URL virtualization dynamic defense method for automatic attacks
A dynamic defense and server technology, applied in the field of network security, can solve the problems of fixed defense direction and inability to effectively deal with hacker attack methods and methods, so as to increase the difficulty and cost of attacks, solve unknown attacks, and increase attack costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
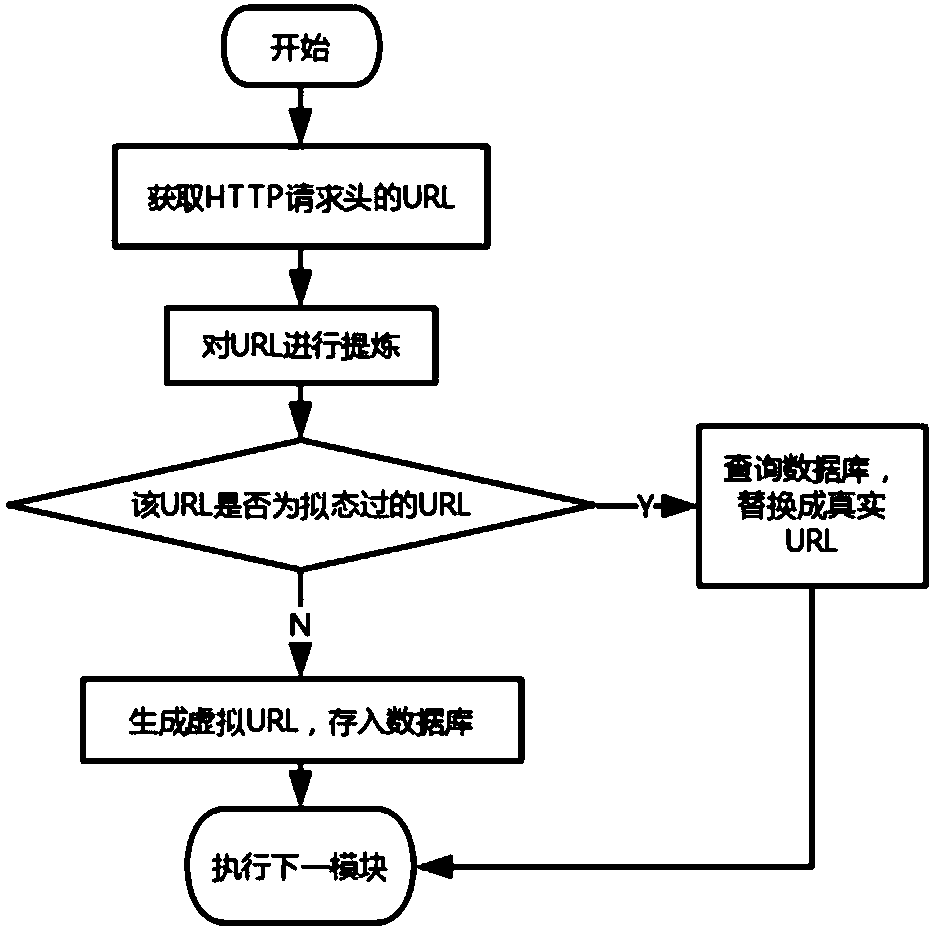
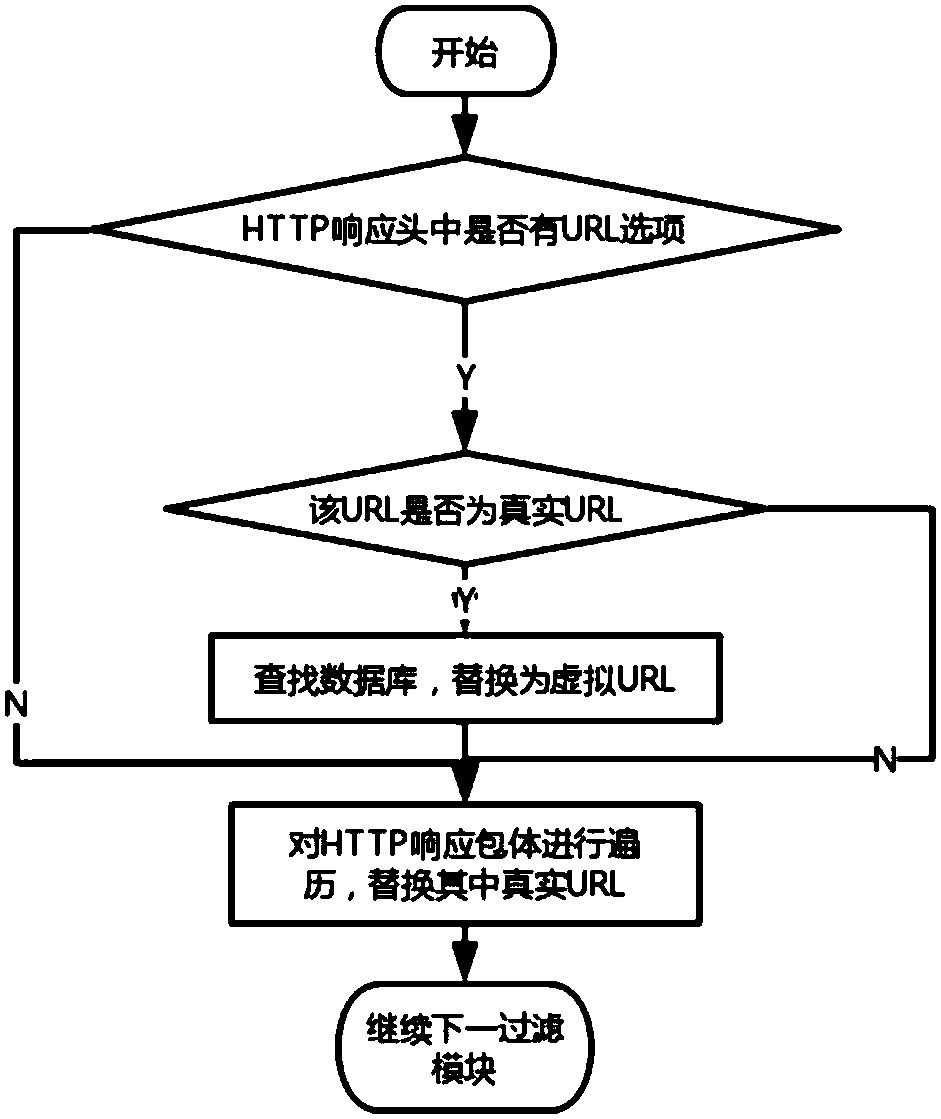
[0016] Such as figure 1 , 2 As shown, the present invention provides a URL virtualization dynamic defense method against automated attacks. Network defense is an important content in the field of computer security. The specific content includes two steps: the client request processing step and the server response processing step.
[0017] Now suppose a client requests a certain website, and the server sends a normal access response message:
[0018] HTTP / 1.1 200 OK
[0019] Date: Sat, 31Dec 2005 23:59:59GMT
[0020] Content-Type: text / html; charset=ISO-8859-1
[0021] Content-Length: 122
[0022]
[0023]
[0024] Wrox Homepage
[0025]
[0026]
[0027]
[0028]
[0029]
[0030] 1. Client request processing steps Process the http request sent by the client to the server. This step is achieved through the following sub-steps:
[0031] 1. The server obtains URL information;
[0032] When there is a URL in the HTTP request, the URL appears in the HTTP re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com