Composite high-security IP secure communication method with true random change key
A secure communication and true random technology, applied in key distribution, can solve the problems of implanting listening Trojan horses, network equipment security holes, easy access to IP subnets, etc., and achieve the effect of resisting attack threats and effectively deciphering and analyzing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
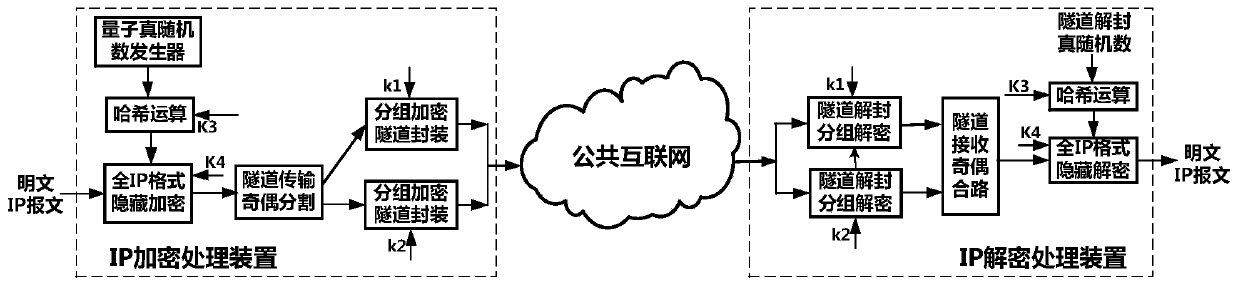
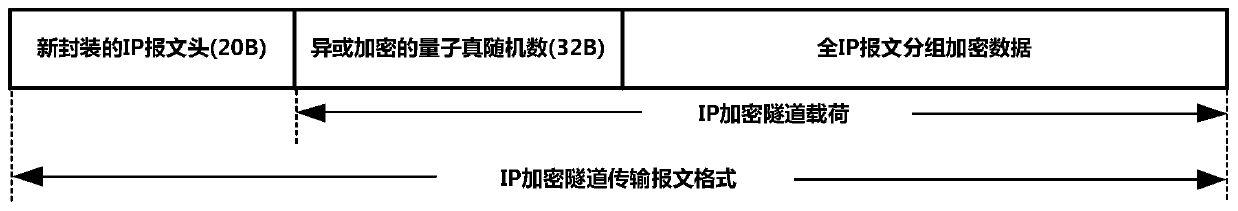
[0014] In the composite high-security IP confidential communication method with truly random key changes proposed by the present invention, the IP encryption machine first uses the quantum true random data generated in real time and the key distribution protocol dynamically for each plaintext IP packet to be transmitted. The distributed keys are concatenated and hashed to form a format-hidden encryption key, and the entire message including the IP header is encrypted in full IP format to form a format-hidden data block; then the format-hidden data block is combined with the Quantum True random data is concatenated together to form an IP encrypted tunnel load data block, and then two randomized data blocks are formed by byte parity segmentation; finally, these two randomized data blocks are encrypted by the link transmission packet encryption algorithm Finally, the two block encrypted data blocks are repackaged into standard IPSec messages (that is, IP encrypted messages) respec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com