Operation data safety assessment method, device, equipment and readable storage medium
A technology for operating data and security assessment, applied in the field of data security, can solve the problems of low accuracy of security assessment of operational data, less log information, and impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
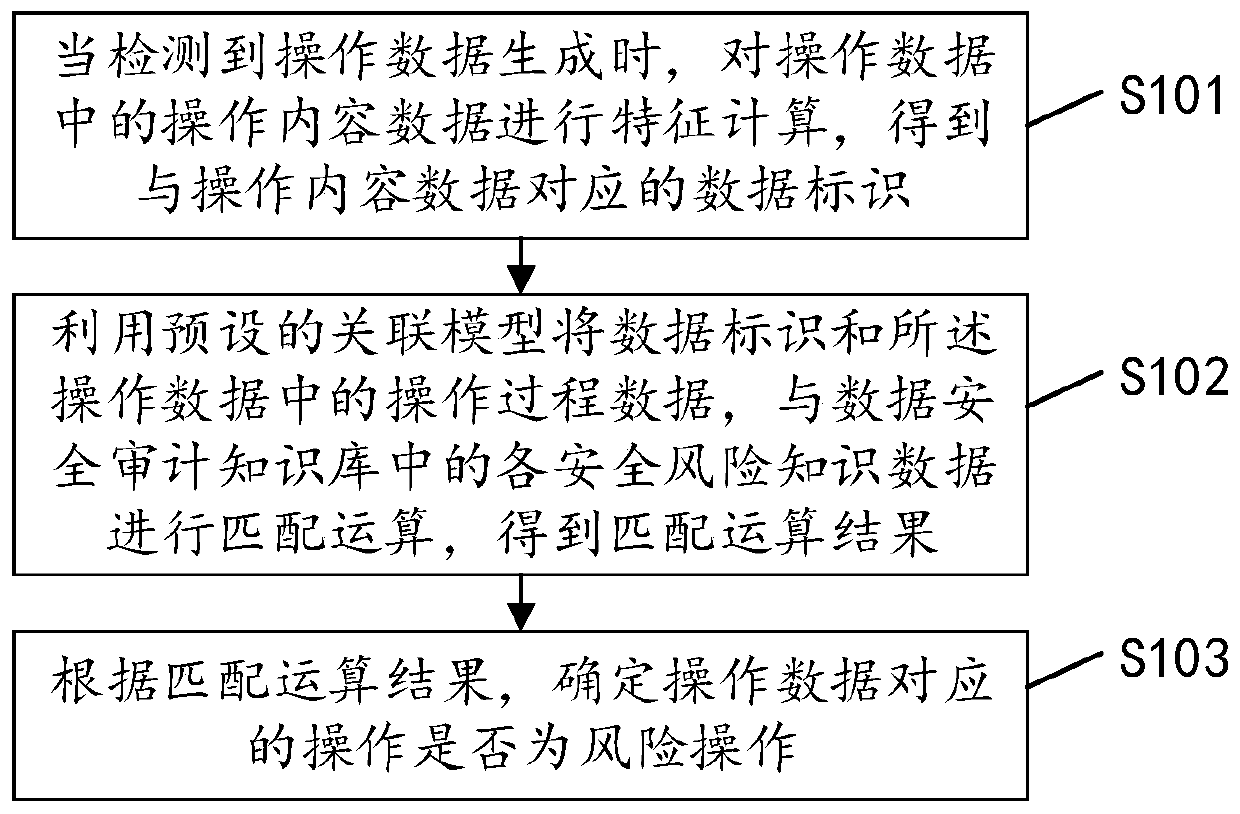
[0045] see figure 1 , figure 1 It is an implementation flowchart of the security assessment method for operating data in the embodiment of the present invention, and the method may include the following steps:
[0046] S101: When it is detected that the operation data is generated, perform feature calculation on the operation content data in the operation data to obtain a data identifier corresponding to the operation content data.
[0047] When the user operates the database, application system, and terminal (PC, server, etc.) of the computer system, corresponding operation data will be generated. When the generation of operation data is detected, the feature calculation is performed on the operation content data in the operation data to obtain the data identification corresponding to the operation content data, and the data identification can be recorded along with the log file. The operation data can include operation process data such as the operation user's IP, user nam...
Embodiment 2
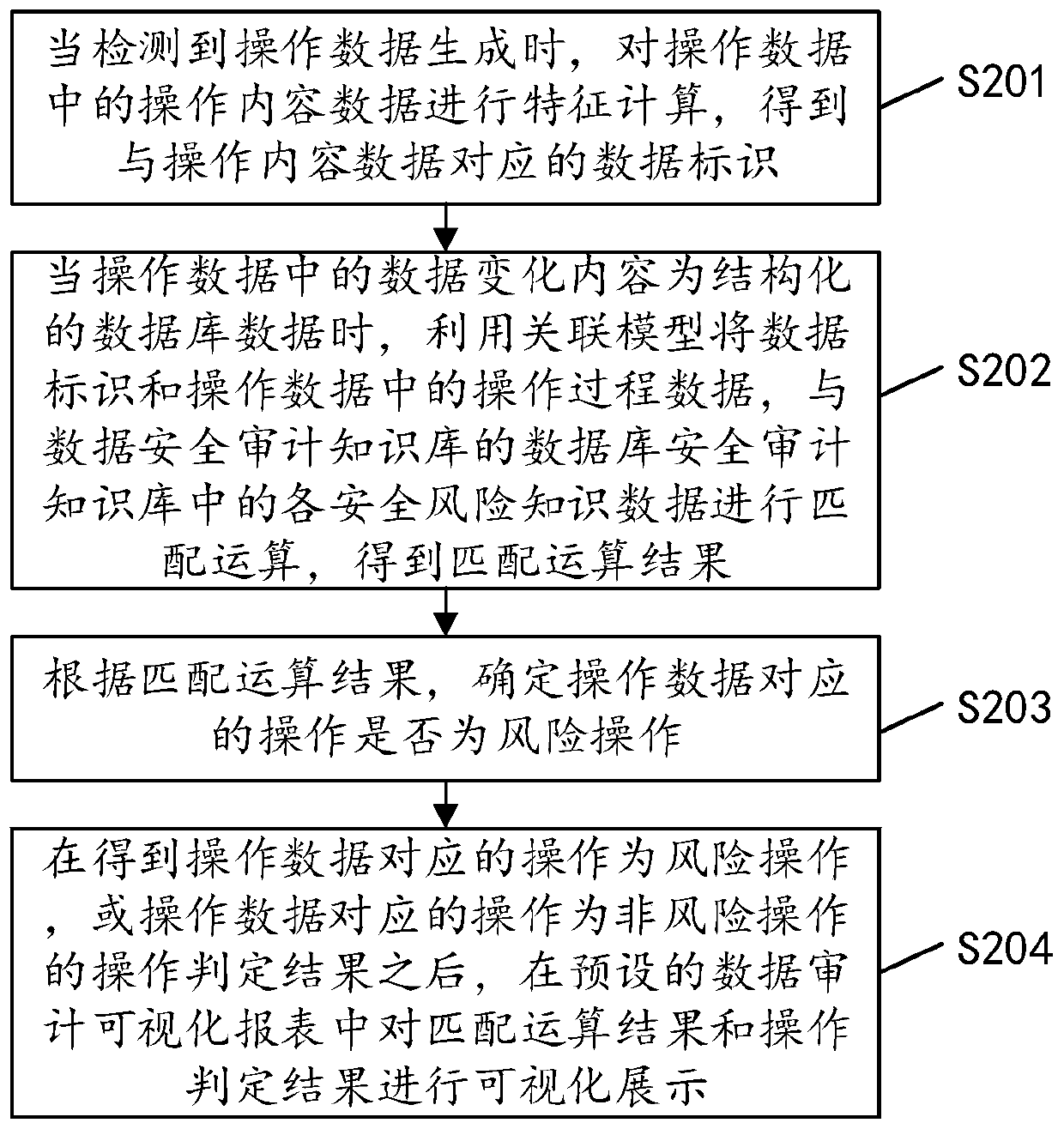
[0056] see figure 2 , figure 2 It is another implementation flowchart of the security assessment method for operating data in the embodiment of the present invention, and the method may include the following steps:
[0057] S201: When it is detected that the operation data is generated, perform feature calculation on the operation content data in the operation data to obtain a data identifier corresponding to the operation content data.
[0058] S202: When the data change content in the operation data is structured database data, use the association model to associate the data identification and operation process data in the operation data with each security risk in the database security audit knowledge base of the data security audit knowledge base Matching operation is performed on the knowledge data to obtain the matching operation result.
[0059] Among them, the data security audit knowledge base is obtained through artificial intelligence learning and training.
[0...
Embodiment 3
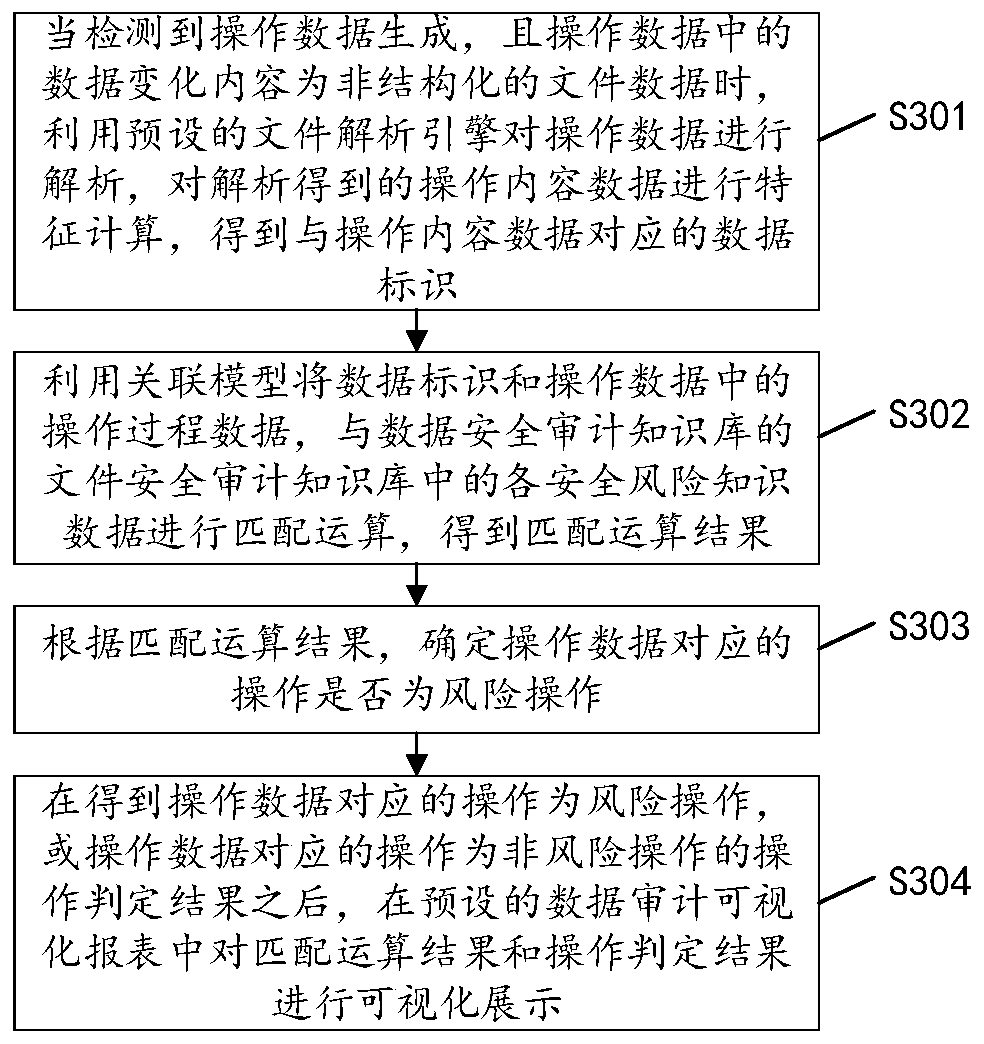
[0065] see image 3 , image 3 It is another implementation flowchart of the security assessment method for operating data in the embodiment of the present invention, and the method may include the following steps:
[0066] S301: When it is detected that the operation data is generated, and the data change content in the operation data is unstructured file data, use the preset file analysis engine to analyze the operation data, and perform feature calculation on the analyzed operation content data, Obtain the data identifier corresponding to the operation content data.
[0067] A file parsing engine for parsing unstructured file data can be set in advance. When it is determined that the content of data changes caused by user operations in the operation data is unstructured file data (such as PDF document data), the preset The file parsing engine parses the operation data, performs feature calculation on the parsed operation content data, and obtains a data identifier corresp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com