Trusted data collection method based on node trust value virtual force
A data collection and trust value technology, applied in wireless communication, security devices, network traffic/resource management, etc., can solve the problems of fast node energy consumption, limited communication ability and energy, and high delay, so as to achieve reliable guarantee and reduce node energy The effect of consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
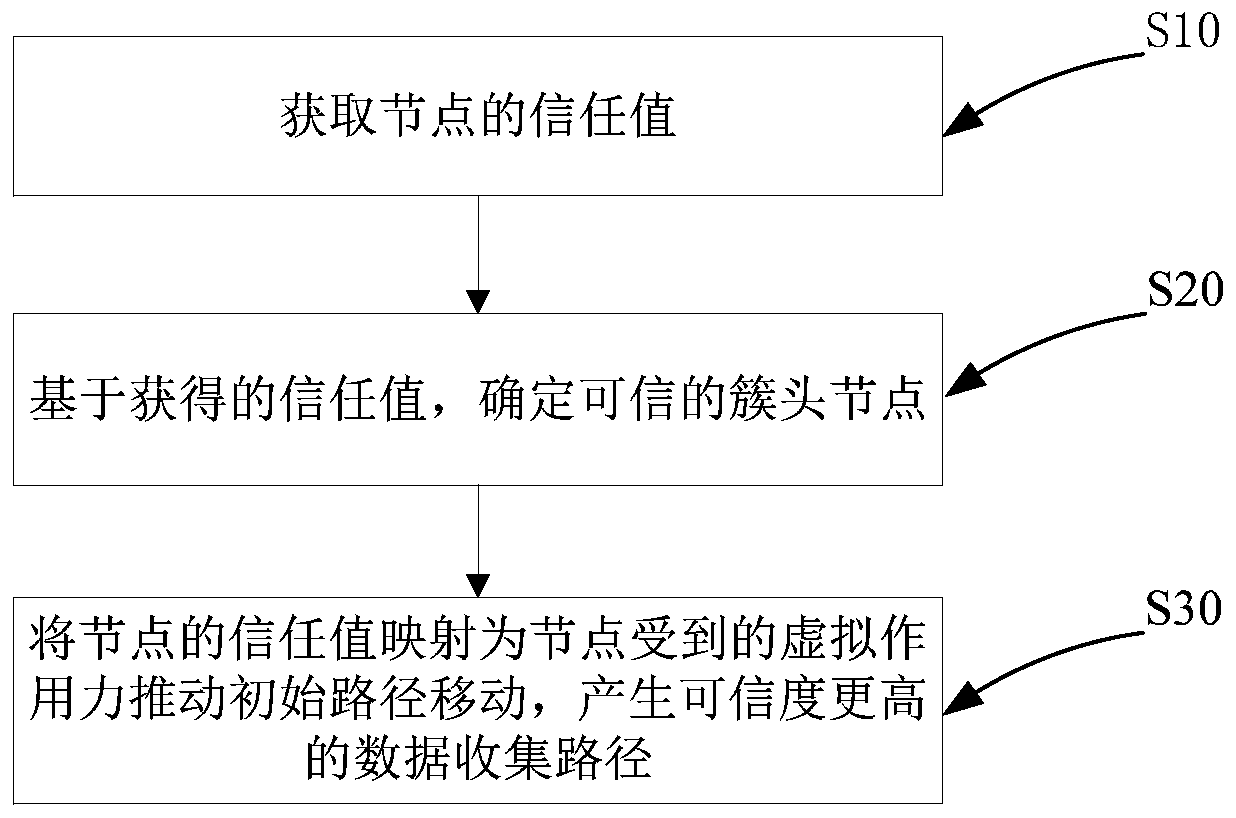
[0061] The technical solutions in the embodiments of the present invention will be described and discussed in detail below in conjunction with the drawings of the present invention. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
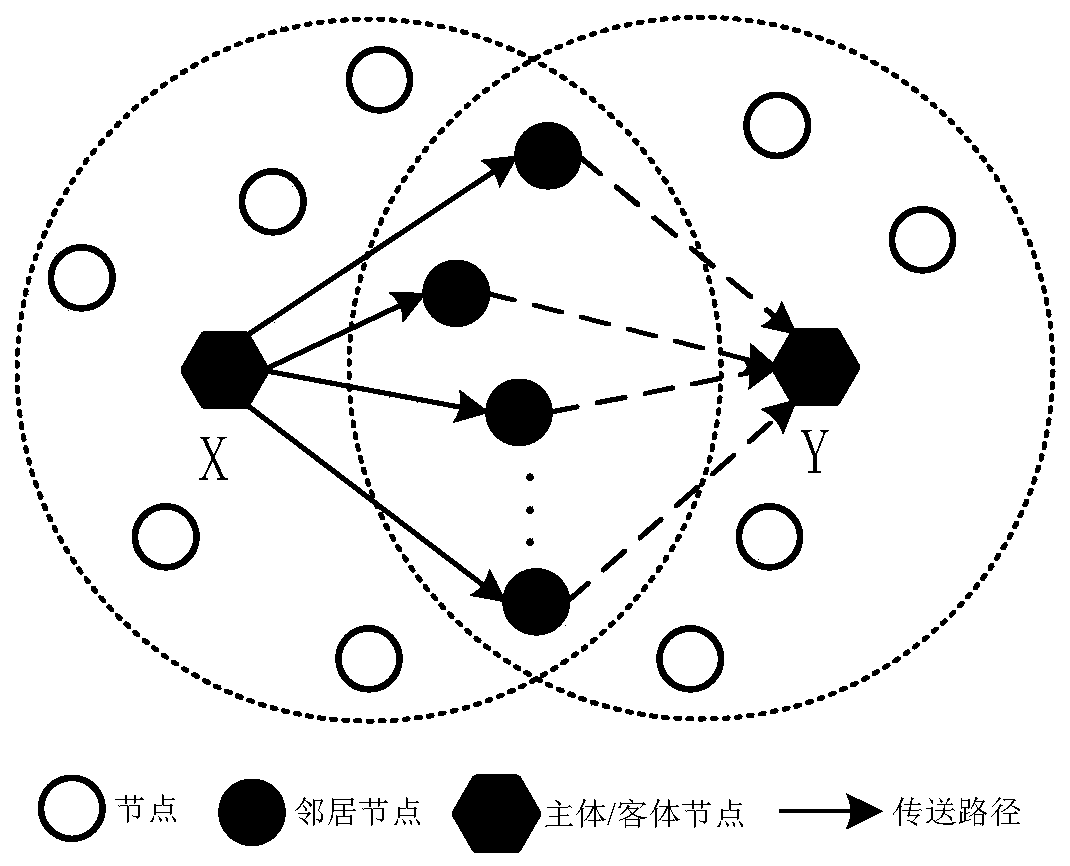
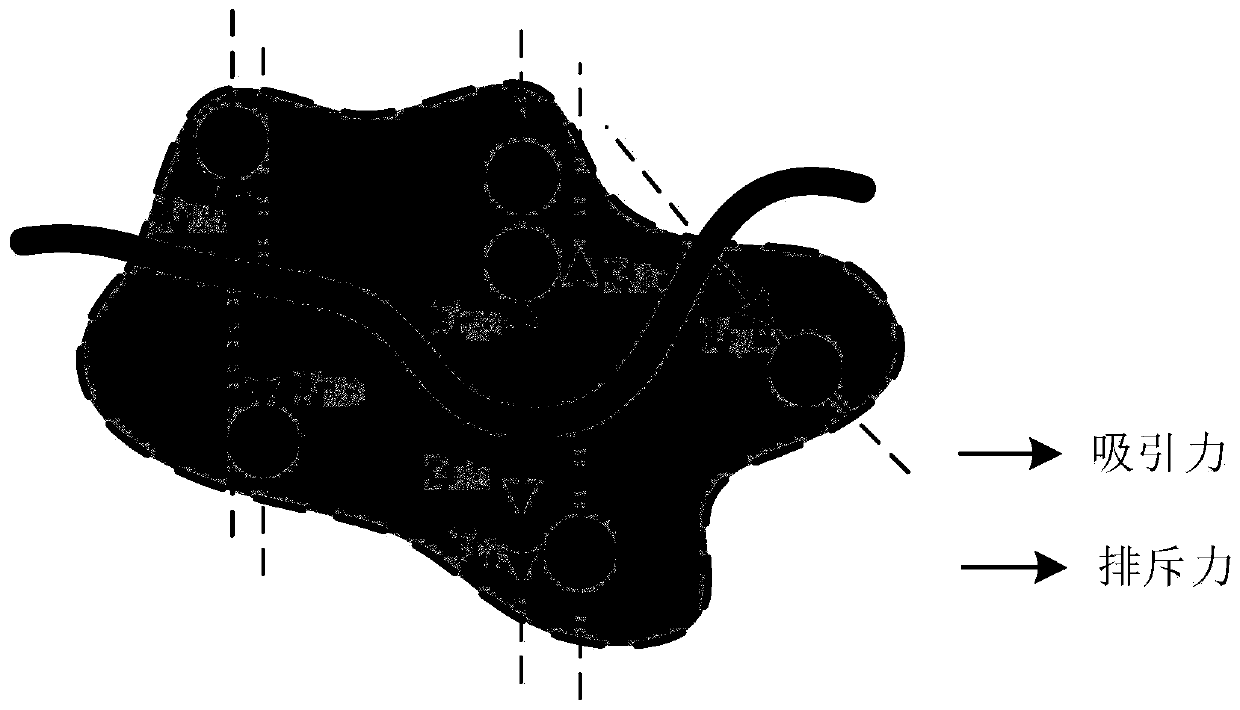
[0062] In the application of the data collection of the Internet of Things, the present invention first designs a node trust evaluation algorithm (such as direct trust and indirect trust) according to the relationship between nodes, and calculates the quantitative trust value of the node by the existing algorithm. The trust value of the node is mapped to the physical force on the node, and the trusted node is given an attractive force, and the untrusted node is repelled. The initial path of movement is simulated as a soft rope with magnetism, and the initial path moves under the joint force of the nodes, finally generating a credible data collect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com