Resource locking algorithm for memory read-write process
A memory resource and algorithm technology, applied in the field of resource locking algorithms in memory read and write processes, can solve problems such as affecting the number of concurrency, occupying operating system CPU resources, system deadlock, etc., to improve the number and efficiency of concurrency, improve scalability, The effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
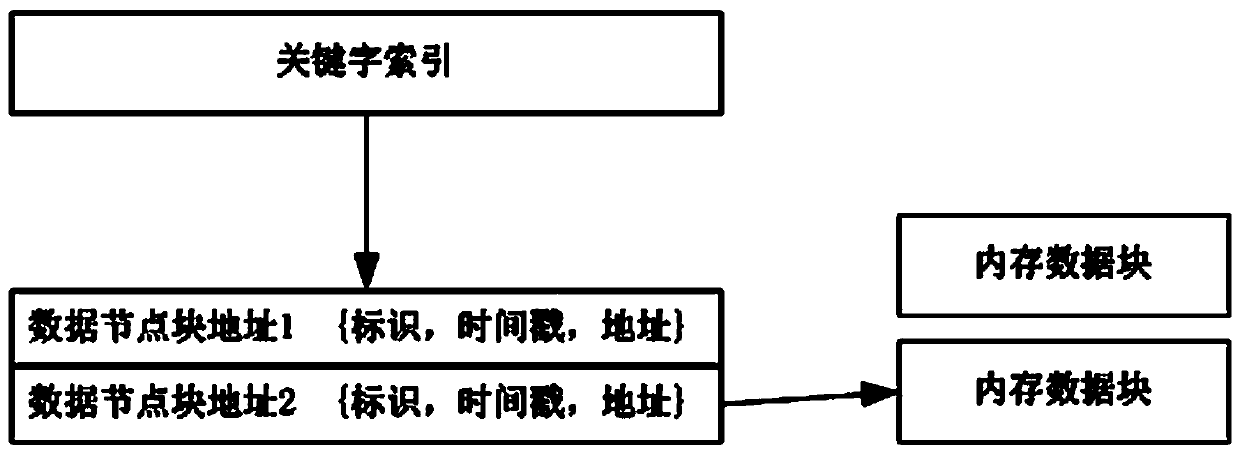
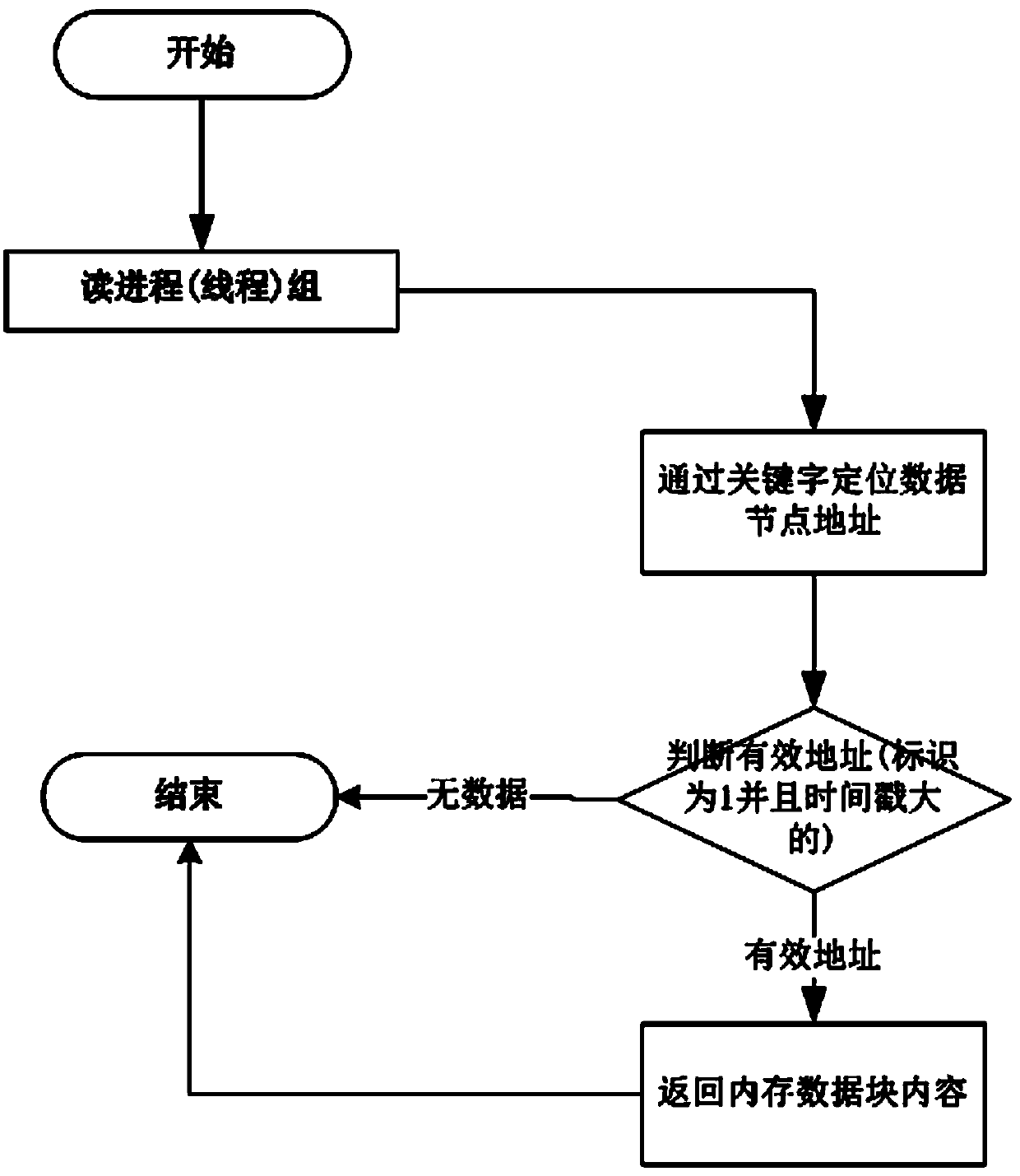
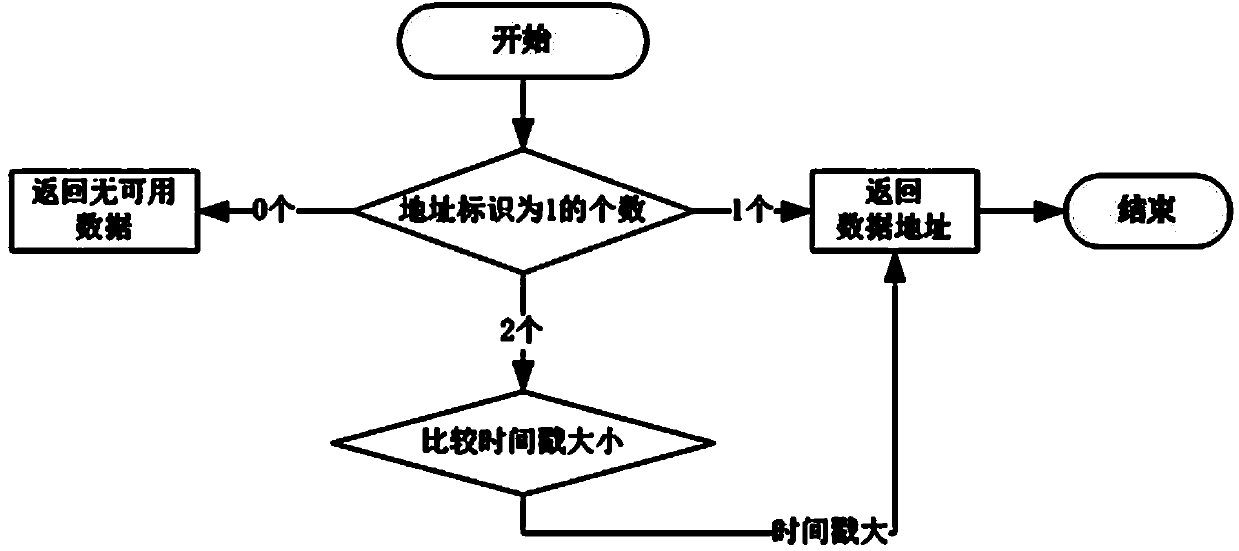
[0067] In the web server using the resource locking algorithm, the server caches the content of the web page in the memory so as to quickly respond to the customer's access requirements. When a web page needs to be modified and maintained, the resource locking algorithm finds the memory space S corresponding to the web page. Copy the data blocks in the memory space to form a mirror space L containing the webpage. During the modification and maintenance period, external customers' access to the webpage is uniformly directed to the original memory space S, and the permissions of the mirror space L are modified to only Write, for write process operations only.
[0068] The timestamp of the memory data structure in the memory space S is a millisecond-level timestamp.
[0069] After the maintenance and modification of the web page is completed, the resource locking algorithm modifies the permission of the mirror space L to read-only, and redirects the access of external customers t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com