Php-based independent sql injection defense analysis alarm method and system thereof
An alarm system, an independent technology, applied in the transmission system, electrical components, etc., can solve the problem that it is difficult to establish normal SQL statements and SQL injection attacks, cannot provide very effective protection, high false alarm rate and false negative rate, etc. problem, to achieve the effect of increasing cost, good scalability, and data protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
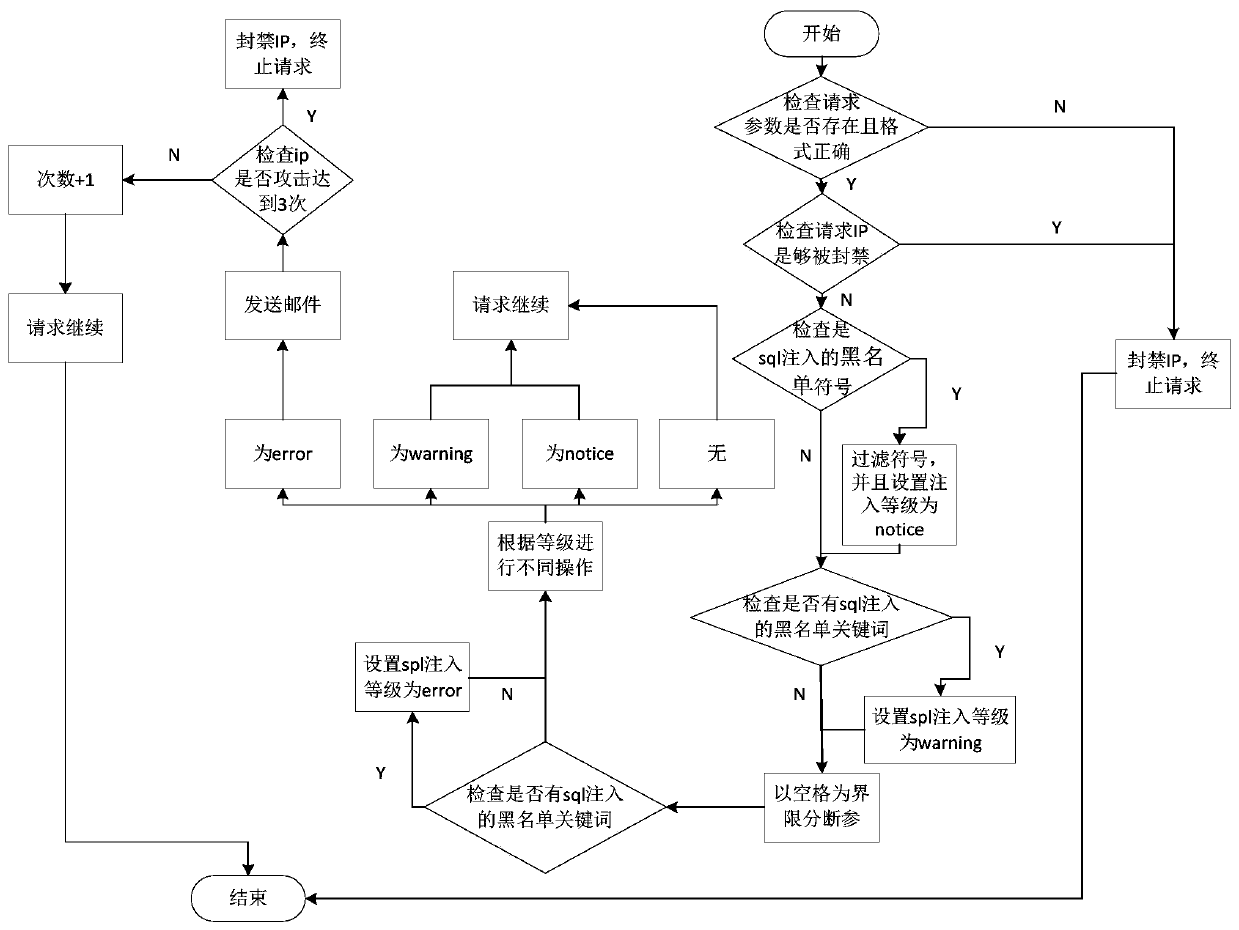
[0035] There are four problems addressed by the present invention: the first is the defense problem of sql injection; the second is the analysis and processing problem of sql injection attack; Knowing that the server has been attacked; the fourth solution is the low cost of sql injection and frequent attacks.
[0036] The proposal of the present invention aims at the above four problems, and designs a set of independent prevention system based on php.
[0037] To solve the first problem, this solution uses the first layer of blacklist get, post, and cookie parameter judgment and filtering, mainly filtering some commonly used injection punctuation marks, the second layer monitors sql injection keywords, and the third layer is Sentence analysis of parameters to avoid misjudgment.
[0038] For the second question, the parameters will be judged. If there is a problem with the first layer and the rest are OK, the rating will be notice. If the first and second layers have injected ...
Embodiment 2
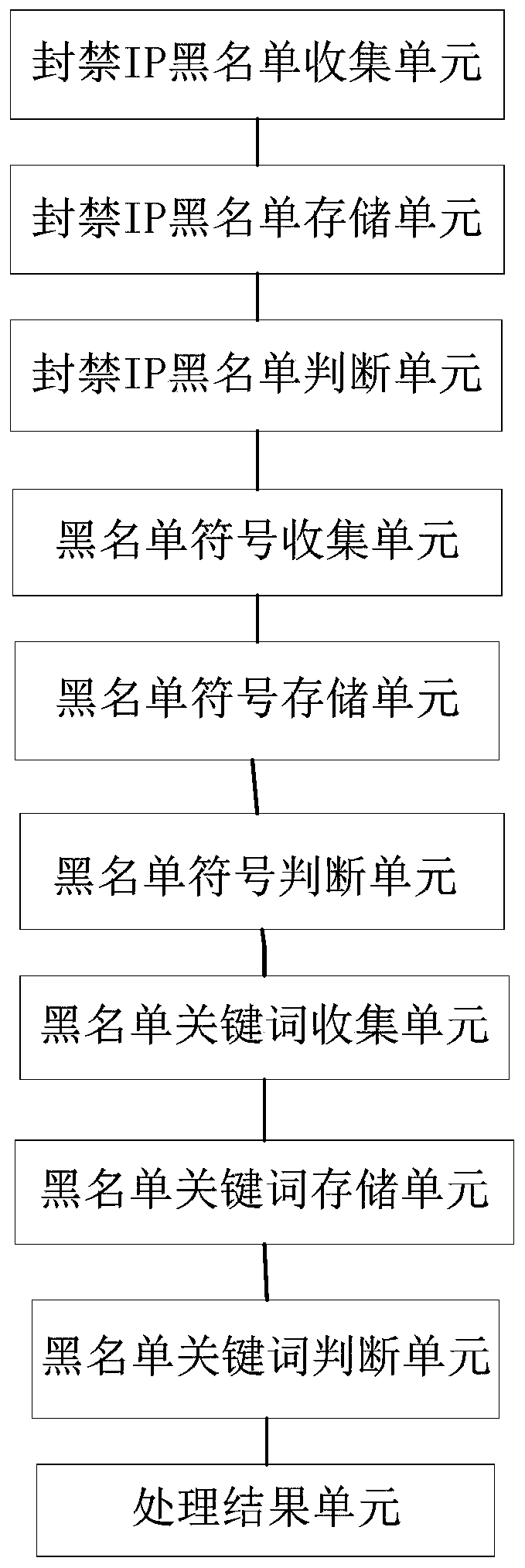
[0049] Such as figure 2 As shown, this embodiment provides a php-based independent sql injection defense analysis alarm system, including:
[0050] Banned IP blacklist collection unit, used to collect banned IPs for sql injection;
[0051] Banning the IP blacklist storage unit, used to store the collected banned IPs of sql injection;
[0052] Forbidden IP blacklist judging unit, is used for judging the request IP of sql injection, judges whether it is the banned IP in the described banned IP blacklist storage unit;
[0053] The blacklist symbol collection unit is used to collect blacklist symbols for sql injection;
[0054] The blacklist symbol storage unit is used to store the collected blacklist symbols of sql injection;
[0055] A blacklist symbol judging unit is used to judge the parameters of sql injection, whether the judgment parameter includes the blacklist symbol in the blacklist symbol storage unit, and the sql injection that includes the blacklist symbol is set ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com