A high-security computer system based on lockstep and monitoring and its design method
A computer system, high-security technology, applied to the generation of response errors, error detection of redundant data in hardware, etc., can solve the problems of undetectable common mode faults, coarse contrast granularity, undetectable errors, etc., to achieve The effect of solving speed mismatch, reducing time and improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0033] In order to make those skilled in the art better understand the present invention, the present invention will be further explained below with reference to the accompanying drawings and in conjunction with the implementation process. It should be noted that the implementation process is only used to explain the invention, and is not used to limit the invention.
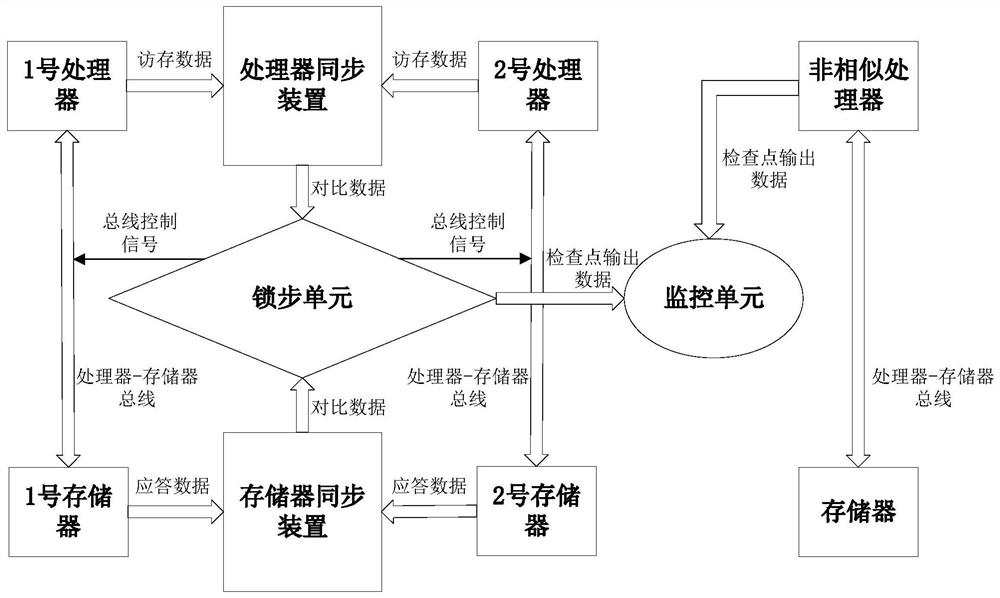
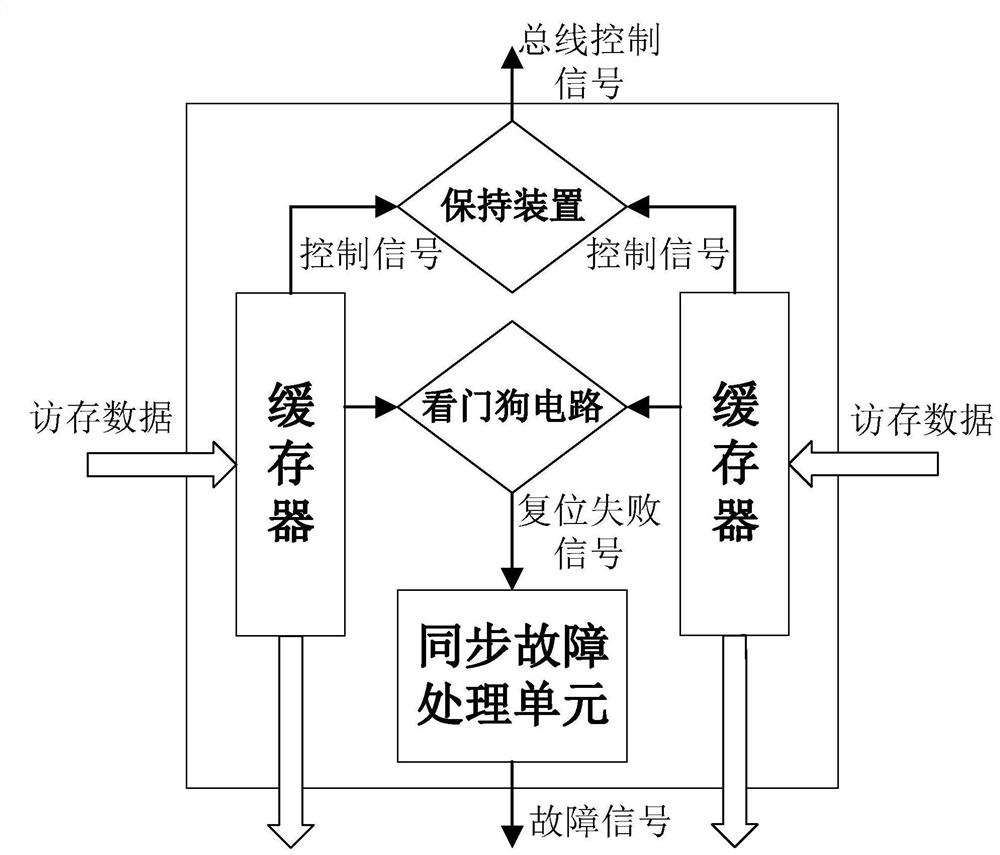
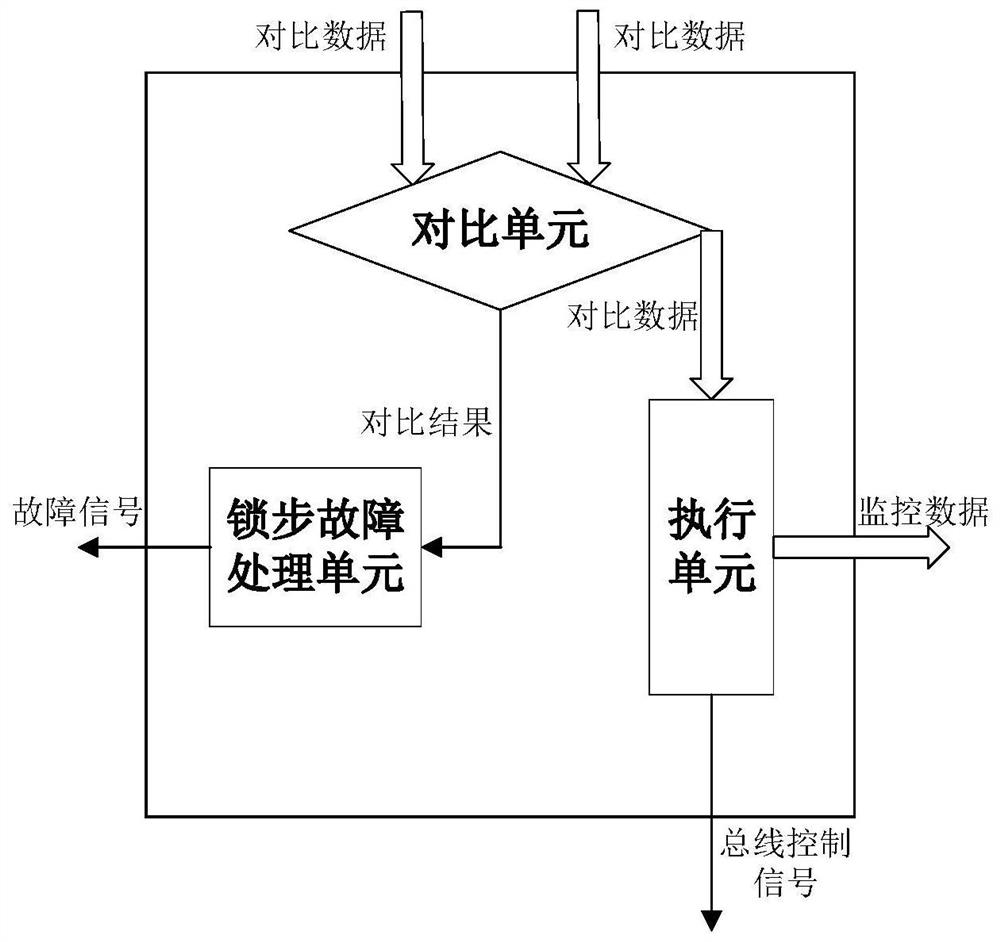
[0034] A high-security computer system based on lockstep plus monitoring, comprising a lockstep module and a monitoring module, wherein the lockstep module comprises a No. 1 processor, a No. 2 processor, a No. 1 memory, a No. 2 memory, a processor synchronization device, A memory synchronizing device and a lock-step unit, the monitoring module includes a dissimilar processor that adopts a different instruction set from the lock-step module, a No. 3 memory and a monitoring unit.
[0035]I...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com