Encryption and decryption method for wireless communication, data transmission method and wireless communication system
A technology of wireless communication and encryption method, which is applied in the fields of wireless communication encryption and decryption, data transmission and wireless communication systems, which can solve problems such as increasing network burden, affecting encryption strength, and affecting transmission quality, so as to ensure security and reduce network burden , the effect of shortening the transmission time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
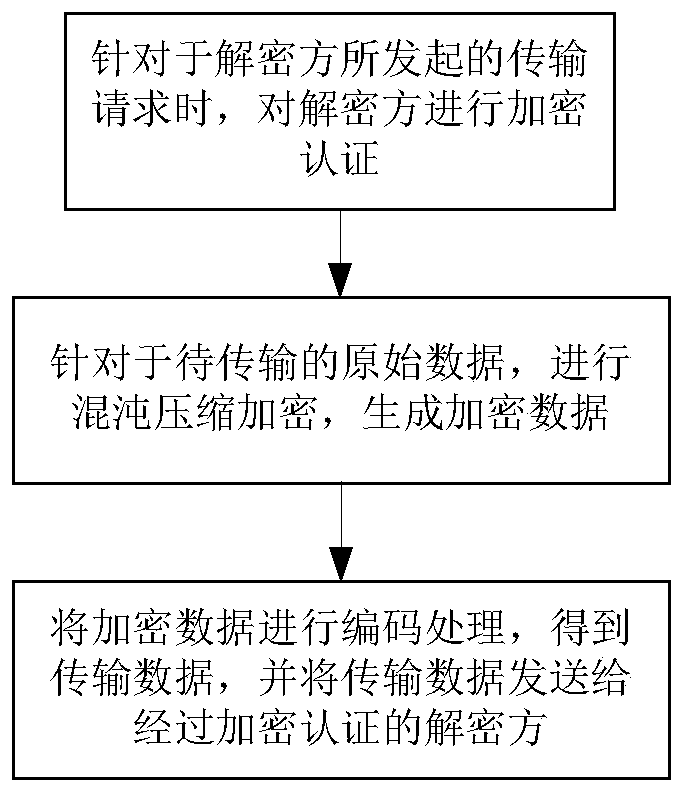
[0082] This embodiment discloses an encryption method for wireless communication, such as figure 1 As shown, the steps are as follows:
[0083] (1) For the transmission request initiated by the decrypting party, encrypt and authenticate the decrypting party, the process is as follows:
[0084] Step 1. For the received transmission request, extract a random number from the transmission request, and generate a random key according to the random number;
[0085] Step 2. Use the generated random key to initialize: Perform chaotic compression encryption on the random key. During the compression encryption process, count the number of occurrences of each character in the random key to obtain the random key. The probability of each character in the key appearing again;
[0086] Use the RSA encryption algorithm to encrypt the pre-stored encryption party authentication message and the random key generated by the random number to obtain the encrypted encryption party authentication me...
Embodiment 2
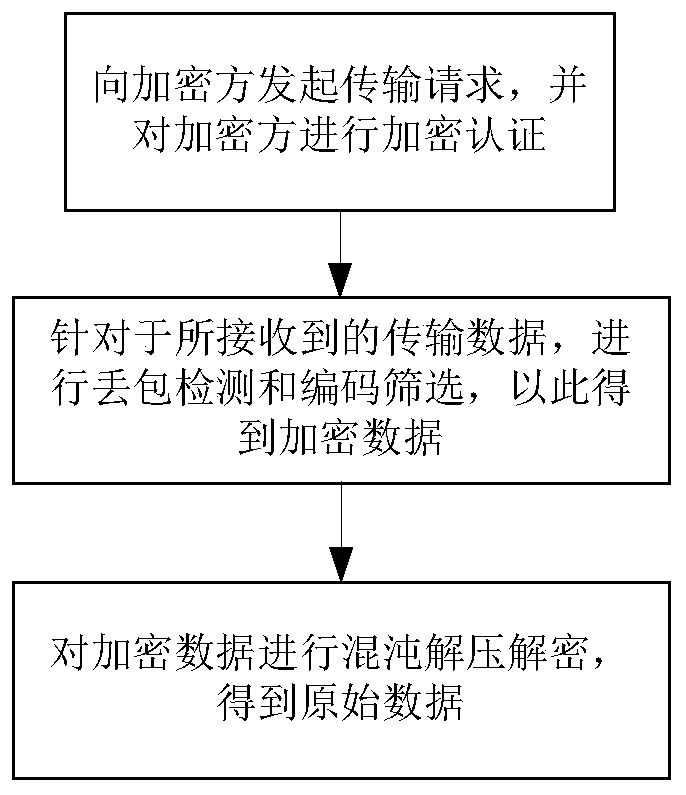
[0103] This embodiment discloses a wireless communication decryption method, such as figure 2 As shown, the steps are as follows:
[0104] (1) Initiate a transmission request to the encryption party, and perform encryption authentication on the encryption party. The encryption authentication process is as follows:
[0105] Step 1. After receiving the encrypted authentication message from the encryption party, use the preset RSA key to decrypt the encryption party authentication message encrypted by the RSA encryption algorithm, and obtain the decrypted encryption party authentication message and random key ;
[0106] Step 2. Initialize with a random key: Perform chaotic compression encryption on the random key. During the process of compression and encryption, count the number of occurrences of each character in the random key to obtain the The probability of each character appearing again;
[0107] Verify the decrypted encryption party authentication message, and perform ...
Embodiment 3
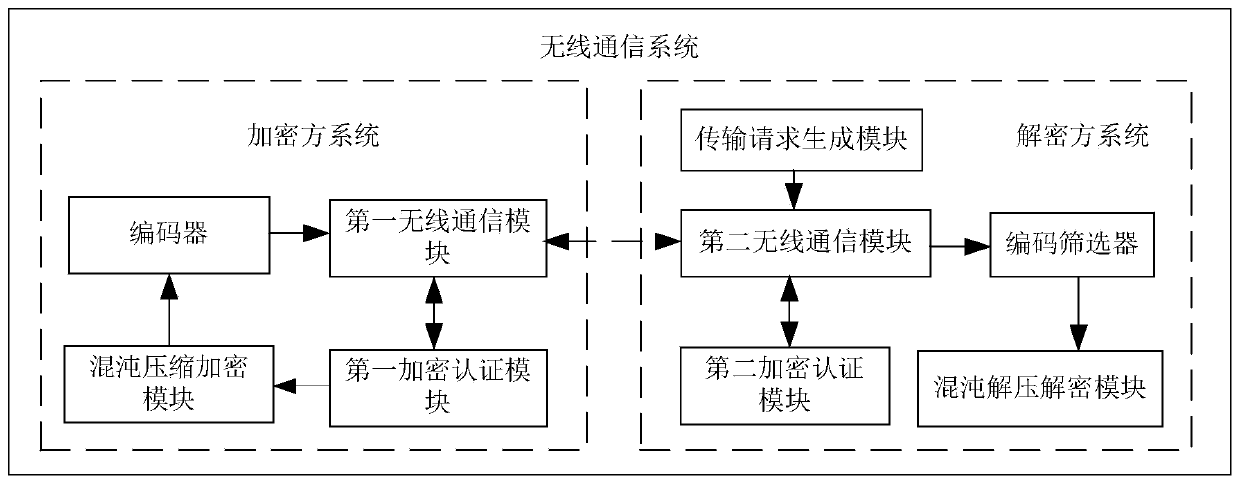
[0124] This embodiment discloses a data transmission method for wireless communication, the steps are as follows:
[0125] Step S1, the decryption party initiates a transmission request to the encryption party, and after the encryption party receives the transmission request initiated by the decryption party, encryption authentication is performed between the encryption party and the decryption party;
[0126] Among them, the encryption authentication process is as follows:
[0127] Step S11, the encrypting party extracts a random number from the received transmission request, and generates a random key according to the random number;
[0128] Step S12, the encryption party uses the generated random key to initialize: perform chaotic compression encryption on the random key, and in the process of compression encryption, count the number of occurrences of each character in the random key to obtain the probability of each character in the random key appearing again;
[0129] T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com