FPGA authorization verification method and device and processing equipment
A verification method and equipment code technology, which is applied in electrical digital data processing, computer security devices, software deployment, etc., can solve problems such as poor controllability, complicated material management and production process, and FPGA cannot be started
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
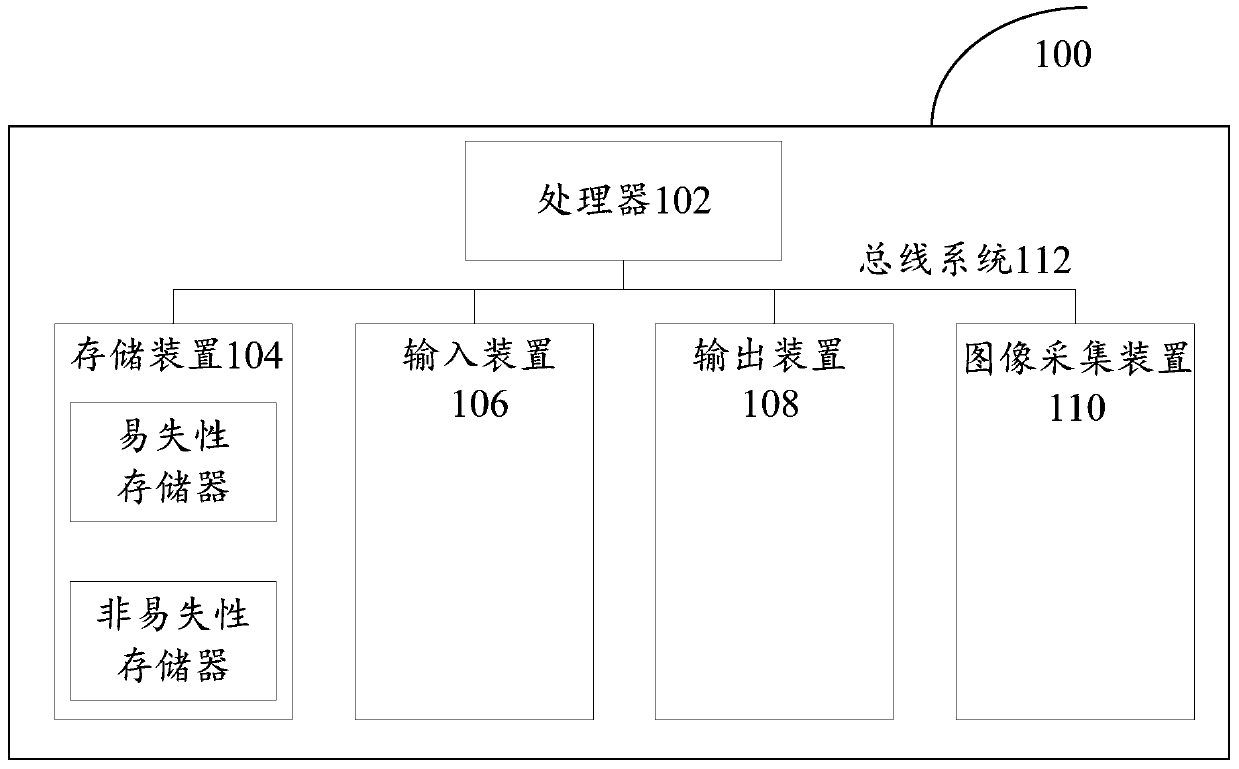
[0028] First, refer to figure 1 An example electronic device 100 for implementing the FPGA authorization verification method, device and processing device according to the embodiments of the present invention will be described.
[0029] Such as figure 1 Shown is a schematic structural diagram of an electronic device. The electronic device 100 includes one or more processors 102, one or more storage devices 104, an input device 106, and an output device 108. These components are connected via a bus system 112 and / or other forms of interconnected by a connecting mechanism (not shown). It should be noted that figure 1 The components and structure of the electronic device 100 shown are only exemplary, not limiting, and the electronic device may also have other components and structures as required.
[0030] The processor 102 can be implemented in at least one hardware form of a digital signal processor (DSP), a field programmable gate array (FPGA), and a programmable logic arra...
Embodiment 2
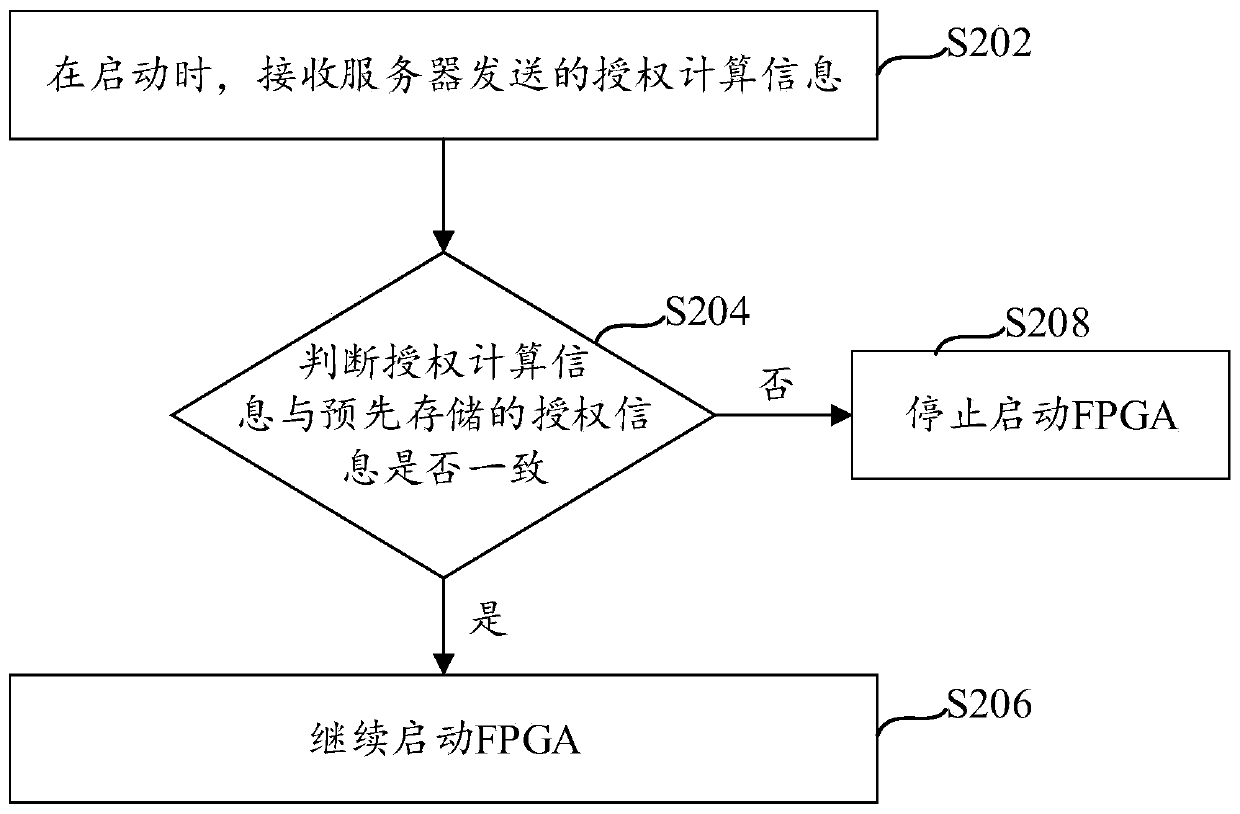
[0036] see figure 2 A flow chart of a FPGA authorization verification method shown, the method can be performed by the electronic device provided in the foregoing embodiment, and the method specifically includes the following steps:
[0037] Step S202, at startup, receiving authorization calculation information sent by the server. Wherein, the authorization calculation information is encrypted and calculated by the device code of the FPGA and the characteristic value of the function corresponding to the firmware.
[0038] When the FPGA chip is started, it is necessary to verify whether the current firmware is authorized firmware, and only when it is verified that it is authorized firmware can it continue to start and work on the chip. In order to distinguish FPGA chips with different functions, different authorization information may be set for different functions. At startup, the authorized computing information sent by the server can be received. The server can be a local s...
Embodiment 3
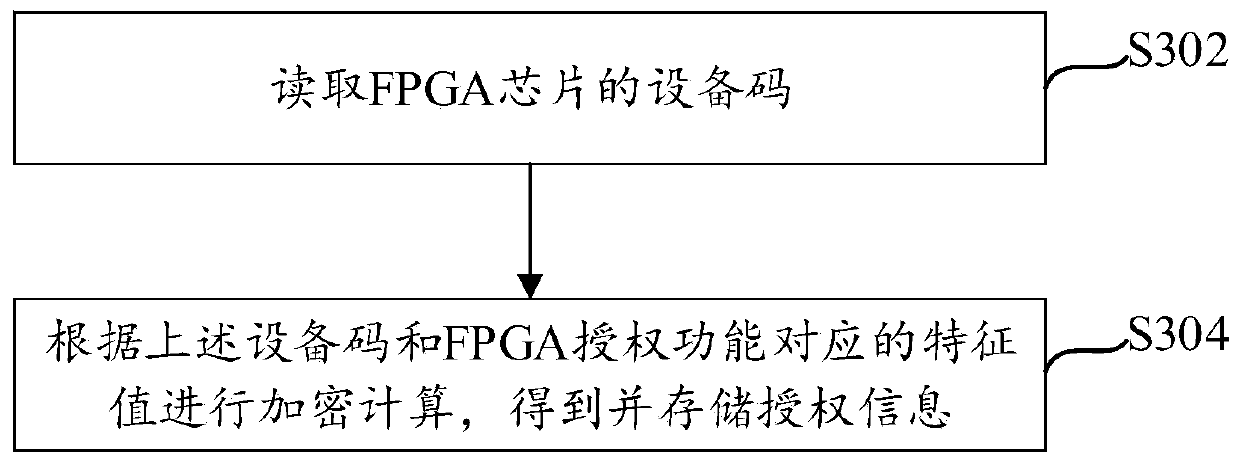
[0058] For the FPGA authorization verification method provided in Embodiment 2, the embodiment of the present invention provides an FPGA authorization verification device, see Figure 4 A structural block diagram of an FPGA authorization verification device shown, including:
[0059] The receiving module 402 is used to receive the authorized computing information sent by the server when starting; wherein, the authorized computing information is encrypted and calculated by the feature value corresponding to the device code of the FPGA and the function of the firmware;
[0060] Judgment module 404, used to judge whether the authorization calculation information is consistent with the pre-stored authorization information; wherein, the authorization information is encrypted and calculated by the feature value corresponding to the device code and the FPGA authorization function;
[0061] Start module 406, if consistent, continue to start FPGA;
[0062] Stop module 408, configured ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com