Campus access control method and system based on internet
An access control and Internet technology, which is applied in the field of campus access control methods and systems, can solve the problems of correct registration information, difficult to track, and the difficulty of the school to count the historical records of visitors, so as to facilitate tracking and searching, and improve the cleanliness of personnel. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
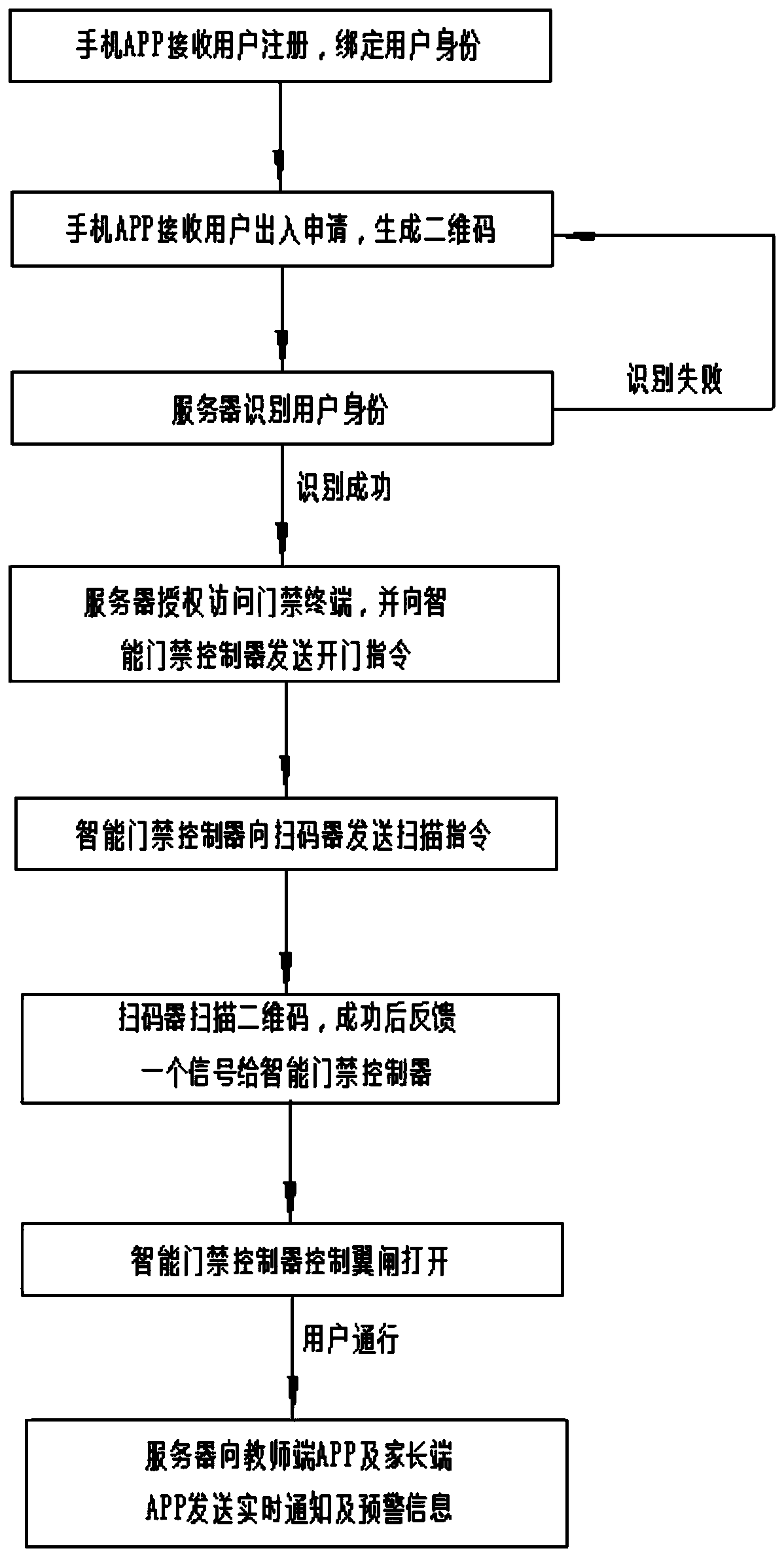
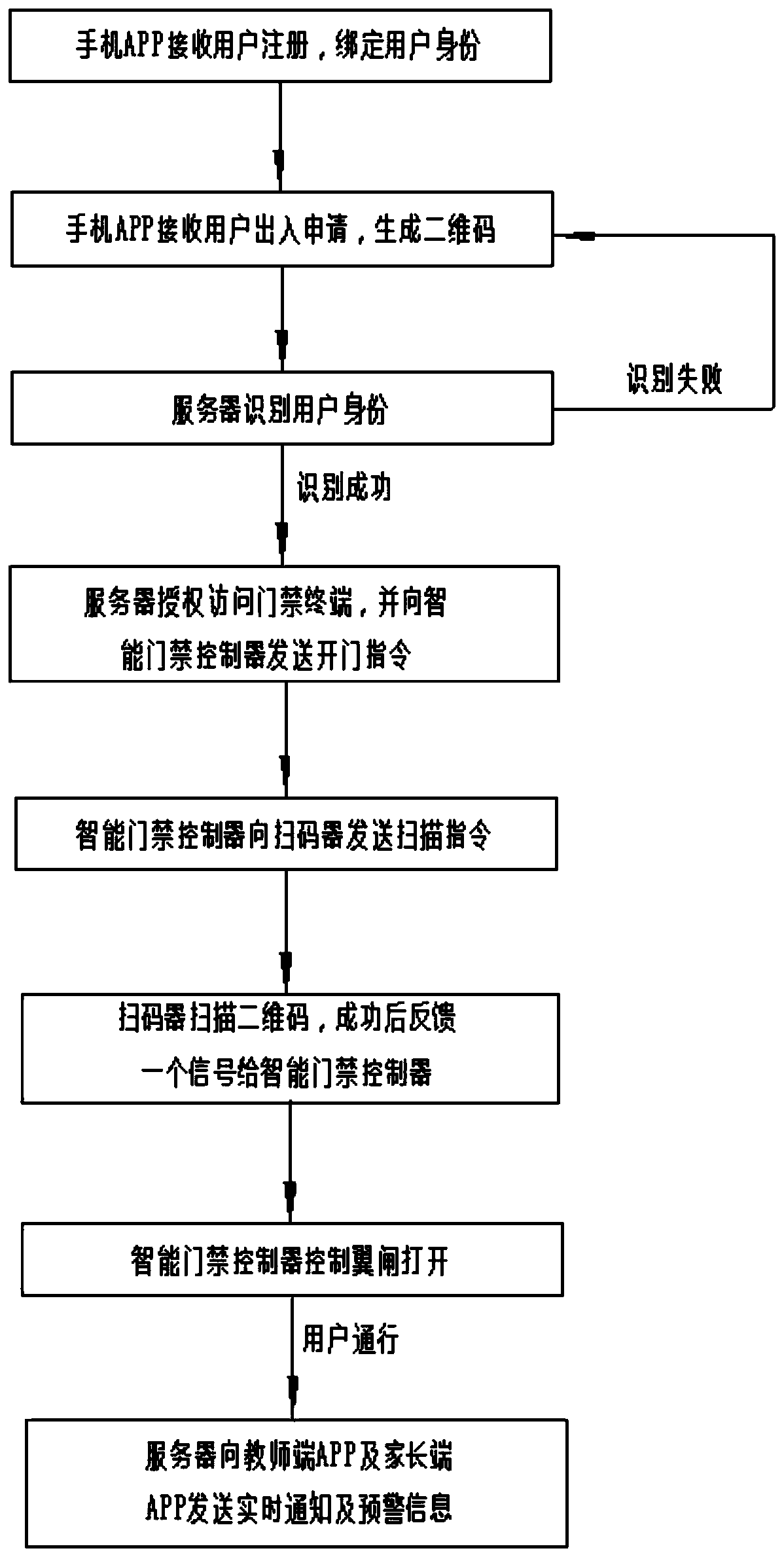
[0040] Such as figure 1 Shown, a kind of campus access control method based on Internet, comprises the steps:
[0041] S10: After receiving the registration request sent by the user, the mobile APP (Happy Parents APP) binds the user's identity according to the information provided by the user. If the binding is passed, it enters step S20; otherwise, it sends a notification of binding failure;
[0042] S20: If the mobile phone APP (Happy Parents APP) receives the user's access request, it generates a corresponding two-dimensional code and sends an access application to the server;
[0043] S30: After receiving the user's access application, the server identifies the user's identity by comparing the pre-stored student information;
[0044] S40: After the identification is successful, send an instruction to open the door to the access control terminal; and after scanning the QR code, open the wing gate, and if it detects that the user is passing, send a user passing signal to th...
Embodiment 2
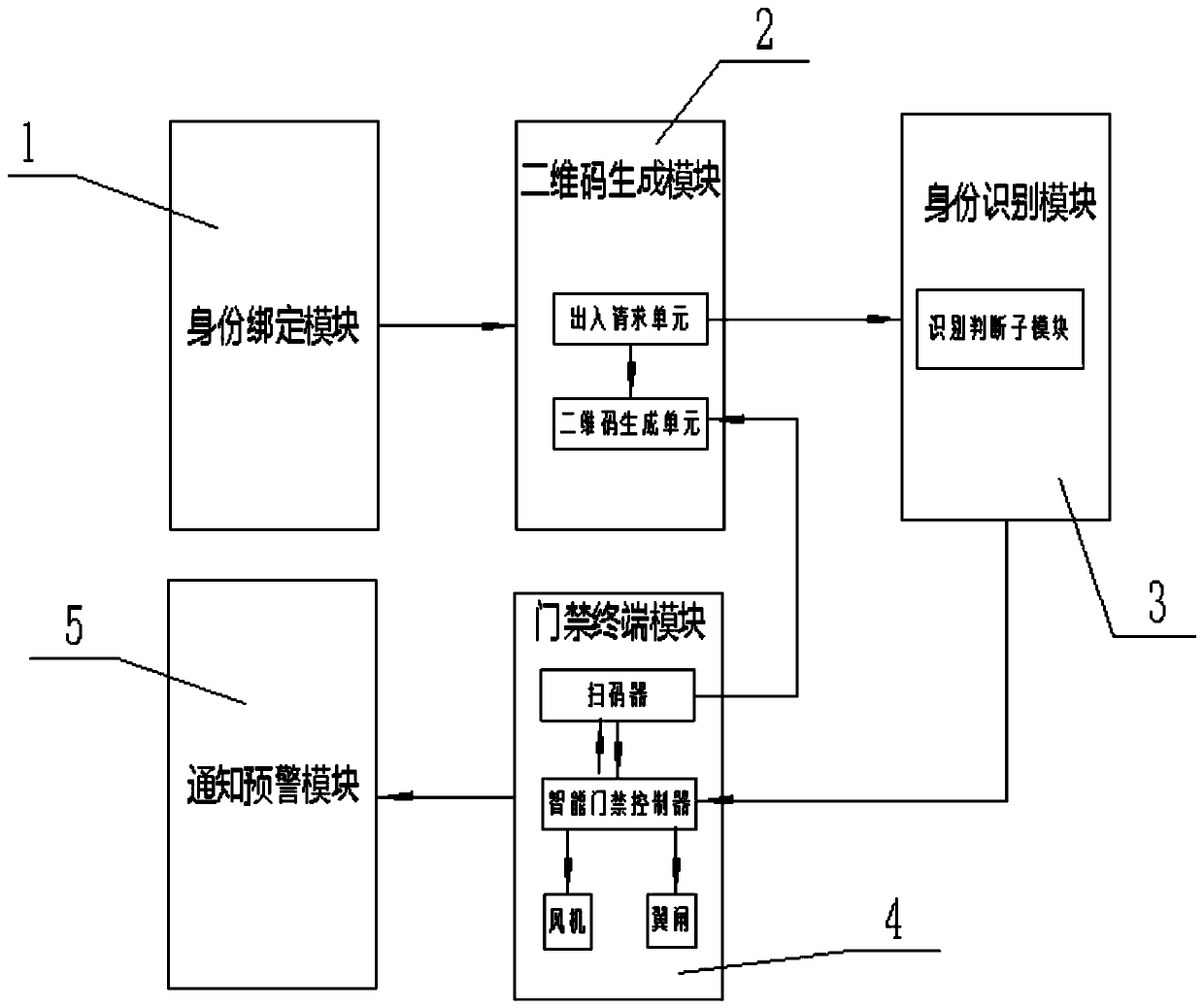
[0047] This embodiment is on the basis of embodiment 1, as figure 1 As shown, the step S30 specifically includes the following steps:
[0048] After receiving the access application, the server judges whether the student information provided by the user matches according to the pre-stored student information. If it matches, the identification is successful, and the server authorizes access to the access control terminal, and proceeds to step S40; .
Embodiment 3
[0050] This embodiment is on the basis of embodiment 1, as figure 1 As shown, the step S40 specifically includes the following steps:
[0051] After the identification is successful, the server sends an instruction to open the door to the intelligent access controller of the access control terminal;
[0052] After receiving the door opening instruction, the intelligent access controller of the access control terminal sends a scanning instruction to the code scanner of the access control terminal;
[0053] If the code scanner successfully scans the QR code, it will feed back a signal to the intelligent access control controller, and the intelligent access control controller will control the wing gate to open after receiving the feedback signal.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com