Ciphertext domain reversible-data-hiding (RDH) method based on left and right shifting of histogram
A technology of information hiding and histogram, which is applied in image communication and key distribution, can solve the problems of high embedding rate, high reversible security, non-expansion or small expansion of encrypted data, and limited application breadth. The effect of high practical significance and good safety guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the method of the present invention will be further described in detail below in conjunction with specific implementation methods and accompanying drawings.
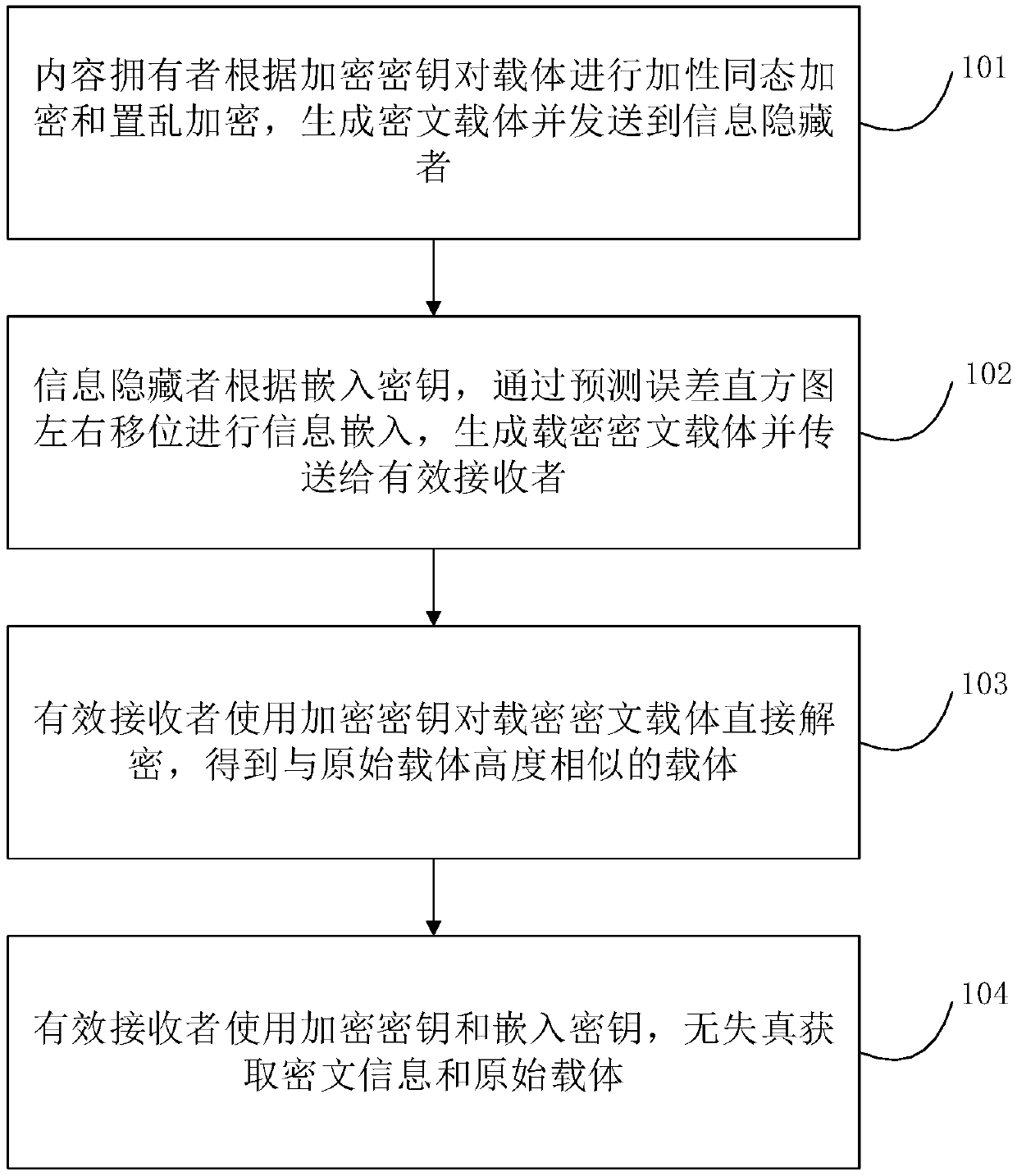
[0022] like figure 1 As shown, the ciphertext domain reversible information hiding method based on the left and right shift of the histogram of the present invention comprises the following steps:
[0023] Step 101, encryption stage: the content owner performs additive homomorphic encryption and scrambling encryption on the carrier according to the encryption key, generates a ciphertext carrier and sends it to the information hider. The specific steps are as follows:
[0024] A1. The carrier is divided into blocks, and the original carrier data stream with a length of R×C is stored as a matrix X, X={x r,c |r=1, 2,..., R, c=1, 2,..., C}, divide the matrix into I×J non-overlapping sub-blocks X i,j , X i,j ={...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com