Device of terminal network access control system and implementation method
A technology of access control and terminal network, applied in the direction of transmission system, electrical components, etc., can solve problems such as data loss, easy to be ignored, system intrusion, etc., to improve processing speed, reduce repetitive and unnecessary processing, and ensure security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
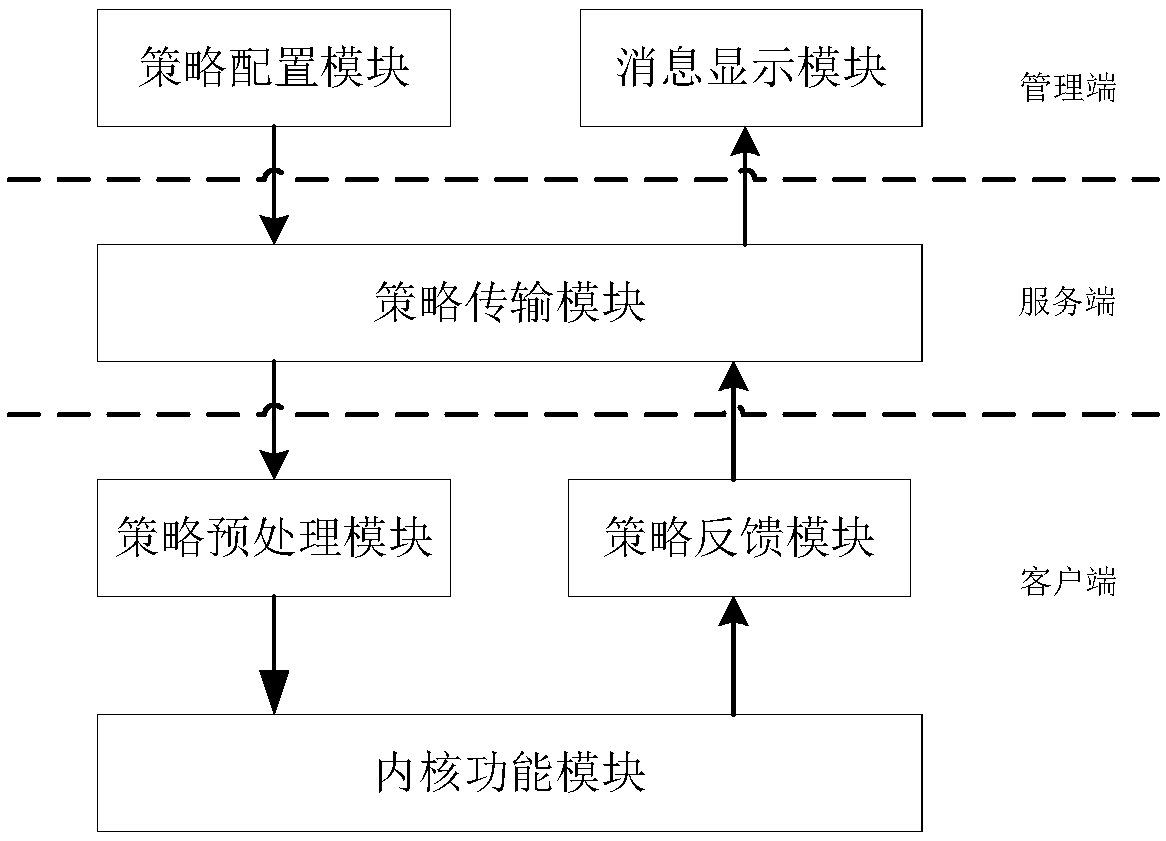
[0053] as attached figure 1As shown, the device of the terminal network access control system of the present invention mainly includes a management terminal, a server terminal and a client terminal. The management terminal is used to configure the terminal network access strategy in real time and audit logs for network access. display information; the server is used to configure policies and transmit audit information, including sending the policies configured by the management end to the client and passing the audit logs generated by the client to the management end; the client is used to parse and store the server According to the policy sent, the data packet is processed accordingly according to the pre-processed configuration policy, and the corresponding audit log is generated according to the processing result and sent to the server.
[0054] Among them, the management terminal includes a policy configuration module and a message display module; the management terminal i...
Embodiment 2
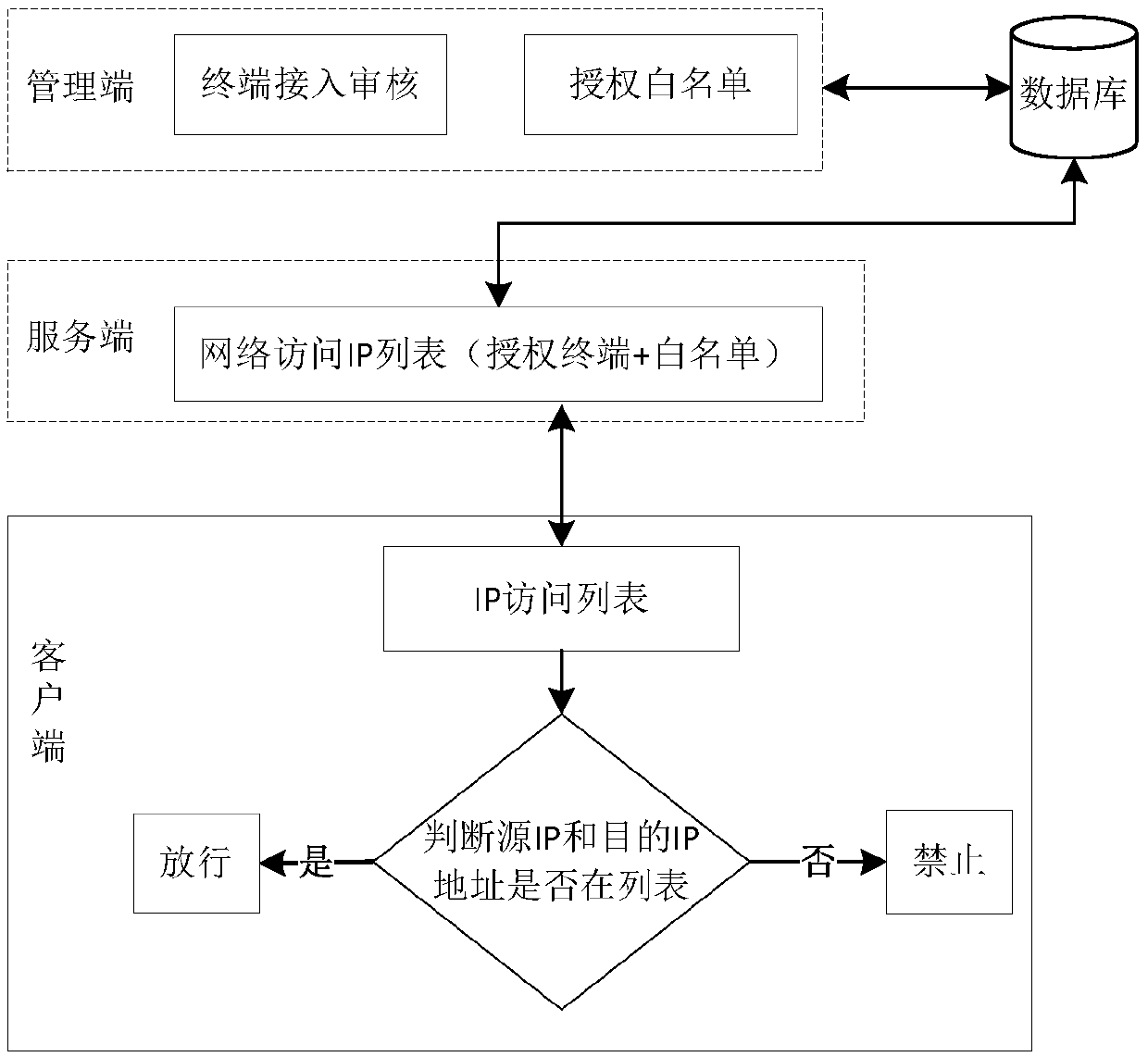
[0071] as attached figure 2 As shown, the implementation method of the terminal network access control system of the present invention, the method steps are as follows:
[0072] S1. The terminal registers after installing the client program, submits the basic information of the terminal to the server, the server stores the basic information of the terminal in the database, and the management terminal conducts a network access audit on the terminal, assigns or modifies network access policies, and notifies the server;
[0073] S2. The server queries the database to generate a network access control strategy IP list, and the IP list only includes the terminal IP addresses authorized to allow access and the authorized whitelist IP addresses;
[0074] S3. The server notifies the client to update the network access control IP list;
[0075] S4. The client judges whether the source IP address and the destination IP address are in the IP list:
[0076] ①, if yes, execute step S5; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com