Electric power material coding optimization method based on hash algorithm
An electric power material and hash algorithm technology, which is applied in the field of power material coding optimization based on hash algorithm, can solve the problems of limited information connection, inconsistent coding form, and no effective combination of materials, etc., and achieves high security strength and good The effect of anti-attack ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
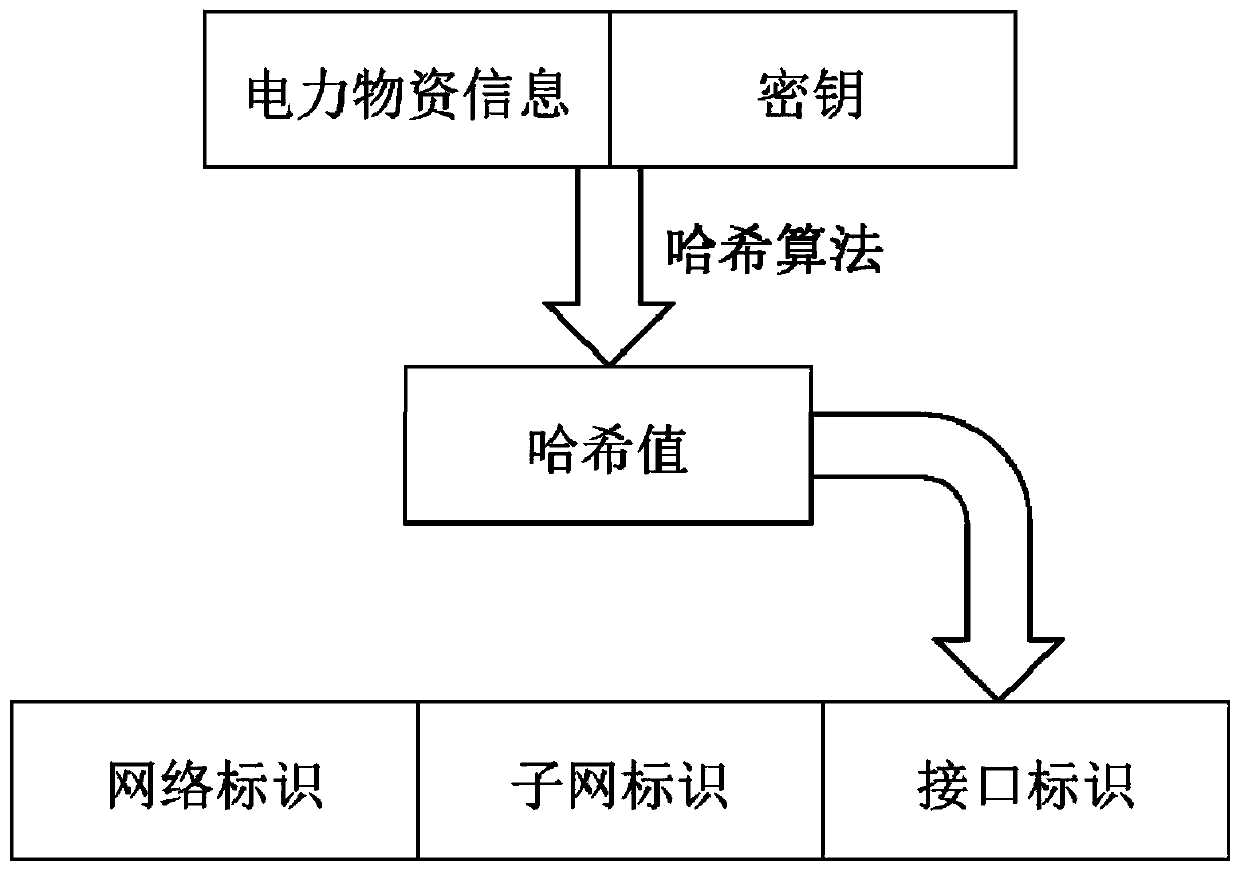
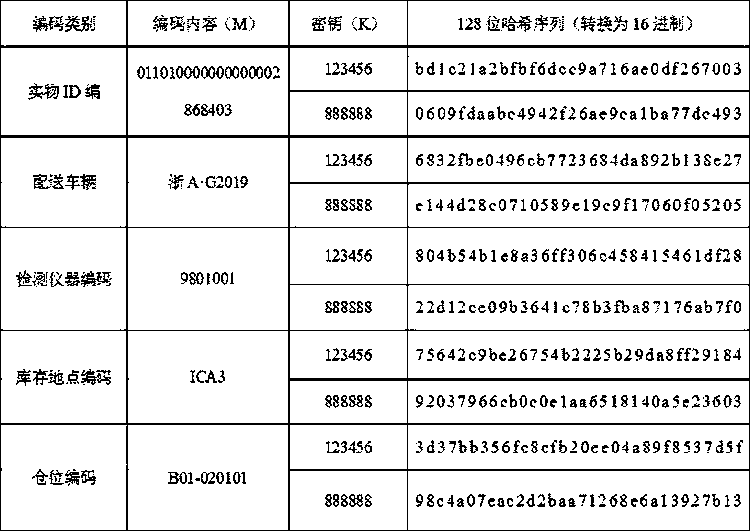
[0056] A power material coding optimization method based on hash algorithm, HMAC based on Hash algorithm, its security strength is much higher than that of Hash algorithm, using the HMAC-MD5 algorithm constructed on the basis of MD5 message digest algorithm, the key and message Data mixing, using a hash function to hash the result of the mixing, mixing the resulting hash value with the key, and then applying the hash function again. HMAC-MD5 accepts keys of any size and generates hash sequences of length 128 bits.
[0057] The description of the HMAC-MD5 algorithm is as follows:
[0058] HMAC(K,M)=H(K⊕opad‖H(K⊕ipad‖M))
[0059] K: key; M: message content; H: hash function, the hash function selects MD5; opad and ipad: strings composed of several 0x5c and 0x36 respectively; ⊕: XOR operation; ‖: connection operation .
[0060] The process steps are as follows:
[0061] Step 1: Add 0 after the key K to create a string of length B;
[0062] Step 2: XOR the string generated in...
Embodiment 2
[0076] A fusion method based on the encoding method of the HMAC-MD5 algorithm and the IPv6 address, and the IPv6 address includes a global network identifier, a local subnet identifier, and a host identifier, and the host identifier includes an HMAC-MD5 algorithm-based The encoding generated by the encoding method.
[0077] IPv6 is the abbreviation of "Internet Protocol Version 6" (Internet Protocol Version 6) in English. It is designed by the Internet Engineering Task Force (IETF) to replace IPv4 and become the basic communication protocol of the next generation Internet [13].
[0078]The text representation of IPv6 is also determined in RFC5952[14]. IPv6 addresses are usually expressed in hexadecimal form with colons, that is, x:x:x:x:x:x:x:x, each x is in hexadecimal Represents a 16-bit long integer, and the letters inside are expressed in lowercase. It includes a 48-bit global network identifier, a 16-bit local subnet identifier, and a 64-bit host identifier. The last 48-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com