Tooth shape code identification method and device and terminal equipment
An identification method and code name technology, applied in the field of numerical control, can solve the problems of high labor cost, consumption, and low key duplication efficiency, and achieve the effect of reducing labor cost and improving duplication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
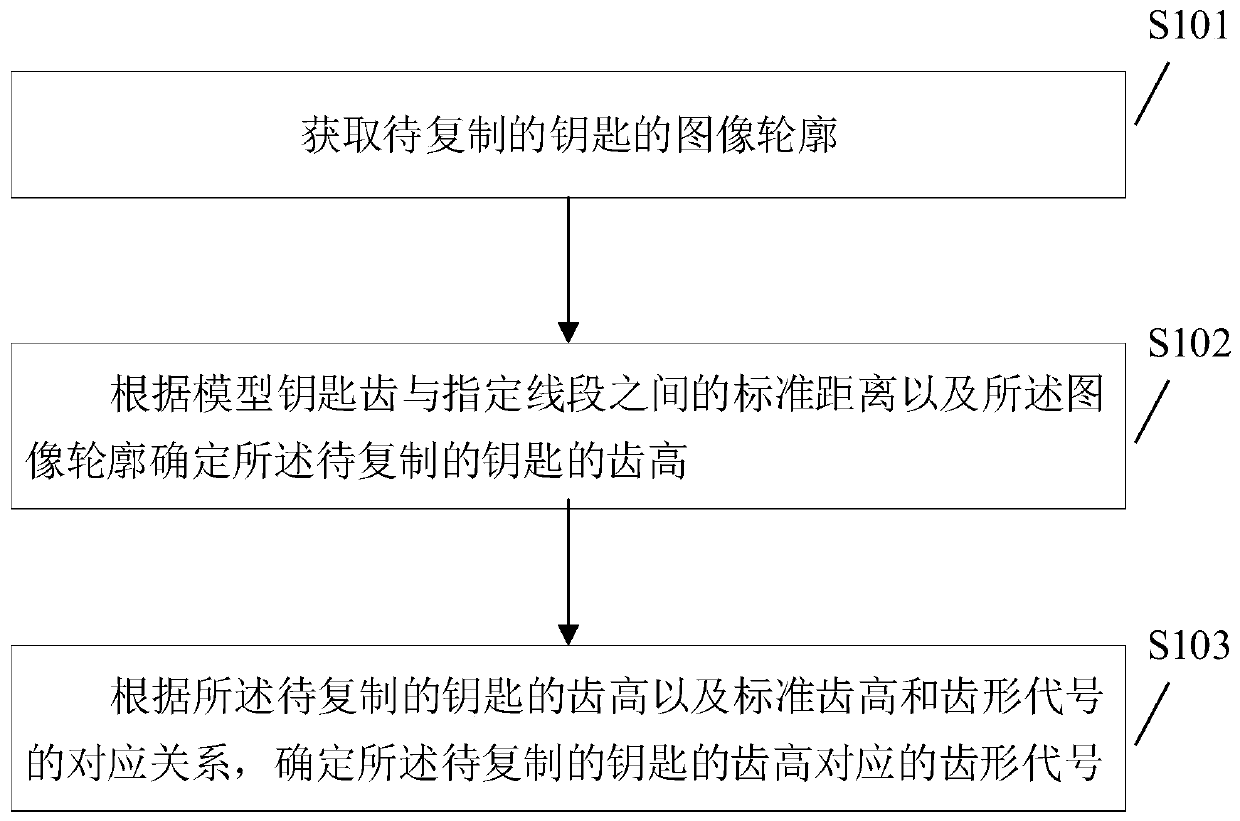
[0037] figure 1 It shows a schematic flow chart of the first tooth shape code identification method provided by the embodiment of the present application, and is described in detail as follows:
[0038] Step S101, acquiring the image profile of the key to be copied.
[0039] Specifically, the step S101 includes: performing a binarization operation on the image of the key to be copied, and the binarization operation includes: setting the gray value of the pixel point of the image of the key to be copied to 0 or 255, using the preset Let the contour detection function obtain the image contour of the key to be copied after the binarization operation.
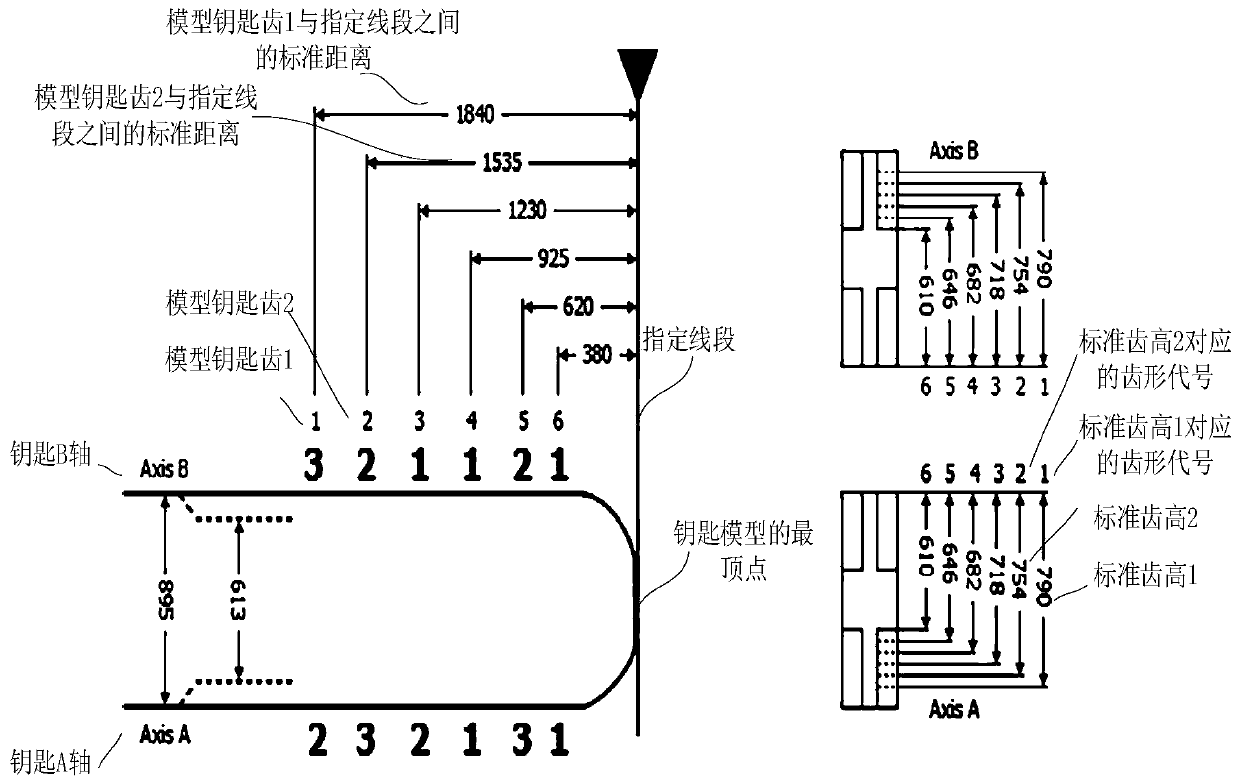
[0040] Step S102, determine the tooth height of the key to be copied according to the standard distance between the model key tooth and the specified line segment, which is perpendicular to the center line of the key model and passes through the vertex of the key model, and the image outline The line segment, the key model includ...
Embodiment 2
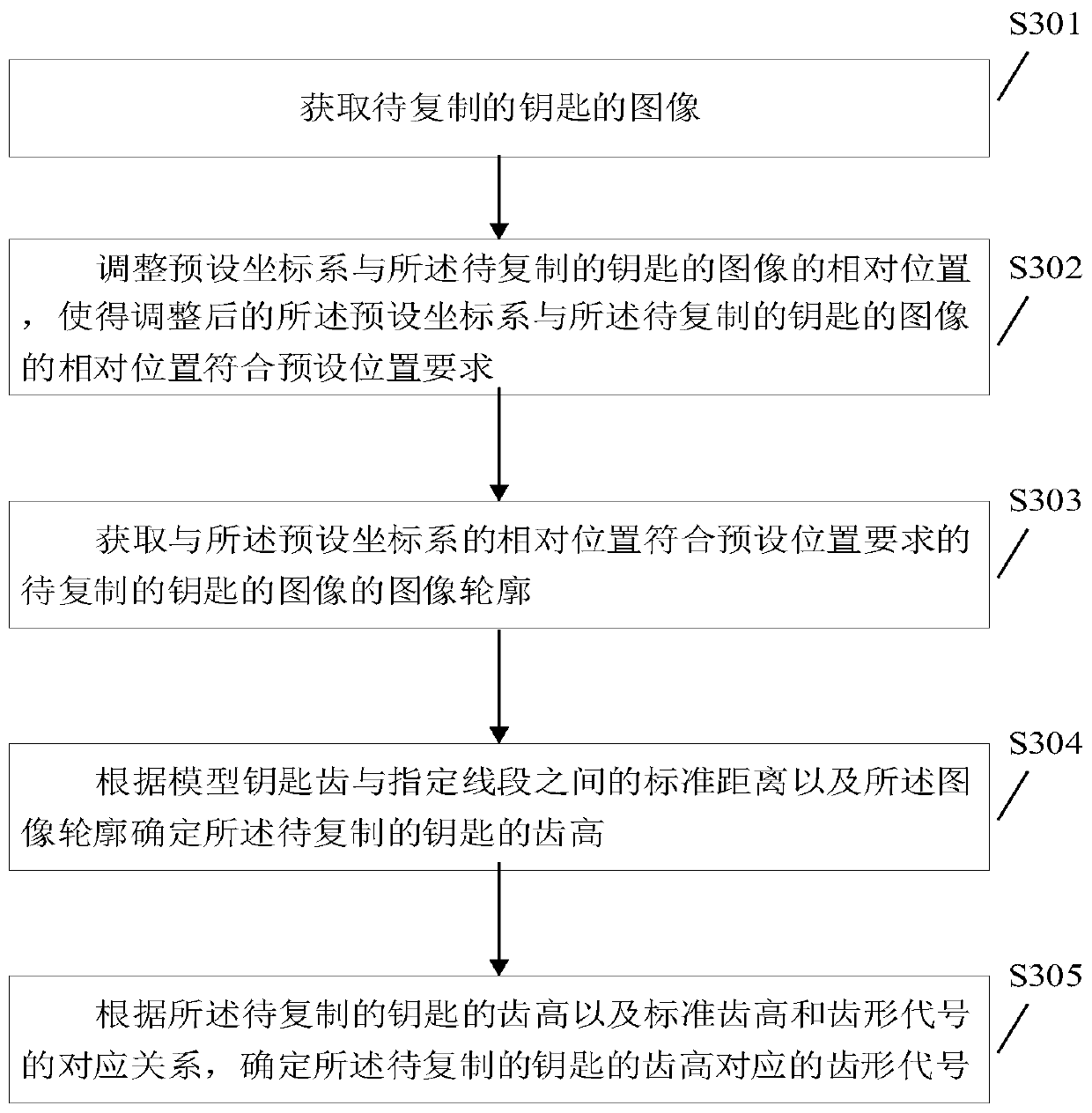
[0054] image 3 It shows a schematic flow chart of the second tooth shape code identification method provided by the embodiment of the present application. Step S303 of this embodiment is the same as step S103 of Embodiment 1, and will not be repeated here:
[0055] Step S301, acquiring the image of the key to be copied.
[0056] Specifically, the data collected by the image collection sensor is obtained, and the image of the key to be copied is obtained according to the data collected by the image collection sensor.
[0057] Step S302, adjusting the relative position between the preset coordinate system and the image of the key to be copied, so that the adjusted relative position between the preset coordinate system and the image of the key to be copied meets the preset position requirements.
[0058] Specifically, adjust the position of the preset coordinate system or / and the position of the image of the key to be copied, so that the adjusted relative position of the preset...
Embodiment 3
[0097] Corresponding to Embodiment 1 and Embodiment 2 above, Figure 9 It shows a schematic structural diagram of a tooth shape code recognition device provided by the embodiment of the present application. For the convenience of description, only the parts related to the embodiment of the present application are shown.
[0098] The tooth shape code identification device includes: a contour acquisition unit 901 , a tooth height determination unit 902 and a tooth shape code determination unit 903 .
[0099] The outline acquisition unit 901 is configured to acquire the image outline of the key to be copied.
[0100] The outline acquisition unit 901 is specifically configured to: perform a binarization operation on the image of the key to be copied, the binarization operation includes: setting the gray value of the pixel point of the image of the key to be copied to 0 or 255, using The preset contour detection function obtains the image contour of the key to be copied after the ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap