Control method of shared charger
A control method and charger technology, applied to instruments, time registers, coinless or similar appliances, etc., can solve the problems of high production cost and high power consumption of chargers, achieve simple circuit structure, and save charger costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
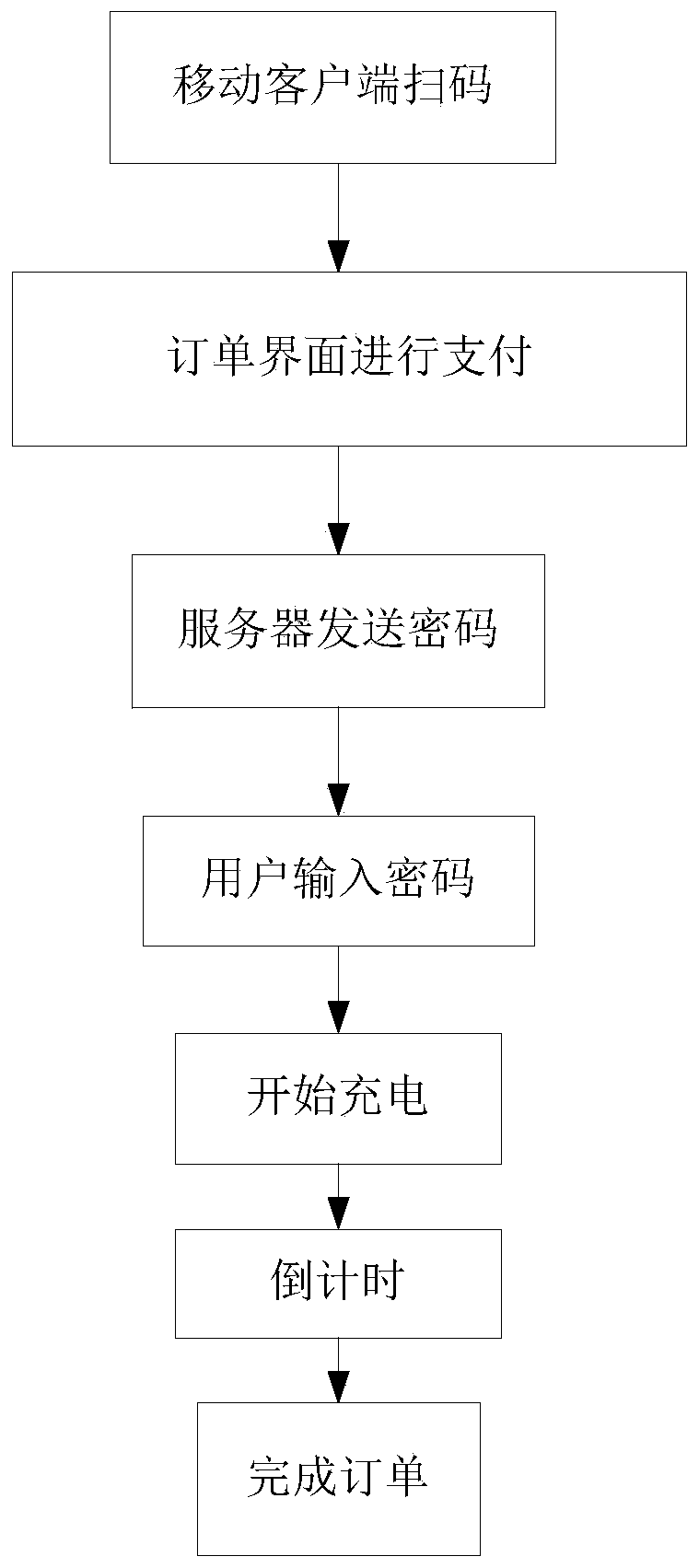
[0029] like figure 1 As shown, this embodiment provides a method for controlling a shared charger, including the following steps:
[0030] S1. Uniquely number the shared charger, and mark the QR code with the unique number and the URL information of the server on the charger;
[0031] S2. Scan the two-dimensional code described in step S1 through the mobile client to connect to the server, and transmit the identified coded information to the server, and at the same time, the mobile client obtains the order interface, and pays for each order through the order interface;
[0032] S3. After the server receives the encoded information from the mobile client and the fee payment completion information, it uses the encoded information as the password seed, generates multiple sets of passwords through the preset password generation rules, and sorts the passwords according to the preset rules; the server Send the corresponding sorted passwords to the mobile client according to the num...
Embodiment 2
[0040] This embodiment is based on Embodiment 1, and is implemented when there are 21 cipher groups.
[0041] When implementing, the single-chip microcomputer is in big-endian mode, and a password is generated using a custom function. Take the last 7 digits of the power bank ID number as the seed, and use the function TwoRandGet(tmpRandData)
[0042] 'addition
[0043] tmpRandData = CLng(tmpRandData) + 416701972
[0044] ' Find the remainder
[0045] TwoRandGet=ThreeMyMod(tmpRandData,125243)
[0046] end function
[0047] Calculate 21 groups of passwords, the 21st group in the password is the reset code, the 1st to 20th groups are the use passwords, the reset code password can be input at any time, the password jumps to the start password group 1, and the 1st to 20th groups are 20 groups of passwords are used in a clockwise cycle, starting from group 1; when the password is used to use the 7th group of passwords, then the previous 5th and 6th group of passwords are not av...
Embodiment 3
[0051] On the basis of implementation 1, the password adopts the password in the form of characters, and a password group is formed by arranging and combining multiple different characters.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com