Anti-attack method based on threat intelligence
An anti-attack and intelligence technology, applied in the field of anti-attack based on threat intelligence, can solve the problems of high hysteresis, low efficiency, false negatives, etc., and achieve the effect of low false positive rate, reduced server traffic, and low cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
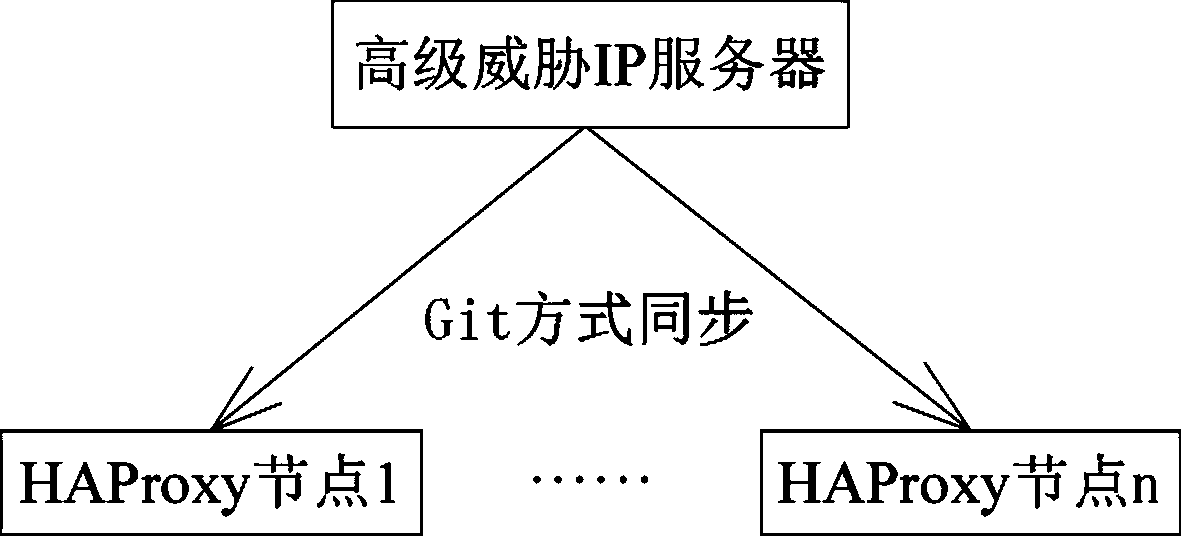
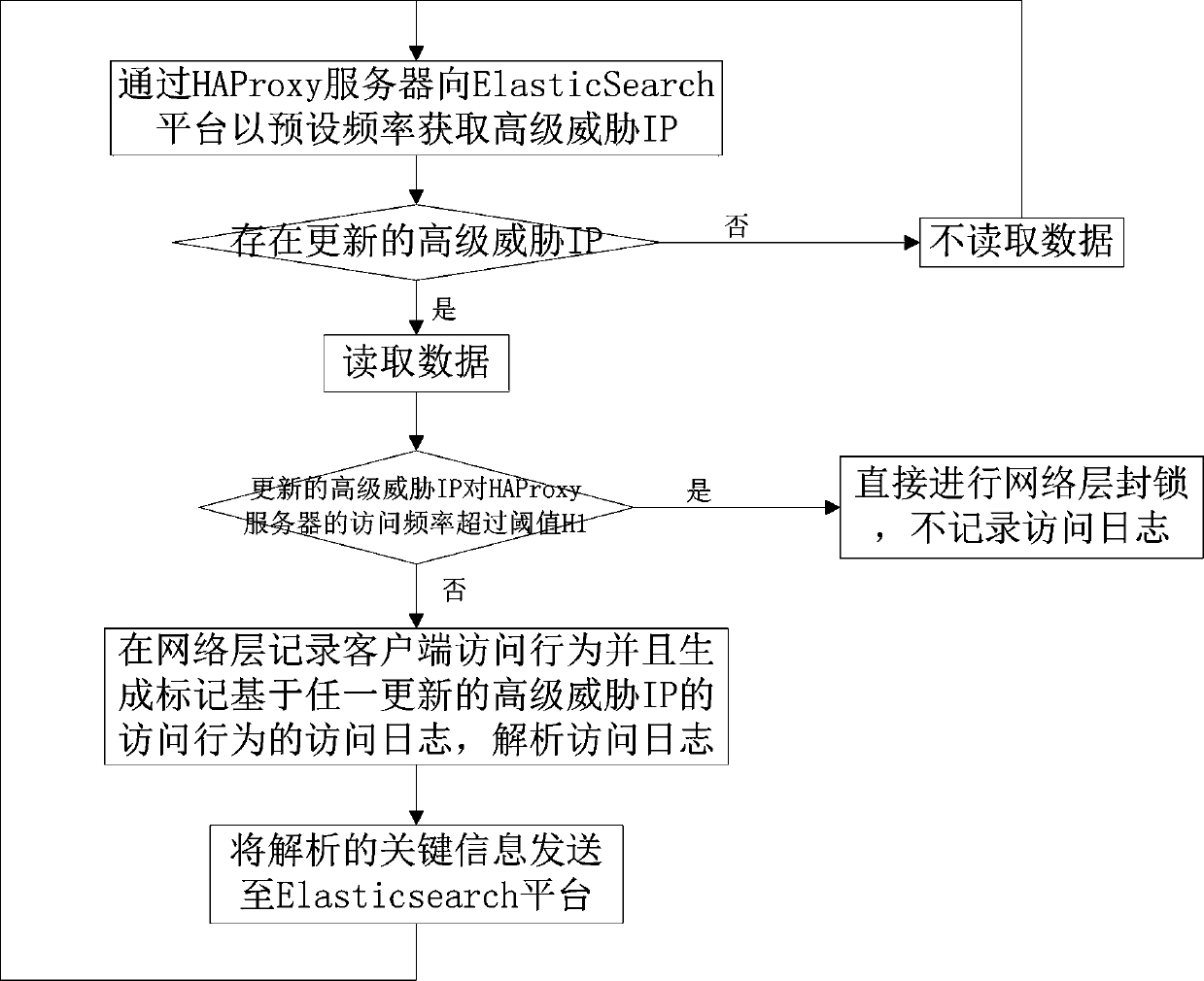
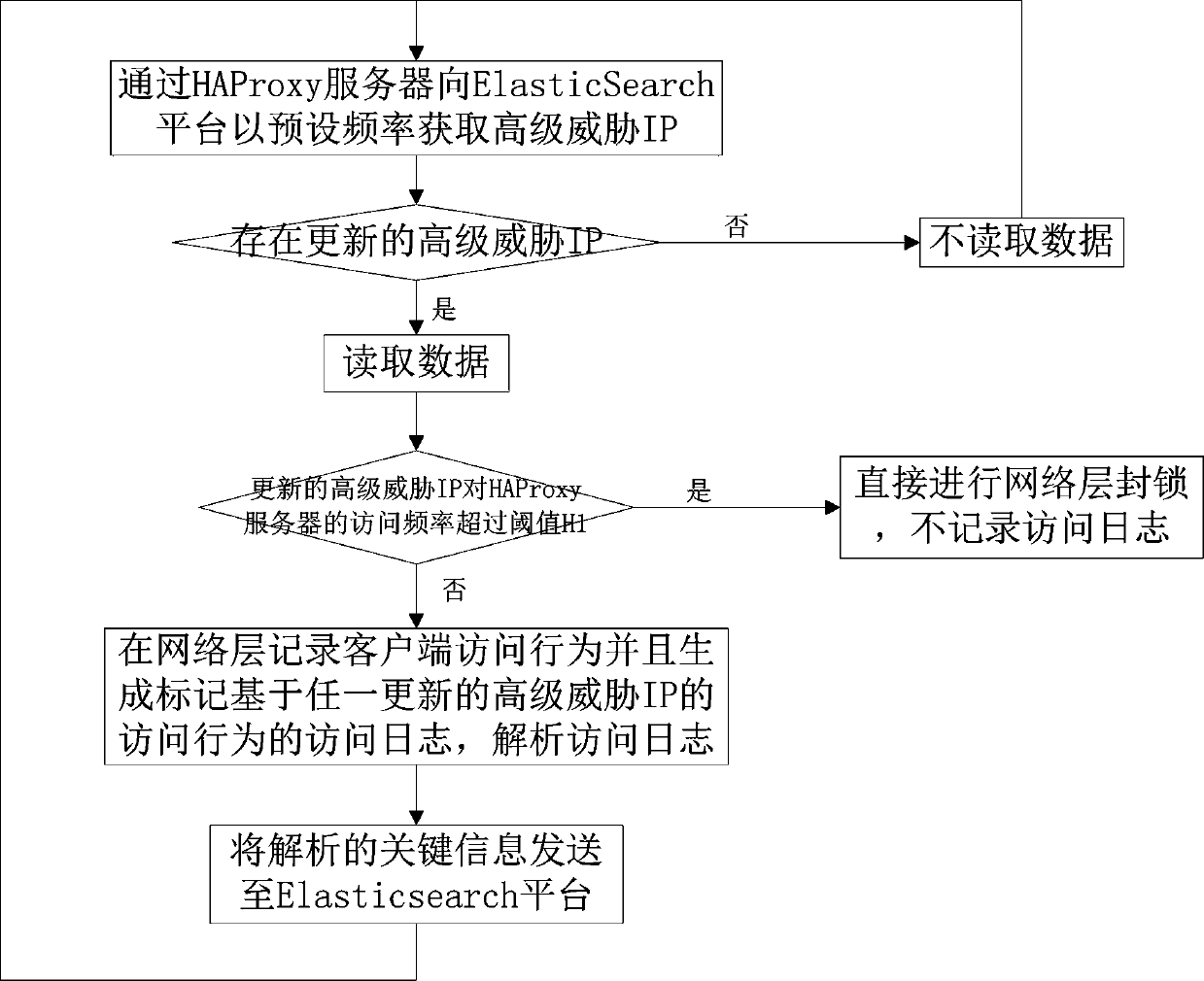
[0025] The present invention relates to an attack prevention method based on threat intelligence. The main principle is: regularly obtain high-level threat IPs, and distribute them to each HAProxy server node, establish high-level threat IP tables through ipset and iptables, and use iptables to detect high-level threat IPs in real time. IP access behavior is blocked, and the blocking log is sent to the ElasticSearch platform, so as to achieve the function of blocking IP at the source of the network layer; in simple terms, the methods include obtaining advanced threat IP, issuing advanced threat IP, updating and blocking IP, There are 5 parts: data return and blocking attack source.
[0026] The high-level threat IP refers to the IP that appears in the scanning IP database and attacking IP database f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com