Anti-quantum-computing blockchain secret transaction system and anti-quantum-computing blockchain secret transaction methods based on P2P (Peer-to-Peer) symmetric key pools
A technology of quantum computing and transaction methods, applied in the field of blockchain, which can solve the problems of unencrypted, cracked, and occupied blockchain transmission and storage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
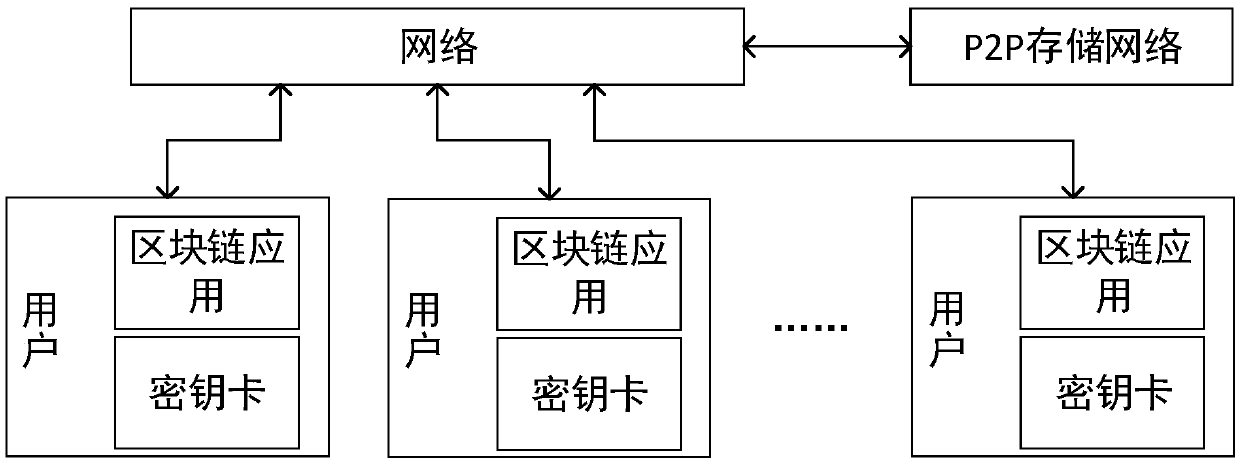
[0038] The system structure is as figure 1 As shown, each user, as a node of the blockchain, has a corresponding blockchain application and is equipped with a key card. There are u key cards, and each key card stores the user's public key PK and private key SK; the key card is called by the blockchain application, and the key does not come out of the key card.
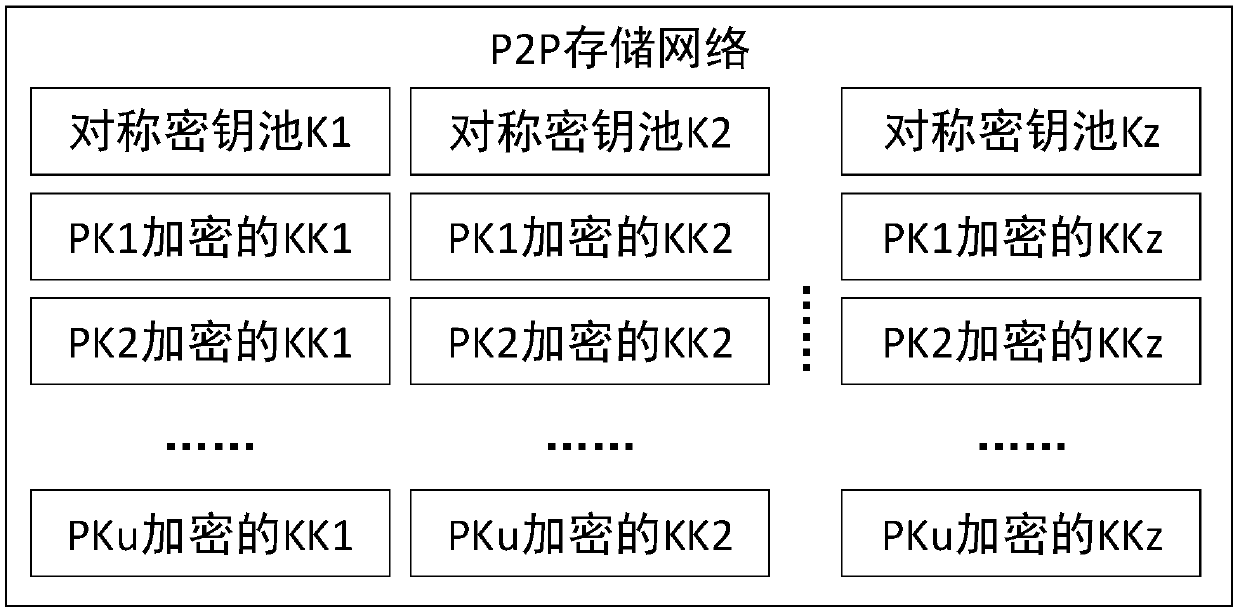
[0039] P2P storage network structure such as figure 2 As shown, there are z symmetric key pools whose ID is KID=Ki (i=1~z). The symmetric key pools are respectively encrypted with z symmetric keys KKi (i=1~z), all of which are true random numbers, preferably quantum random numbers. Each KKi (i=1~z) is encrypted by u PKi (i=1~u). All data in the P2P storage network is uploaded by the user or the key card issuer, and the P2P storage network cannot be decrypted.
[0040] The specific steps of the transaction are as follows:
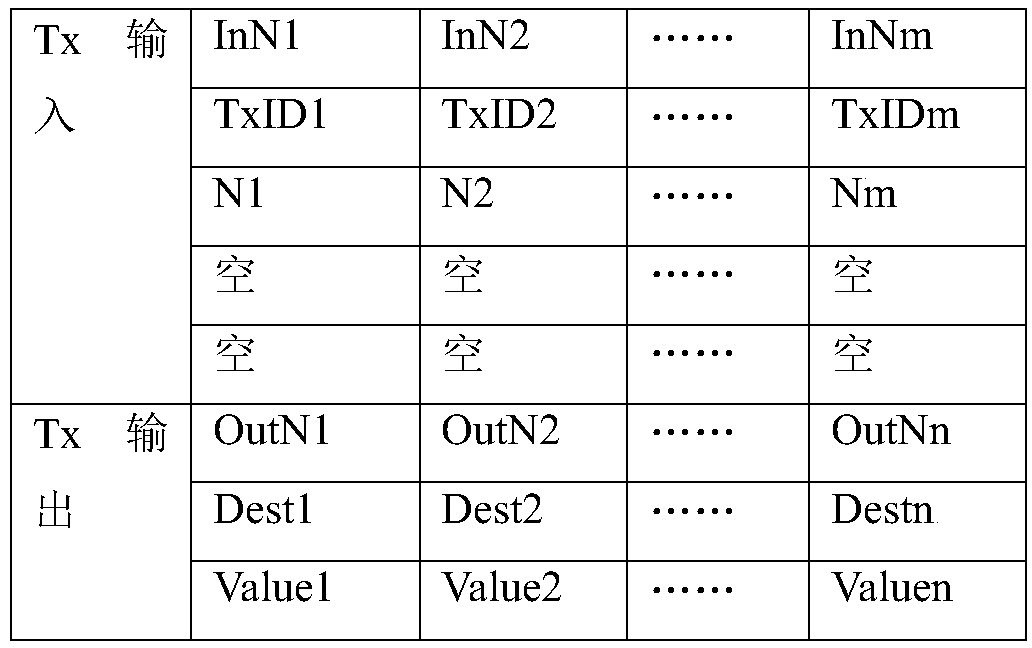
[0041] Step 1.1 generate unsigned transaction RTx:;
[0042] Before initiating a transacti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com