Web vulnerability detection method and device
A vulnerability detection and vulnerability technology, applied in the field of web vulnerability detection, can solve problems such as low efficiency of web vulnerability detection, and achieve the effect of avoiding low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
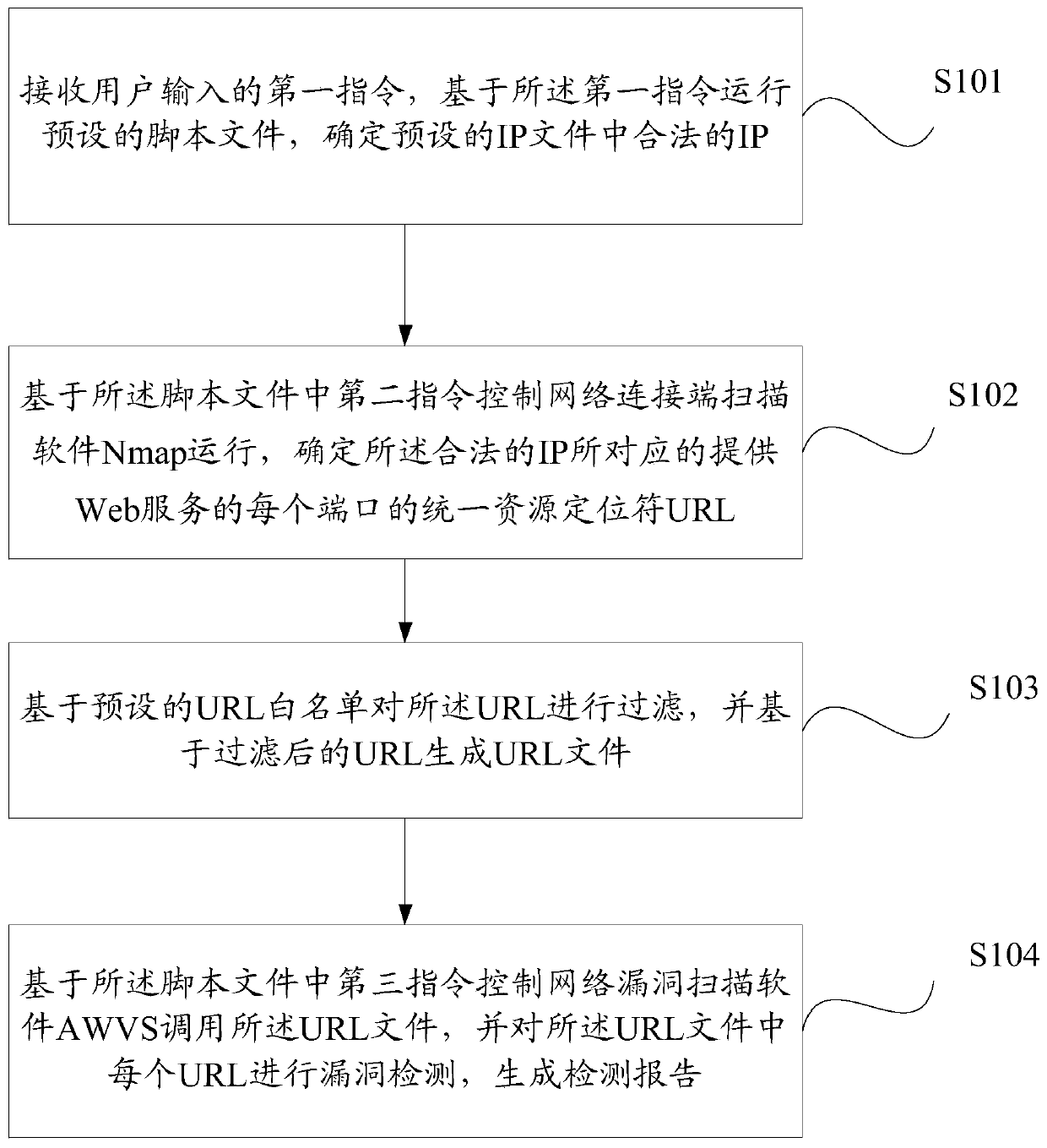
[0065] Step 101, receiving a first instruction input by a user, running a preset script file based on the first instruction, and determining a legal IP in the preset IP file.
[0066] Specifically, the IP file is pre-saved in the database of the computer device, wherein the IP file includes the IP of at least one host to be detected, and the IP file may be in the form of an IP list or in other forms. The computer device receives a first instruction input by a user. The computer device opens and executes the instructions in the preset script file based on the first instruction, wherein the script file can be an object-oriented, literal translation computer programming language python, a literal translation script file language JavaScript or C++ language, etc., in This is not a limitation. It should be understood that the computer device may be a server or a computer, and the computing device may be applied in technical fields such as finance, e-commerce, aerospace or biotechno...
Embodiment 2
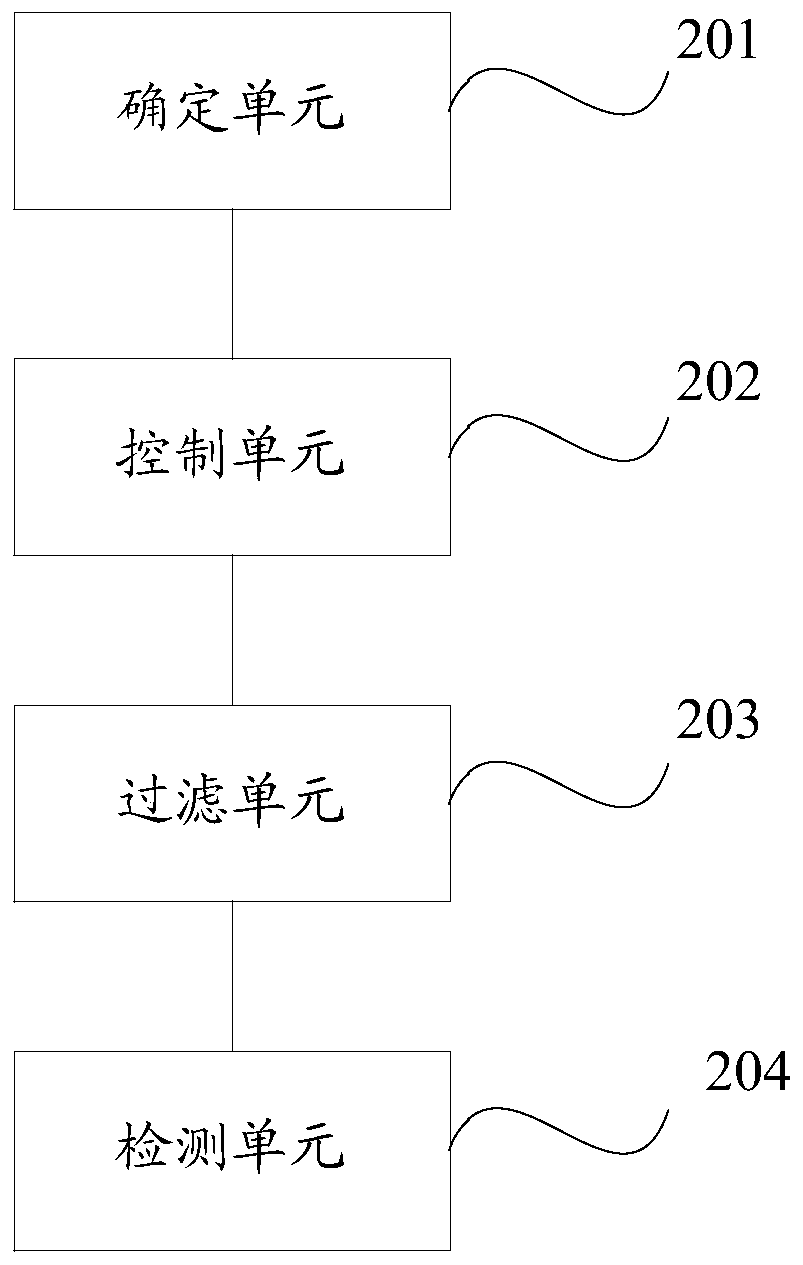
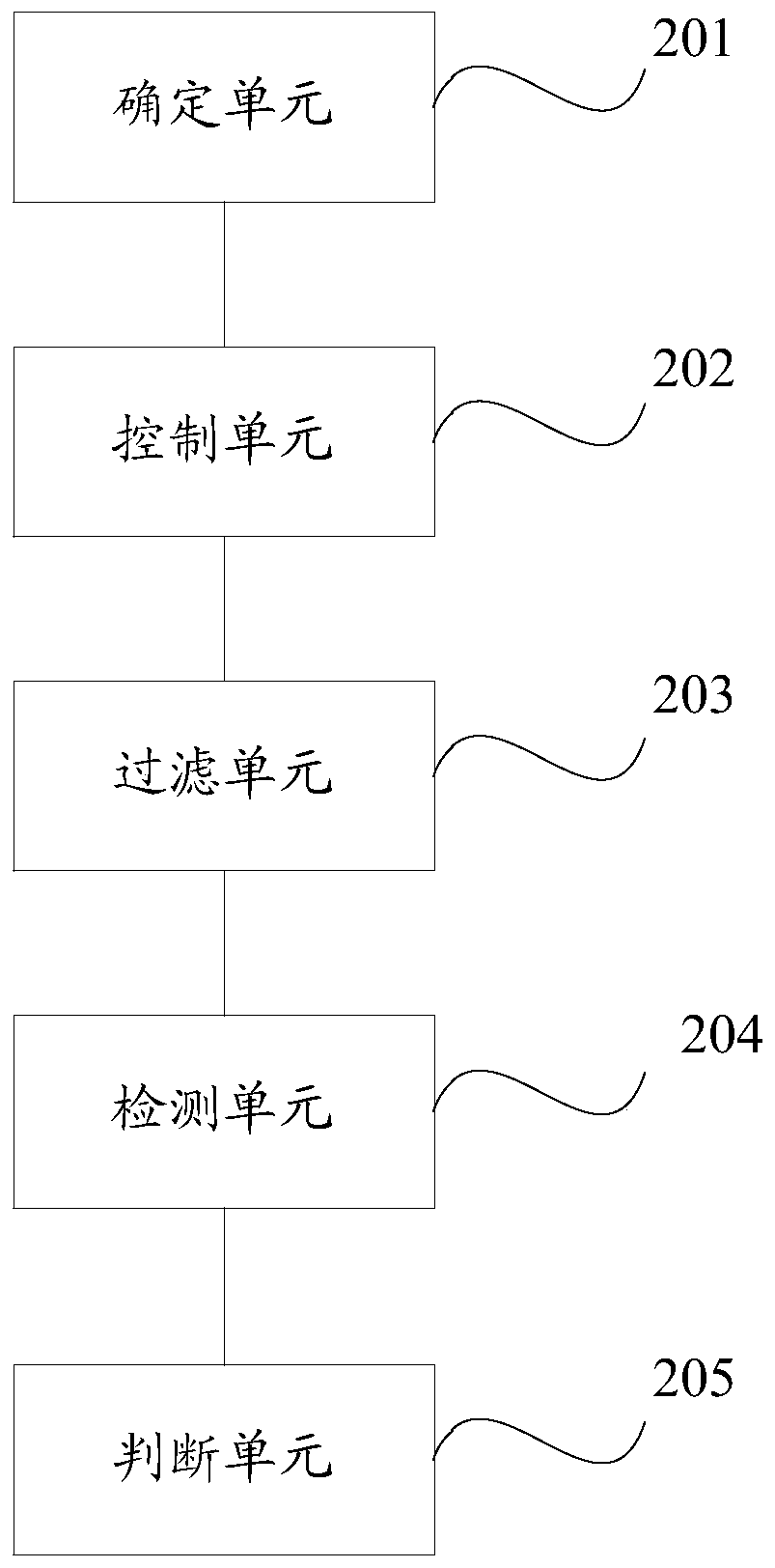
[0106] The embodiment of the present application provides a device for detecting web vulnerabilities, see figure 2 , the device consists of:
[0107] The determining unit 201 is configured to receive a first instruction input by a user, run a preset script file based on the first instruction, and determine a legal IP in the preset IP file;
[0108] The control unit 202 is used to control the operation of the network connection terminal scanning software Nmap based on the second instruction in the script file, and determine the uniform resource locator URL of each port that provides Web services corresponding to the legal IP;
[0109] A filtering unit 203, configured to filter the URL based on a preset URL whitelist, and generate a URL file based on the filtered URL;
[0110] The detection unit 204 is configured to control the network vulnerability scanning software AWVS to call the URL file based on the third instruction in the script file, and perform vulnerability detectio...
Embodiment 3
[0127] An embodiment of the present application provides a computer device, see Figure 5 , the device comprising:
[0128] Memory 501, configured to store instructions executed by at least one processor;
[0129] The processor 502 is configured to execute instructions stored in the memory to execute the method described in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com