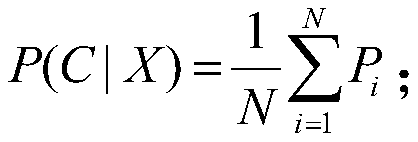Three-branch identity authentication method and system based on mouse behaviors
An identity authentication and mouse technology, applied in the field of identity authentication, can solve the problems of wasting time and high authentication time, achieve the desired effect of low false rejection rate and false acceptance rate, and reduce authentication time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
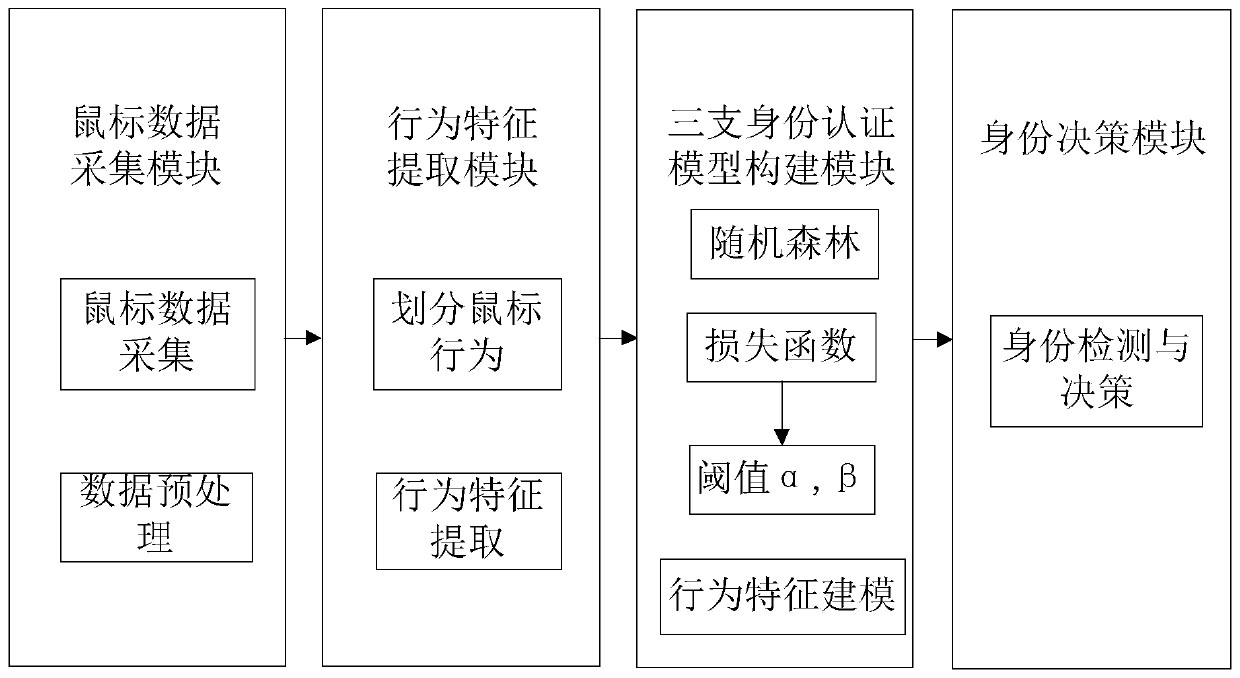
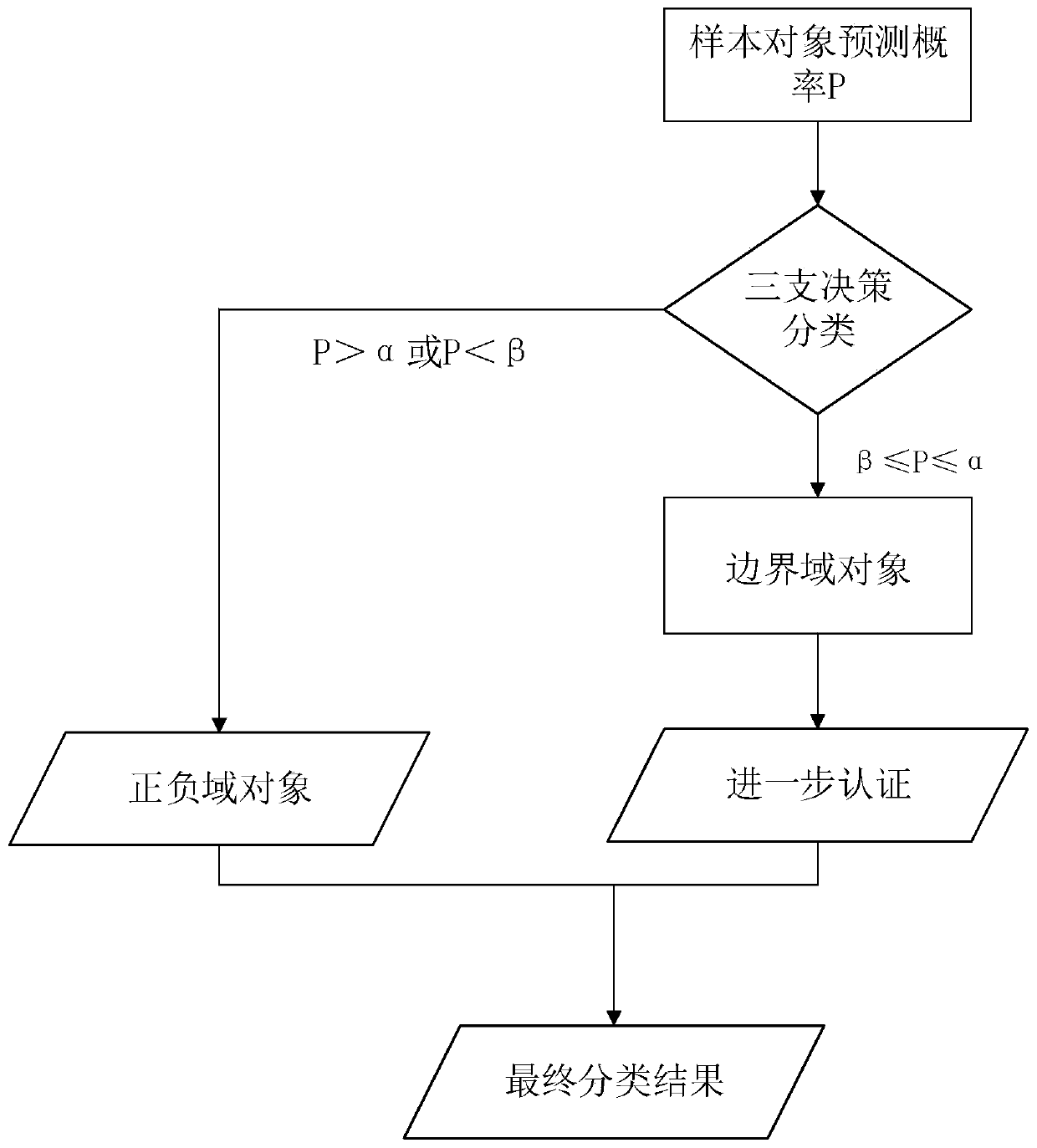
Method used
Image
Examples
Embodiment 2
[0104] This embodiment will further illustrate the application of the three identity authentication models proposed by the present invention in identity authentication;
[0105] The data used in this embodiment is the public data set provided by Balabit as the collected mouse data, and part of the data is shown in Table 1.
[0106] First, data preprocessing is performed on the original data to delete duplicate data, abnormal data, etc.
[0107] According to the mouse behavior and feature calculation method introduced above, the required mouse feature values are calculated and used as model training data. The calculated eigenvalues of the mouse part are shown in Table 3.
[0108] Table 3 Characteristic values of mouse data
[0109]
[0110] In order to avoid errors caused by unbalanced training data, the present invention selects 1000 legal mouse users and 1000 illegal mouse users as training data. Use the random forest algorithm as a classifier for training. And t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com