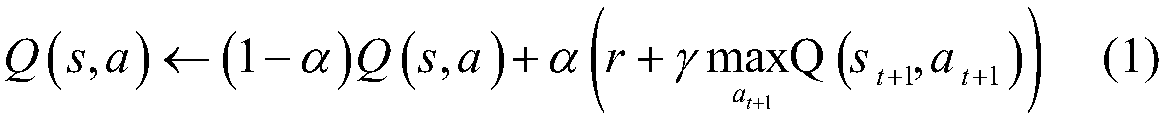DDoS attack detection based on hidden Markov and Q-learning cooperation
An attack detection and learning algorithm technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as low accuracy, link congestion, increased data transmission delay, and incomplete response.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
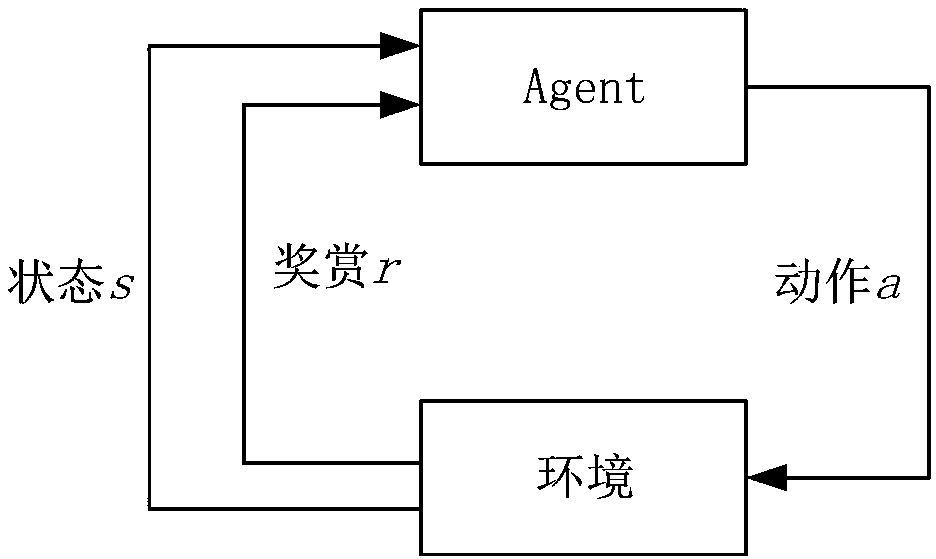
Method used
Image
Examples
Embodiment Construction
[0039] The present invention is explained and elaborated below in conjunction with relevant accompanying drawings:
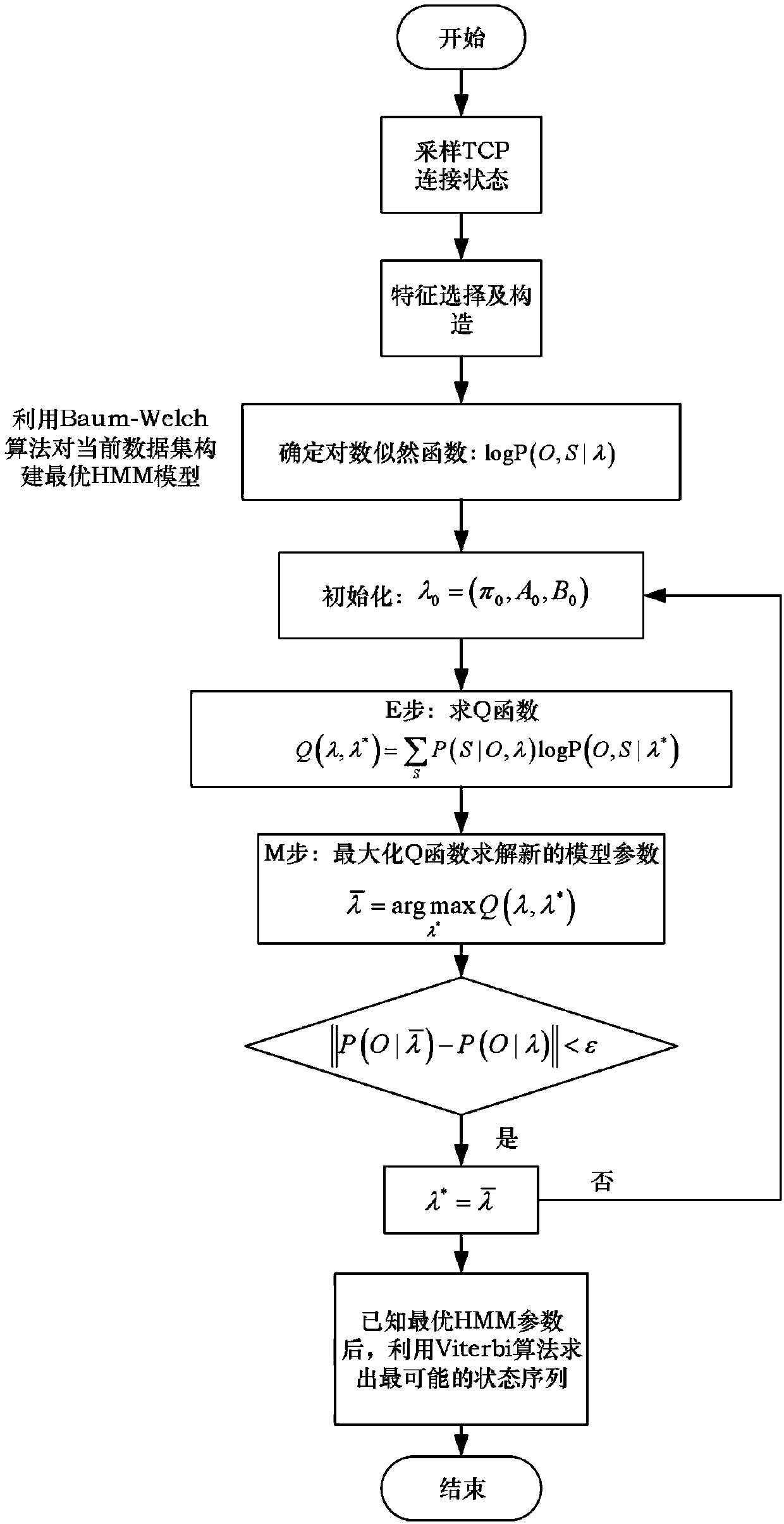
[0040] In order to make the object, technical solution and features of the present invention clearer, the present invention will be further described in detail below in conjunction with specific implementation examples and with reference to the accompanying drawings. The overall frame diagram of the method of the present invention is as figure 1 shown. The flow of each step is described as follows:
[0041] 1) Grab the feature representation based on the TCP connection state from the network data stream;
[0042] 2) Count the number of normal and abnormal network connection states, and show the probability matrix between the state and the observed value;
[0043] 3) Use the Baum-Welch algorithm in the hidden horse model to iteratively establish and train the optimal HMM model parameters;
[0044] 4) After training the single-point detection model, use distri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com