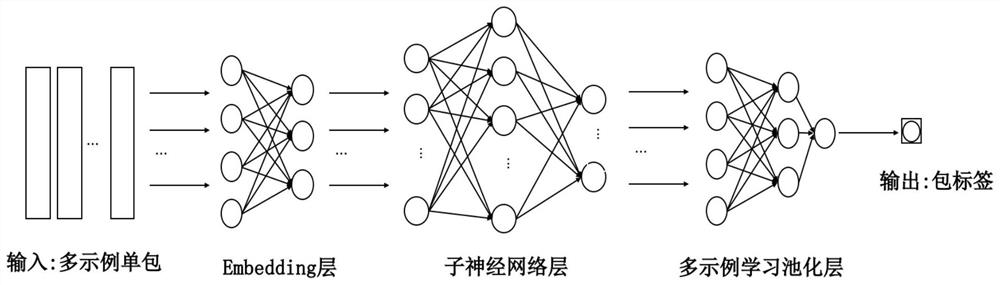
A method and system for verifying suspicious threat indicators based on multi-instance learning
A multi-example learning and indicator verification technology, applied in the field of suspicious threat indicator verification method and system, can solve the problems of ignoring the semantic information of intelligence information, no way to guarantee the accuracy rate, and high false positive rate of verification, so as to reduce manual investment and error interference , improve accuracy, and strengthen the effect of active analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0045] Example 1 A Suspicious Threat Indicator Verification Method Based on Multi-instance Learning
[0046] The present invention is applicable to automatic verification of various types of suspicious threat indicators. Example Take the suspicious APT domain name as an example to illustrate the specific application of the present invention.
[0047] For some suspicious APT domain names and multiple pieces of threat intelligence information related to them, this method can be used to automatically verify whether they are malicious domain names in APT attacks. Here are the specific steps:
[0048] 1) Preprocessing of relevant intelligence information
[0049] Take a suspicious APT domain name "jerrycoper.org" as an example to illustrate the preprocessing steps. There are currently 3 threat information reports related to it. First, match the suspicious APT domain name in each report and replace it with the specific phrase "IS_APT_DOMAIN" , to avoid the impact of different sus...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com