Security risk assessment method and device for information system and apparatus
A security risk and information system technology, which is applied in the field of computer-readable storage media and information system security risk assessment, can solve the problem of low assessment speed, achieve the effect of increasing the speed and avoiding the calculation process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
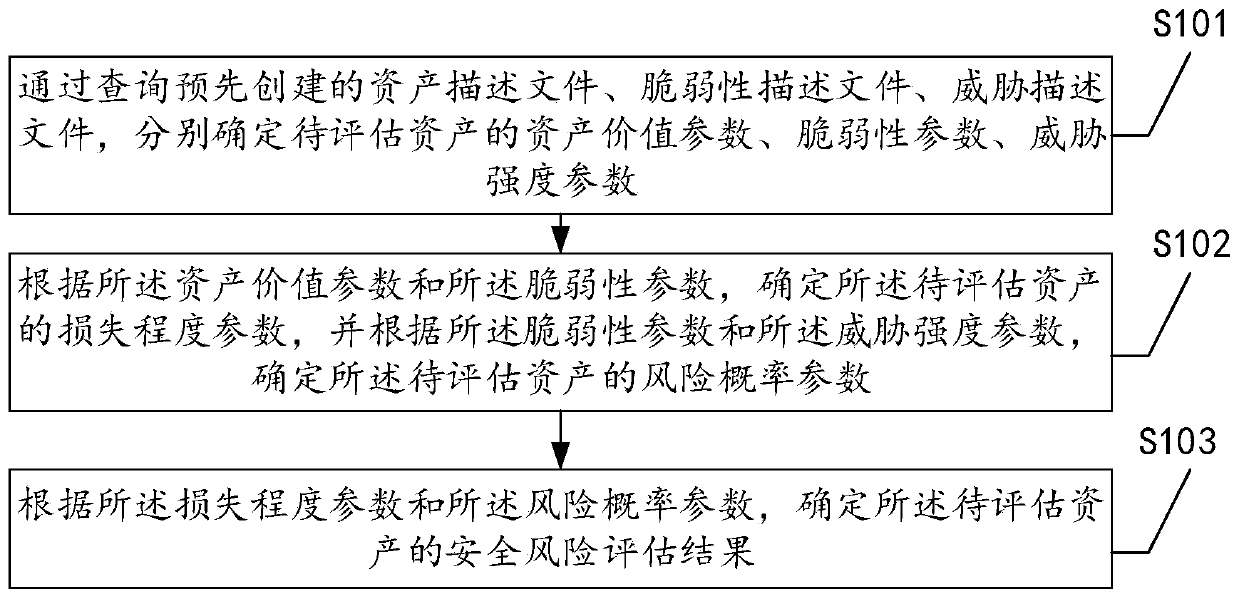
[0041] The following describes the first embodiment of a security risk assessment method for an information system provided by this application, see figure 1 , The first embodiment includes:
[0042] Step S101: by querying the pre-created asset description file, vulnerability description file, and threat description file, the asset value parameters, vulnerability parameters, and threat intensity parameters of the assets to be assessed are determined respectively;
[0043] Information system (Information system) is a human-machine integrated system composed of computer hardware, network and communication equipment, computer software, information resources, information users and rules and regulations for the purpose of processing information flow. The software and hardware in the information system can be called information assets. Security risks are potential and unoccurring dangers of information assets. Due to the existence of security risks, information assets may be dangerous und...
Embodiment 2
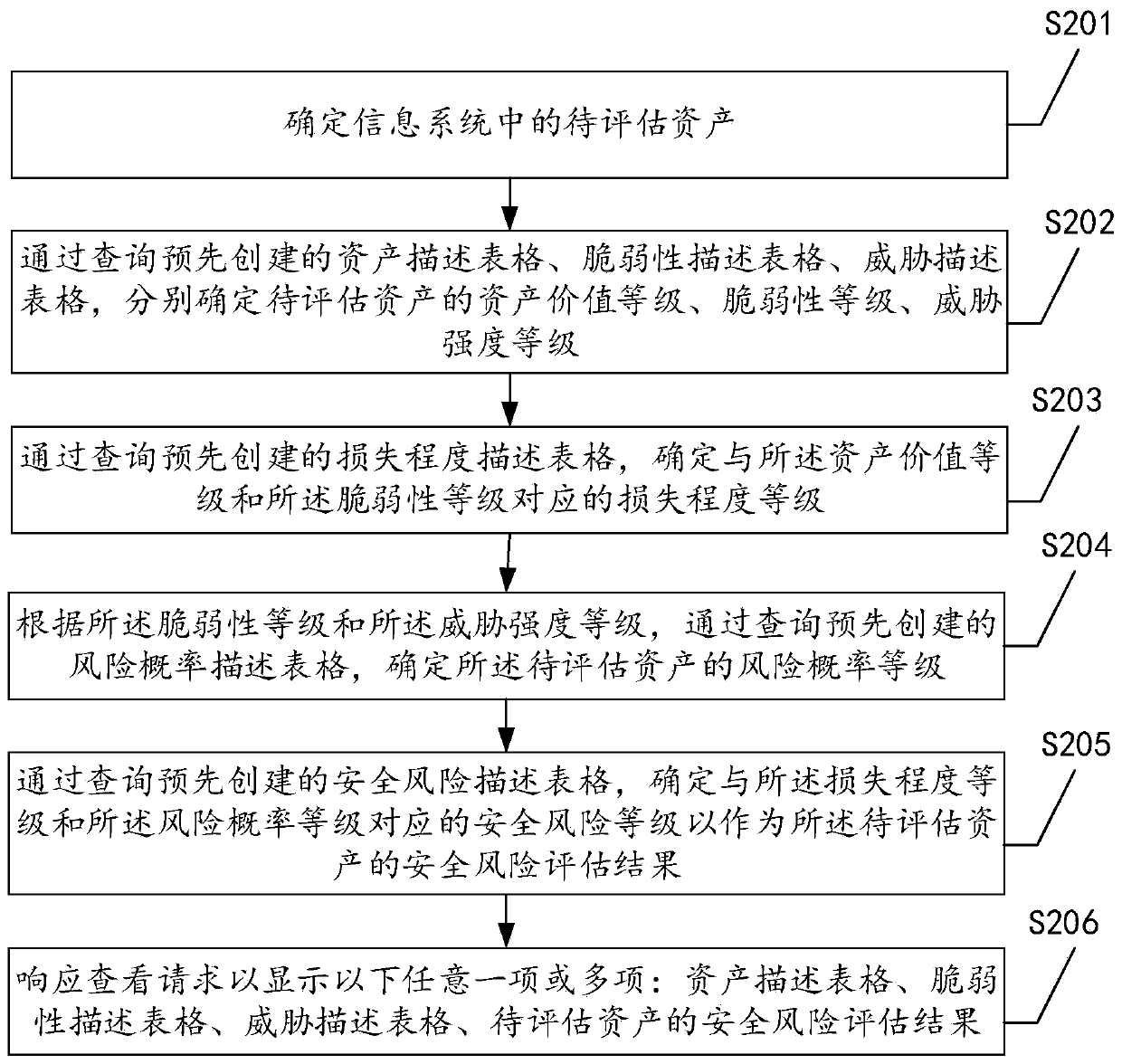
[0051] See figure 2 , The second embodiment specifically includes:
[0052] Step S201: Determine the assets to be evaluated in the information system;
[0053] The specific determination method may be determined according to user requests, or the assets to be assessed may be filtered out from the information system according to preset rules. This embodiment does not limit the number of assets to be assessed.
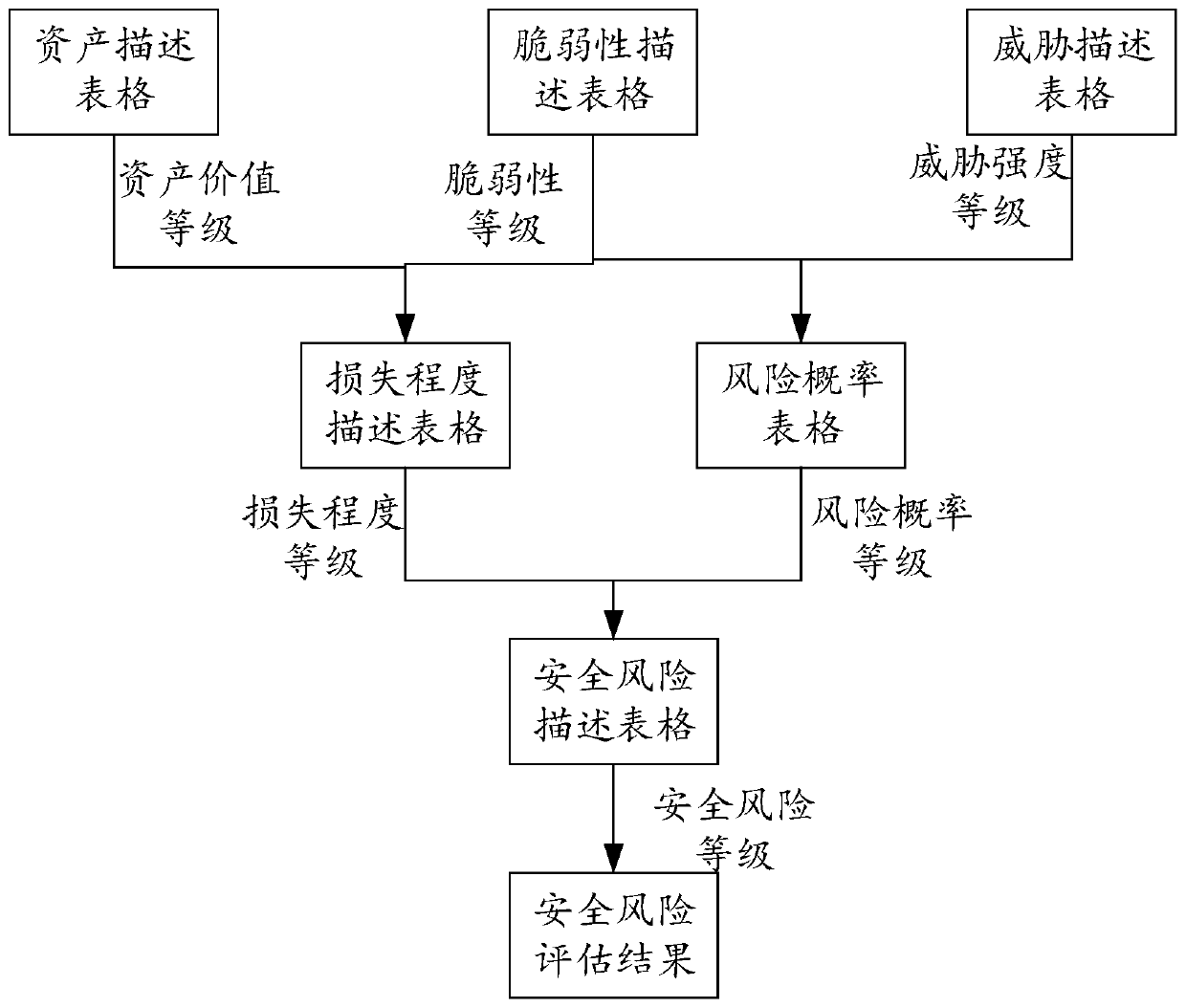
[0054] Step S202: Determine the asset value level, vulnerability level, and threat intensity level of the asset to be assessed by querying the pre-created asset description table, vulnerability description table, and threat description table;
[0055] For the asset description table, the creation process is as follows: create an asset description table, divide different categories and sub-categories of assets in the table, and identify the asset value of different categories. Specifically, the identification level can be divided into "very low" and "low" , "Medium", "High", "Hi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com