Intelligent operation method and device of server, intelligent server and storage medium
A technology of intelligent operation and server, which is applied in the field of server intelligent operation method, intelligent server, readable storage medium, and device, and can solve problems such as tediousness, poor user experience, and misoperation, so as to improve service quality, accurately identify, and avoid security Threat effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
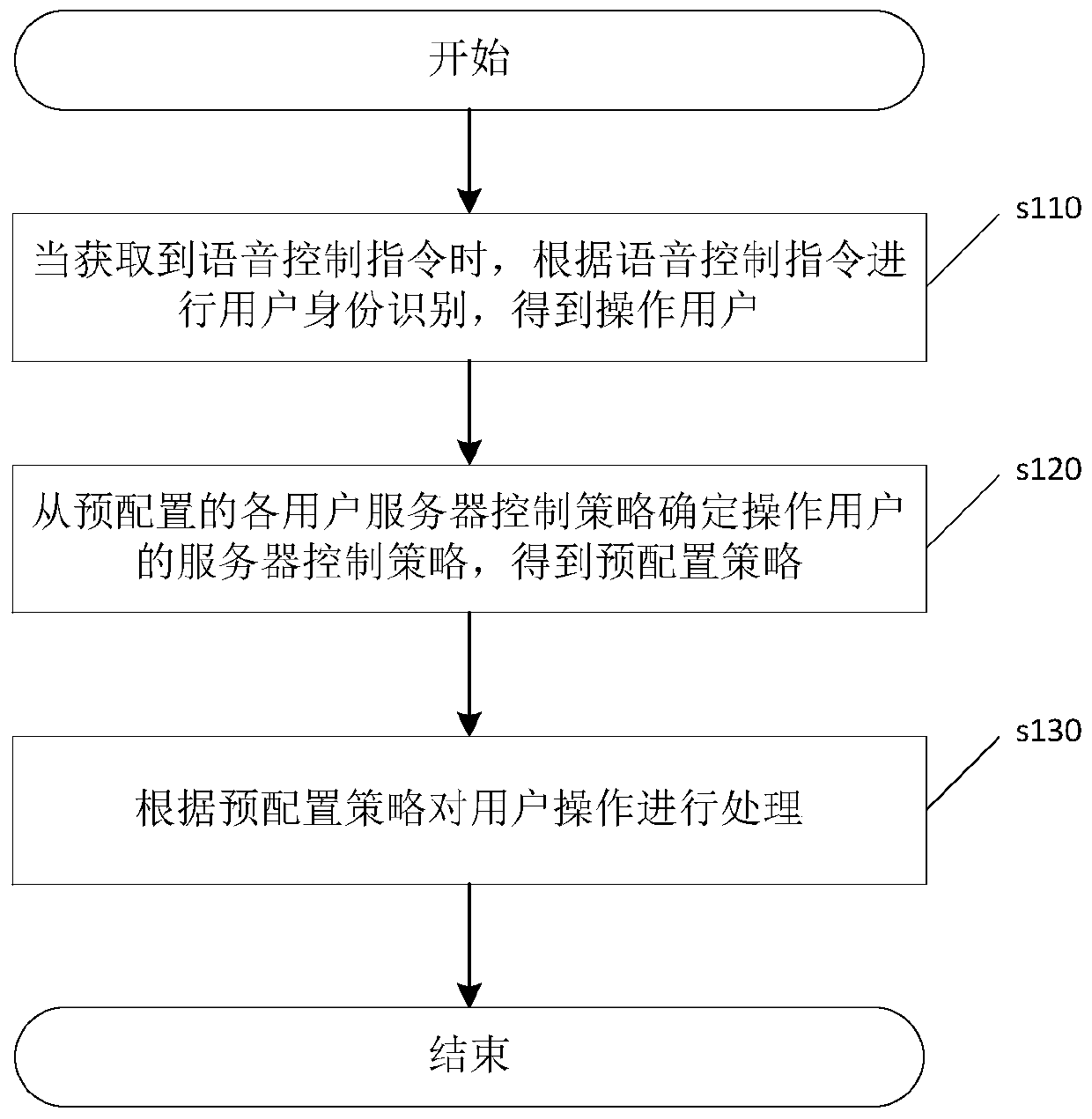
[0048] This embodiment proposes a server intelligent operation method, please refer to figure 1 , figure 1 A flow chart of the server intelligent operation method provided in this embodiment; the method mainly includes:
[0049] Step s110 , when the voice control command is acquired, perform user identification according to the voice control command to obtain the operating user.
[0050] The specific way of user identity recognition based on voice can refer to related technologies, such as voiceprint recognition, etc., or directly call the product with voice recognition function embedded in the server to perform user identity recognition, etc. In this embodiment, the control operation based on voice There is no limit to the way the command performs user identity identification, and corresponding settings can be made as required.
[0051] Step s120, determining the server control policy of the operating user from the pre-configured server control policies of each user to obta...
Embodiment 2
[0059] In the foregoing embodiment, the type of the server control policy is not limited, and this embodiment takes the policy as an operation authority control policy as an example for introduction. Different users have different operating permissions. Identifying the user identity and corresponding permissions for each control command to the server can effectively guarantee the security of the server system and prevent illegal personnel from tampering with the server.
[0060] After determining the identity of the current operating user and before processing the user operation according to the pre-configured policy, the user operation request can be further obtained; then the user operation is processed according to the pre-configured policy as follows: according to the operating user's operation authority control policy Verify the operation authority of the user operation request, and generate the authority verification result; if the authority verification result shows that...
Embodiment 3
[0069] In the above embodiments, the operation authority control strategy is taken as an example to introduce the server intelligent operation method. In order to meet the personalized server setting requirements of different users, in this embodiment, the server control strategy is used as the server interface configuration strategy and the server information interaction strategy as an example. For the introduction, the intelligent operation process of the server under other types of server control policies can refer to the introduction of this embodiment.
[0070] Different users may have different requirements for server interface settings. In order to meet the needs of different users for server interface settings and realize flexible switching of intelligent interface modes, preferably, the server control strategy may specifically include: server interface configuration strategy; Processing user operations includes: judging whether the interface configuration policy enable...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com