Identification method and device for high-risk transaction subject and server
A subject and transaction technology, applied in the computer field, can solve problems such as the scale of harm or loss, the loss of related companies, and disrupt the market order, and achieve the effect of ensuring normal operation, reducing losses, and maintaining market order.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
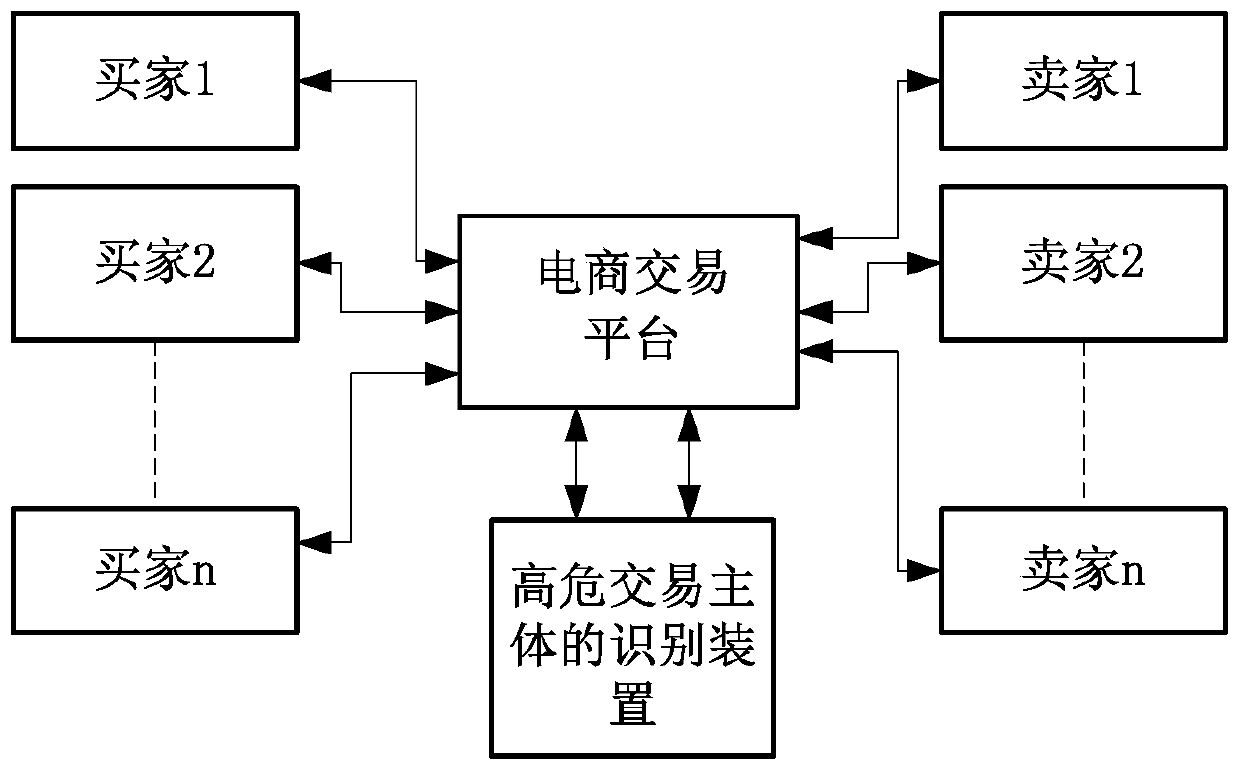
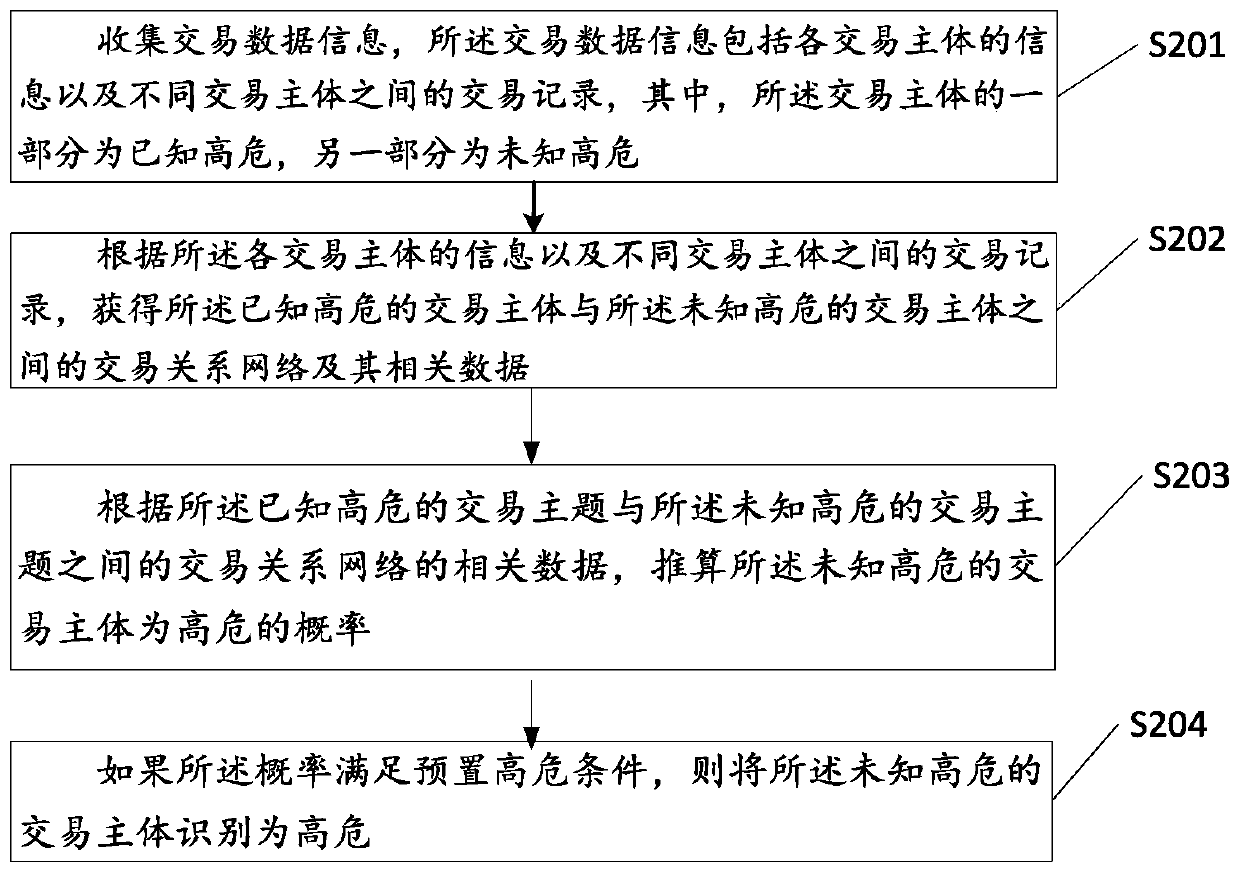
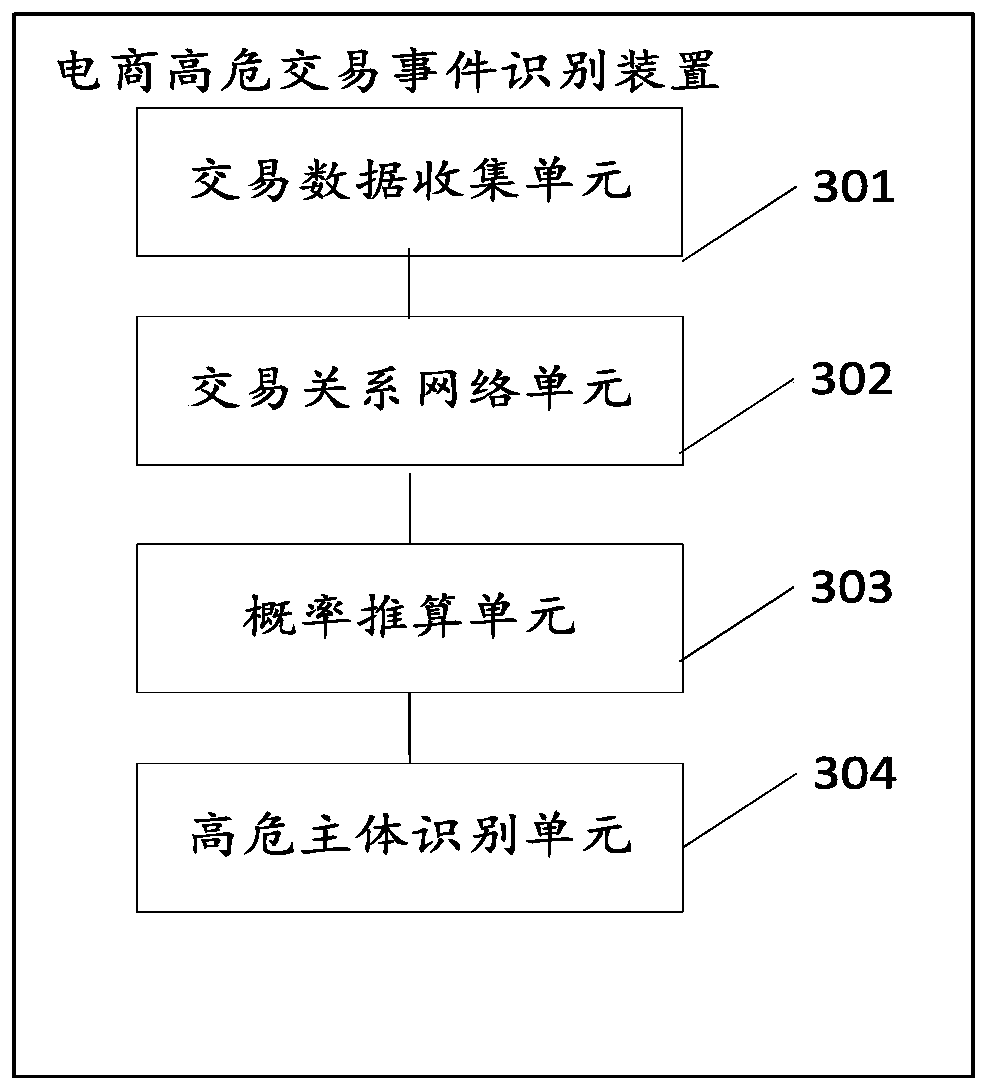
[0018] Please refer to figure 1 , a schematic diagram of an application scenario of an embodiment involved in the technical solution of this specification. The e-commerce trading platform is responsible for accessing buyers 1, 2...n, and sellers 1, 2...n, and facilitating transactions between buyers and sellers and the subsequent payment process on the platform. There is a transaction log in the platform, and its log has recorded data information related to each e-commerce transaction, such as buyer ID, seller ID, transaction type, transaction time, transaction amount, payment method (such as credit card, savings card, goods to payment, etc.), transaction times, total transaction amount and other field information. The platform sends each e-commerce transaction-related data information to the identification device of high-risk transaction subjects based on various strategies to identify high-risk new transaction subjects and related events, thereby identifying new high-risk b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com