Network behavior risk perception and defense method based on behavior characteristic big data analysis
A risk perception and big data technology, applied in the field of network security, can solve the problems that affect the security and reliability of network data communication, low efficiency of network data risk information monitoring, low monitoring accuracy and efficiency, etc., to eliminate threats to network security Data dissemination, good system expansion ability, and the effect of improving work efficiency and quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to make the technical means, creative features, achievement goals and effects realized by the present invention easy to understand, the present invention will be further described below with reference to the specific embodiments.
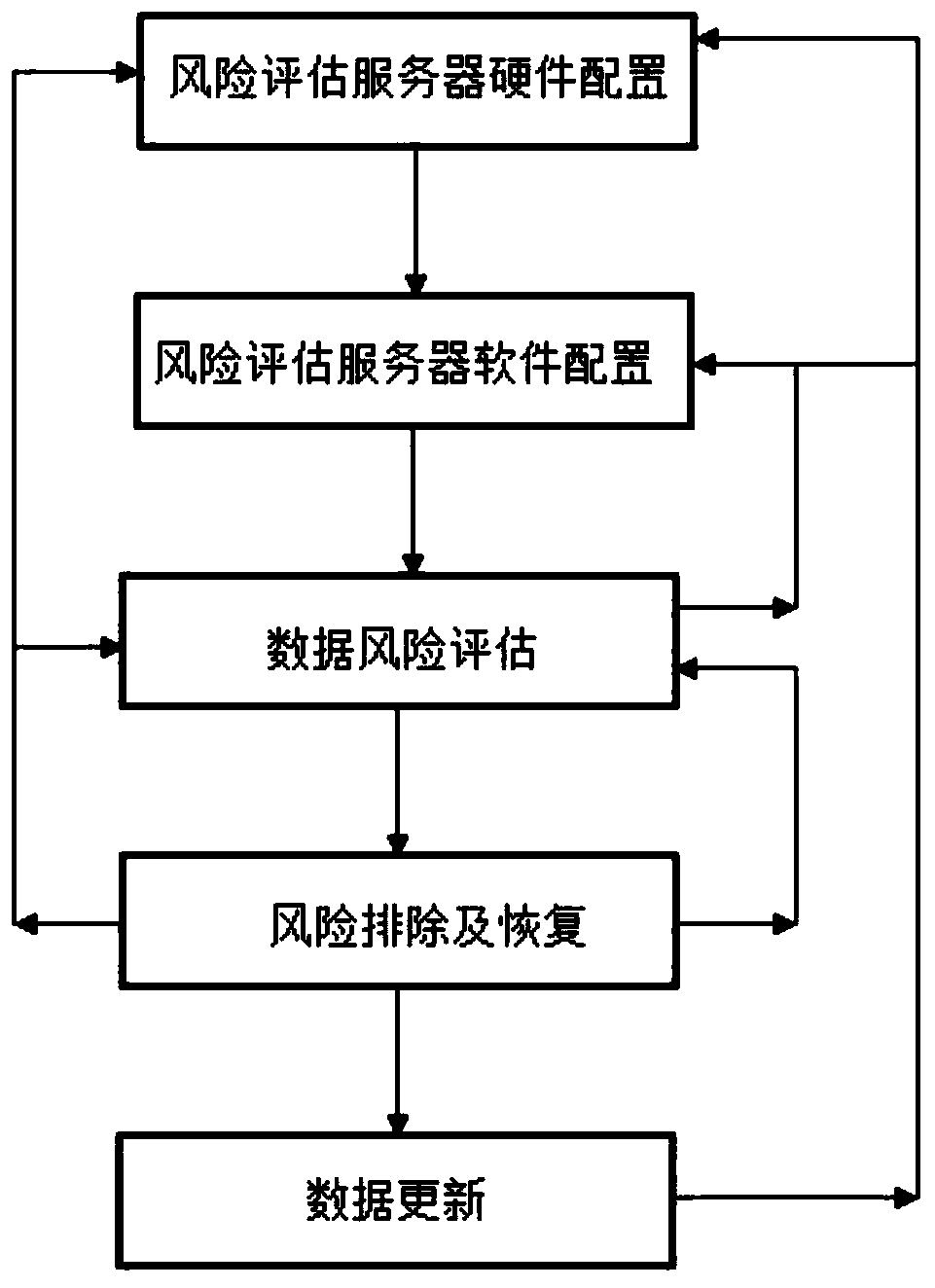
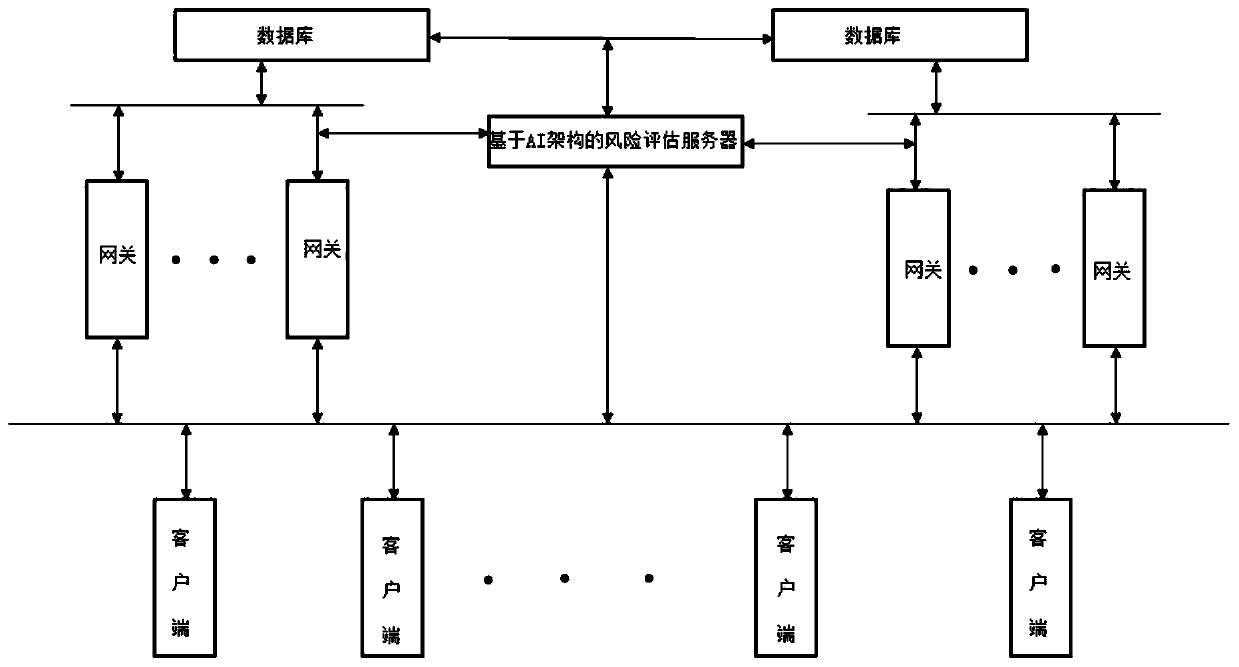
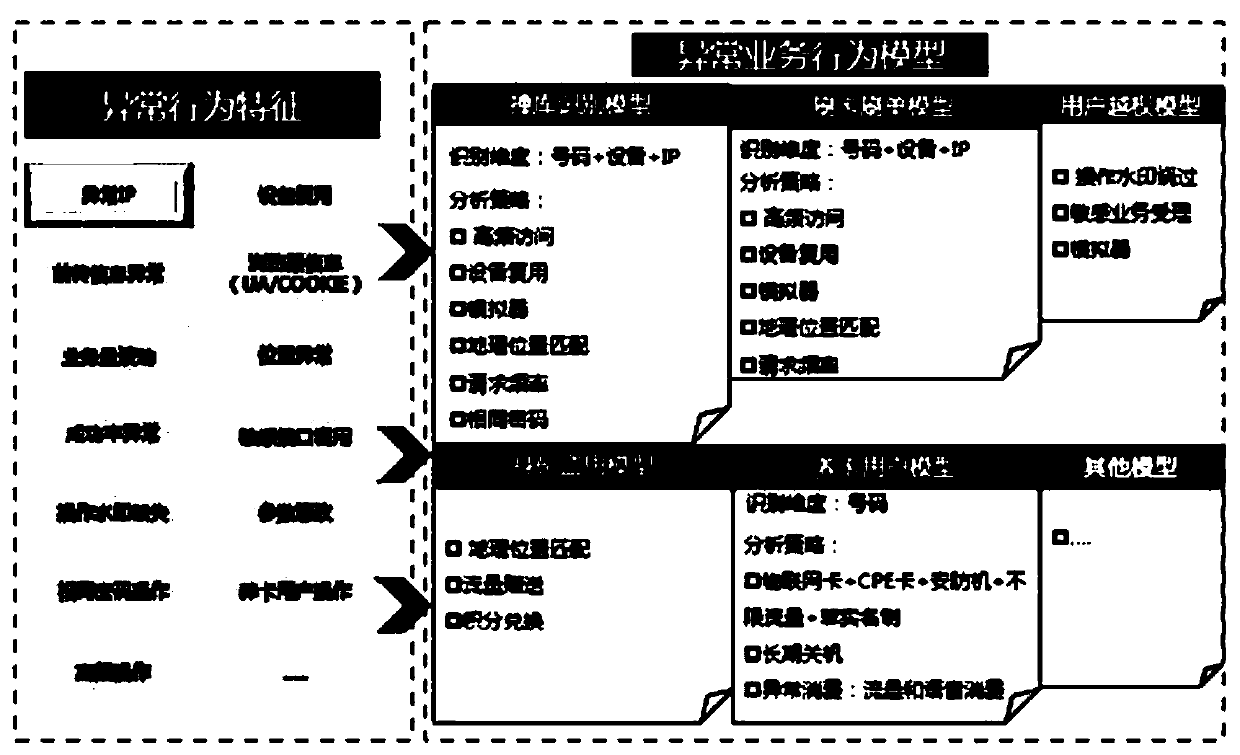
[0023] like figure 1 -4 Network behavior risk perception and defense method based on behavioral feature big data analysis, including the following steps:
[0024]S1. The hardware configuration of the risk assessment server. First, according to the TCP / IP communication protocol parameters, network structure type, database structure type and client distribution method of the specified network to be protected, set up a risk assessment server based on AI architecture and at least one other The risk assessment control terminal connected between the AI architecture-based risk assessment servers connects the AI architecture-based risk assessment server to each database, gateway and client of the designated network to be protected throug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com