Malicious code detection method and device
A malicious code detection and malicious code technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as malicious code cannot be protected, malicious code is not allowed to be executed, and detection methods cannot be detected, etc., and achieves the effect of fine-grained protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
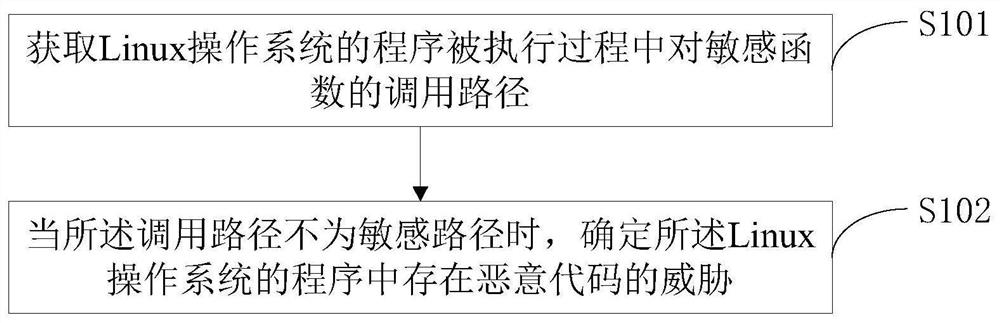
[0052] This embodiment 1 provides a malicious code detection method from the perspective of the security protection system of the Linux operating system host, specifically, see figure 1 , the method may specifically include:
[0053] S101: Obtain the calling path of the sensitive function during the execution of the program of the Linux operating system;
[0054] S102: When the calling path is not a sensitive path, determine that there is a threat of malicious code in the program of the Linux operating system.
[0055] It should be noted that the sensitive function is a function that can access the resources of the Linux operating system, and / or a function that can change the state of the Linux operating system, and the sensitive path is a function other than the sensitive function set by the Linux operating system A call path other than the normal call path for .
[0056] The malicious code detection method provided by this embodiment, by obtaining the calling path of the s...
Embodiment 2
[0058] The second embodiment is based on the first embodiment, and provides another malicious code detection method from the perspective of the security protection system of the Linux operating system host, specifically, see figure 2 , the method may specifically include:
[0059] S201: Determine the sensitive function and determine the sensitive path;
[0060] As a kind of implementable mode, the file operation function, creation process function, memory operation function, network access function and system-related functions in the program of determining Linux operating system are sensitive functions in this application:
[0061] Wherein, the file operation function includes any one or more of open function, openat function, openat64 function, read function, pread function, write function and writev function;
[0062] The creation process function includes any one or more of execve function, clone function and fexecve function;
[0063] The memory operation function inclu...
example 1
[0075] First, the dlsym function in the sensitive path after instrumentation will be monitored at the first time, and it is found that it further calls the syscall function, and the syscall function is also instrumented, and will continue to monitor, and it is further found that the openat64 in the sensitive function is called through the syscall function function, through the above tracking, it is determined that the calling path of the openat64 function in the sensitive function is "calling through the syscall function".
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com