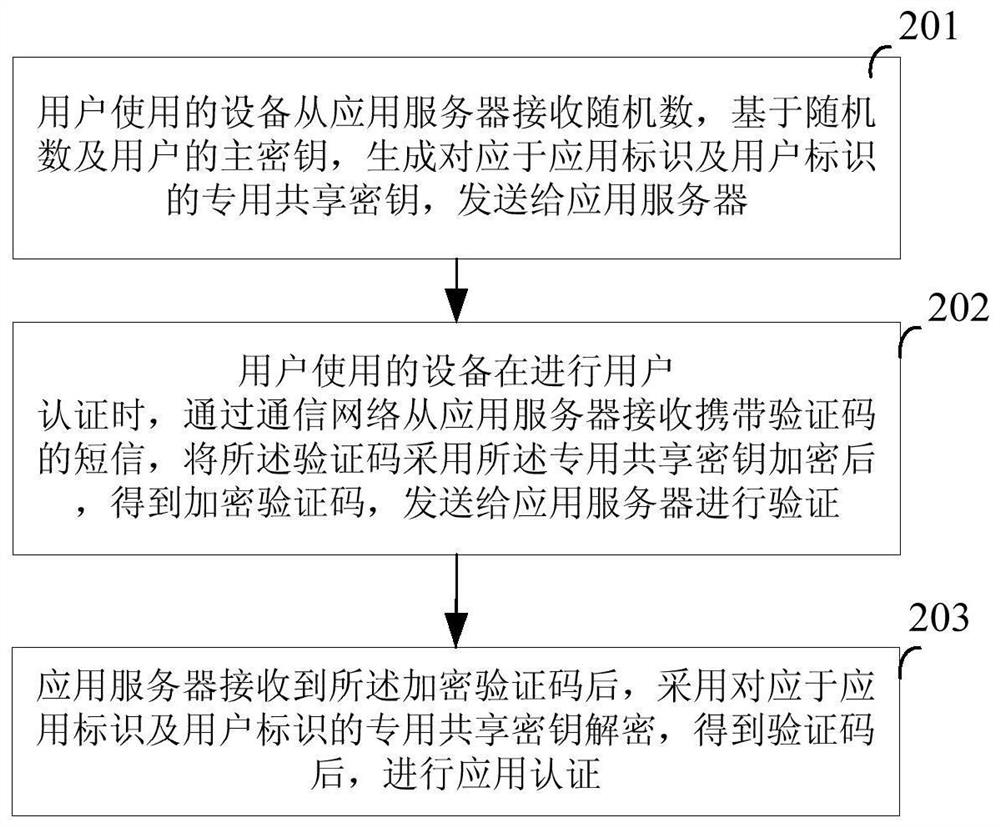
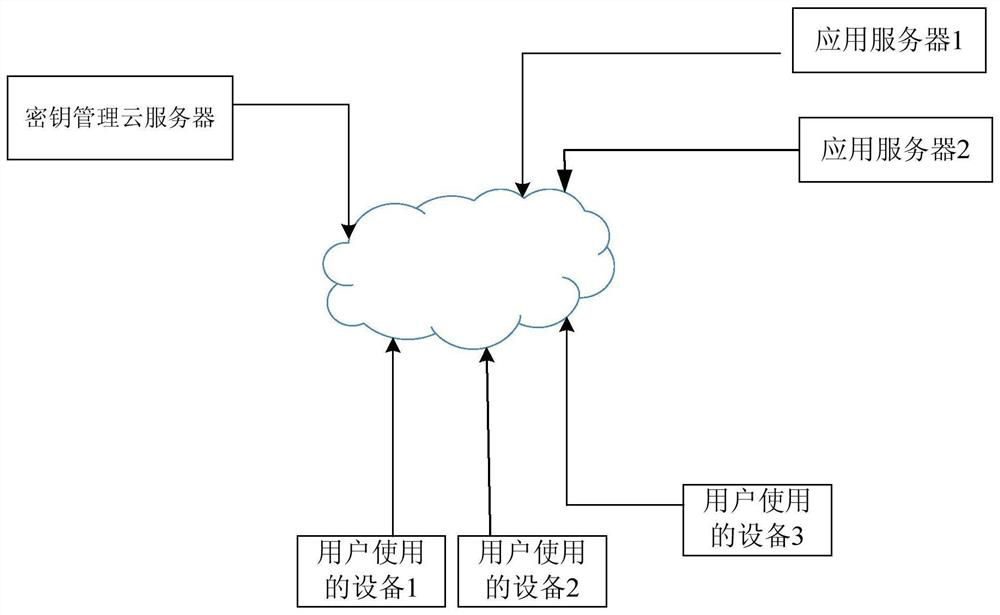
[0035] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
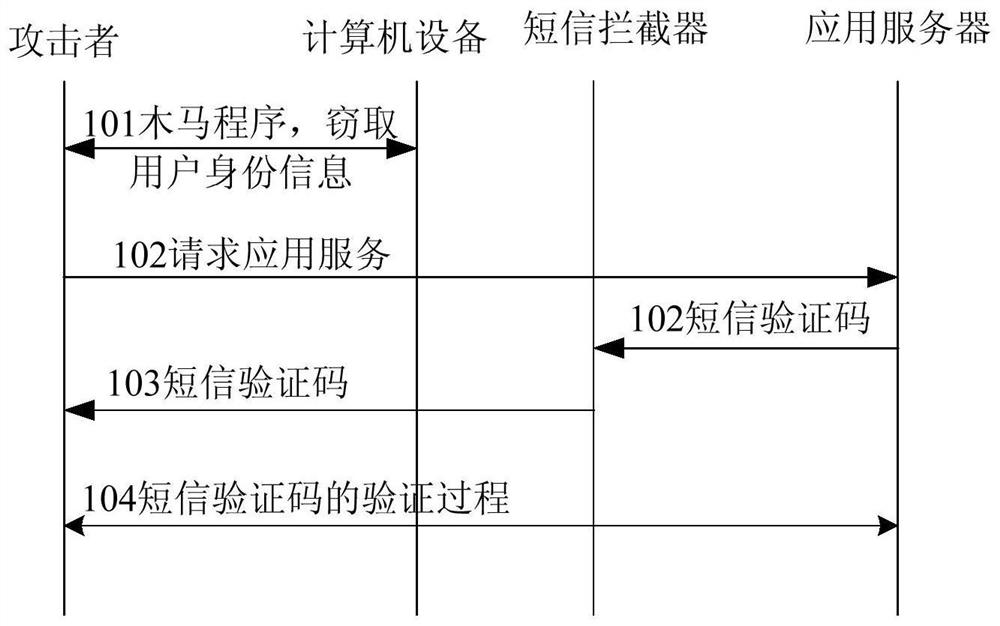
[0036] It can be seen from the background technology that the application adopts the verification code carried by the short message for verification, which depends on the security of the communication network. However, with the deregulation of the communication network, the inherent defects of SS7 will lead to the inability to guarantee the security of SMS sent by SS7. As long as the user's access right is obtained, the SMS sent to the user can be intercepted . Communication network providers set up firewalls in the communication network. Although such threats can be mitigated to a certain extent, they cannot be eradicated. On the other hand, the application server uses the verification code carried in the short message to verify the user, which is the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com