Electronic identity authentication method, apparatus and device, and storage medium
An authentication method and electronic identity technology, which is applied in the field of security authentication, can solve the problems of cumbersome operation, weak implementation, and low security, and achieve the effect of protecting private information, improving security, and making small changes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
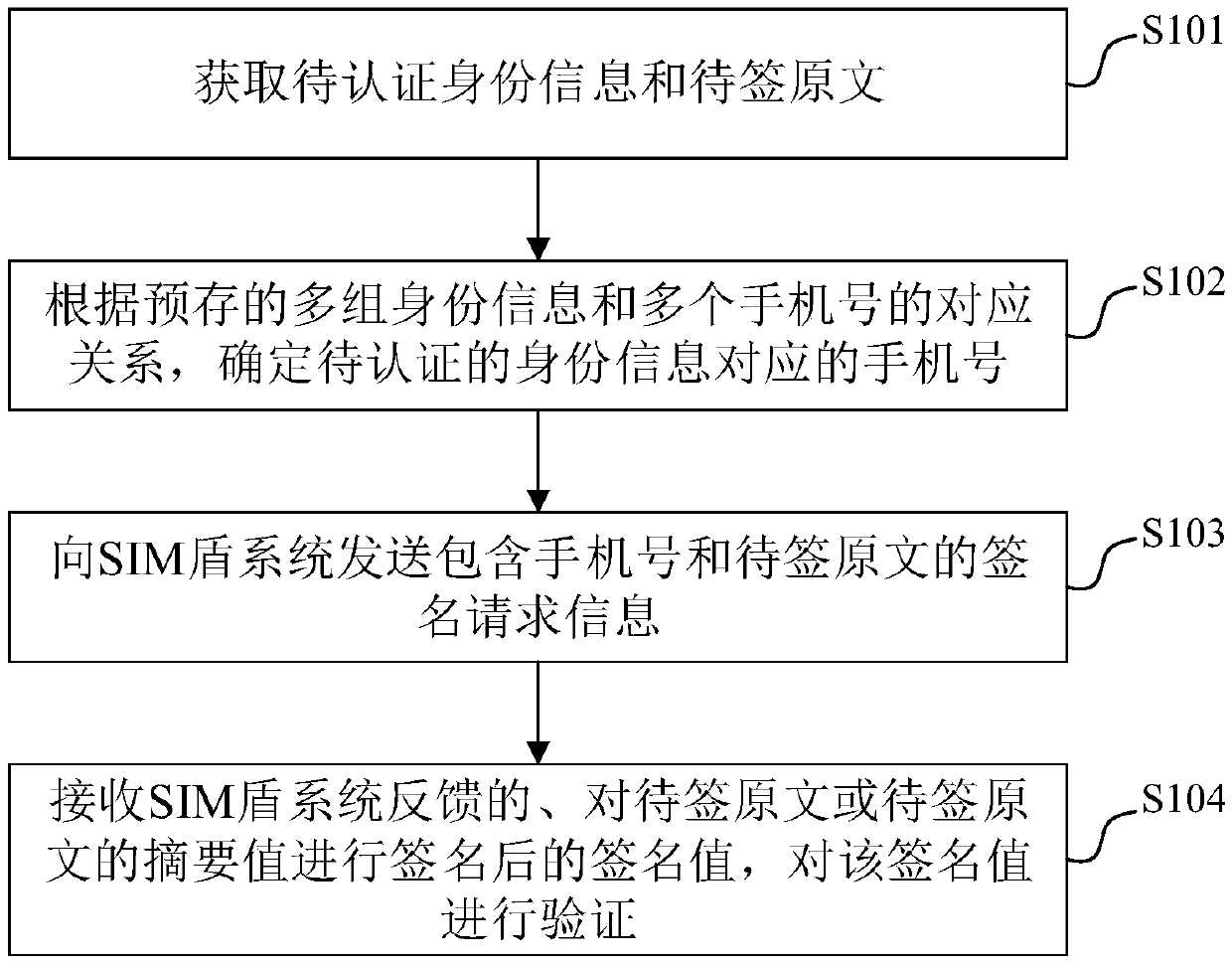
[0035] The embodiment of this application provides an electronic identity authentication method, the schematic flow chart of the authentication method is as follows figure 1 shown, including:
[0036] S101. Obtain the identity information to be authenticated and the original text to be signed.
[0037] Optionally, obtain the real-name authentication request including the identity information to be authenticated and the original text to be signed.
[0038] In an optional implementation manner, the identity information to be authenticated includes name and ID number.
[0039] In another optional embodiment, the identity information to be authenticated includes name, ID number and SIM (Subscriber Identification Module, user identification card) card unique identification information; wherein the SIM card unique identification information can be IMSI (International Mobile Subscriber Identification Number, International Mobile Subscriber Identity).
[0040] S102. Determine the m...
Embodiment 2
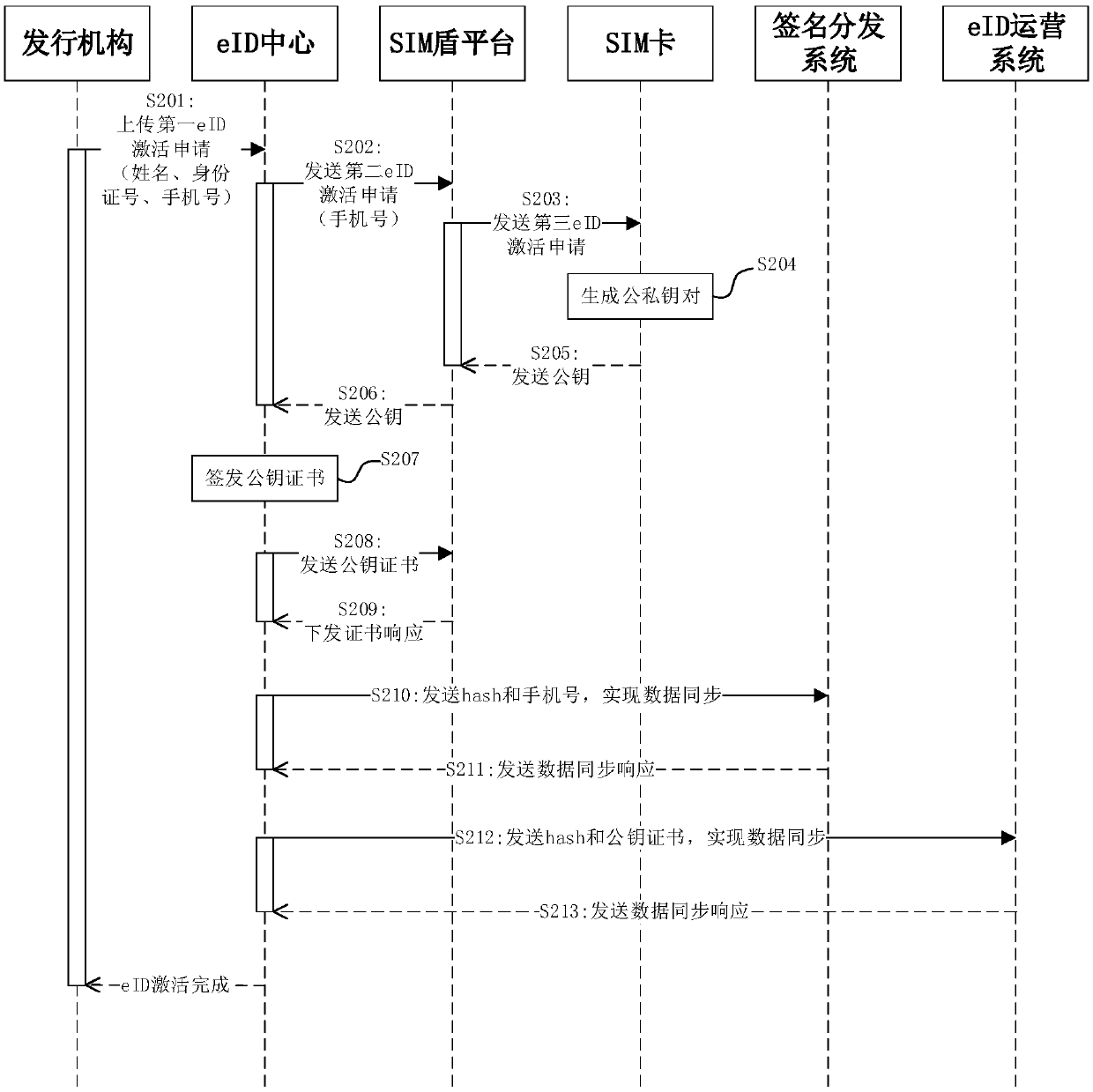
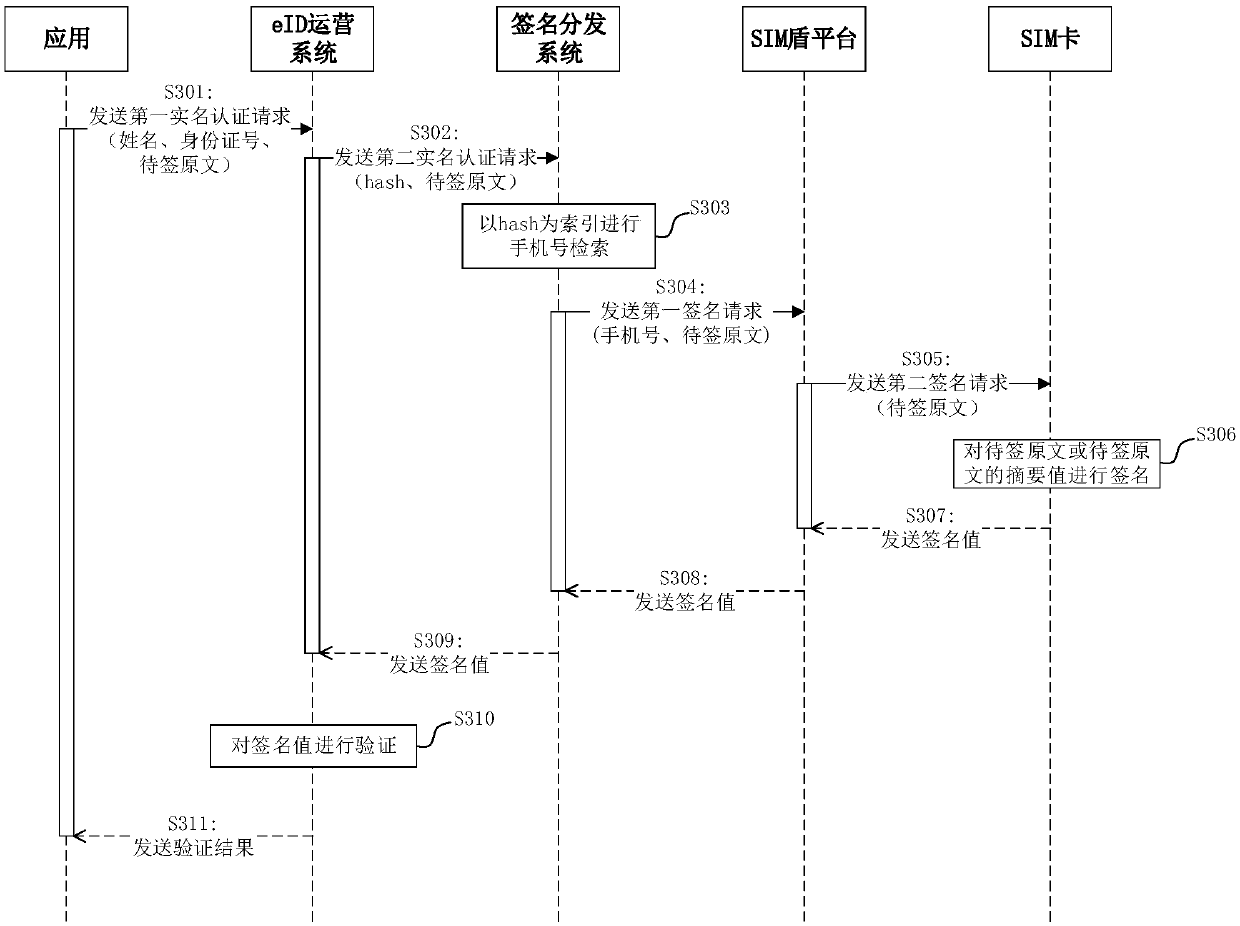
[0124] Based on the same inventive concept, the embodiment of this application provides an electronic identity verification device, the structural framework of the device is shown in Image 6 As shown, it includes: an information acquisition module 601 , a mobile phone number determination module 602 , a signature request module 603 and a signature verification module 604 .
[0125] The information obtaining module 601 is used to obtain the identity information to be authenticated and the original text to be signed.
[0126] The mobile phone number determination module 602 is configured to determine the mobile phone number corresponding to the identity information to be authenticated according to the correspondence between multiple sets of pre-stored identity information and multiple mobile phone numbers.
[0127] The signature request module 603 is configured to send signature request information including the mobile phone number and the original text to be signed to the SIM ...
Embodiment 3
[0139] Based on the same inventive concept, the embodiment of this application provides an electronic identity authentication device, such as Figure 8 as shown, Figure 8 The illustrated electronic identity authentication device 800 includes: a memory 801 and a processor 802 , and the memory 801 is electrically connected to the processor 802 .
[0140] The memory 801 in the embodiment of the present application stores a computer program, and the computer program is executed by the processor 802 to implement the authentication method provided in Embodiment 1 of the present application.
[0141] The memory 801 in the embodiment of the present application may be a ROM (Read-Only Memory, read-only memory) or other types of static storage devices that can store static information and instructions, and may be a RAM (Random Access Memory, random access memory) or Other types of dynamic storage devices that can store information and instructions can also be EEPROM (Electrically Eras...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com